Support Questions
- Cloudera Community
- Support
- Support Questions
- Ambari Fails to create Keytabs when Installing new...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Ambari Fails to create Keytabs when Installing new services or when trying to regenerate keytabs of existing services
- Labels:
-
Apache Ambari
Created on 01-03-2019 02:21 PM - edited 09-16-2022 07:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
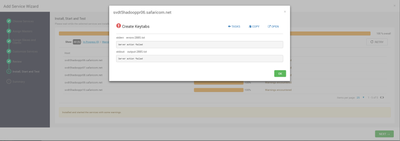
I am getting a server action failed error when ambari tries to create keytabs. I have no idea what is causing this error. I am using KDC admin to install the service. Please help. @Geoffrey Shelton Okot
Created 01-16-2019 11:57 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There seems to be a mismatch between the Active Directory encryption type and the MIT encryption types can you align the 2 supported_enctypes to be the same.
Windows supports the below encryption types depending on the Windows version which are weak encryption
DES_CBC_CRC DES_CBC_MD5 RC4_HMAC_MD5 AES128_HMAC_SHA1 AES256_HMAC_SHA1
In your kdc.conf you have stronger encryption types you validate the AD encryption types? Else try to comment out the kdc.conf encryptions see below
# supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal camellia256-cts:normal camellia128-cts:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal
and see whether the error persists?
Created 01-03-2019 02:57 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you take a look at your Ambari server log (/var/log/ambari-server/ambari-server.log) and see if there are any interesting error messages?
Created 01-03-2019 05:00 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the HDP version? The screenshot doesn't look a typical MIT Kerberos enabling UI? Could you be using the AD as KDC? Having said that can you share how you procedure used? Can you share the Kerberos enabling screenshots from Ambari?
If you could answer promptly with the above info then it would help a great deal.
HTH
Created on 01-04-2019 06:46 AM - edited 08-17-2019 03:12 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The screenshot shared previously was of Ambari UI when adding hbase as a service.
Kerberos is MIT and was working fine when initially enabled. I realized there was a problem when adding a new service to the cluster. Ambari creates the principles needed in the kerberos db but is unable to create the keytabs.
HDP version is 3.0.0.0-1634
Ambari Version 2.7.1.0
The procedure i used was the one in the guidelines of ambari using an exsisting MIT kerberos. It works fine until you try and add a new service or regenerate keytabs for an existing service.
@Robert Levas There are no error messages in the logs that say anything.
Created 01-04-2019 02:15 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
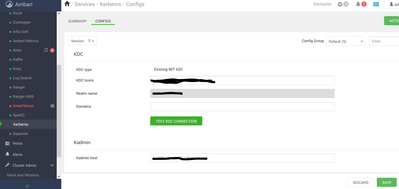
At least I am reassured about the previous screenshot. From the screenshot, I don't see domain which should be in the format and comma separated if your REALM is TEST.COM note the dot(.)
.test.com,test.com
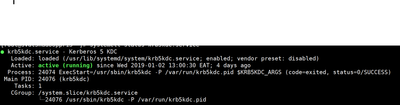
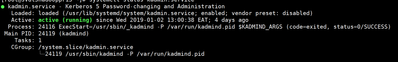
And the Kadmin too, meanwhile can you share a tokenized version of you krb5.conf,kdc.conf and kadm5.acl most important ensure these 2 daemons are running
Enable auto start
# systemctl enable krb5kdc # systemctl enable kadmin
Start the daemons
# /etc/rc.d/init.d/krb5kdc start # /etc/rc.d/init.d/kadmin start
or
# systemctl start krb5kdc # systemctl start kadmin
Whichever is applicable
HTH
Created 01-04-2019 02:35 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is the Ambari server on a host that is registered with the cluster? If not, I was recently alerted to an issue where this case was causing an error. But enabling Kerberos would have failed for you... unless you had enabled Kerberos before upgrading to Ambari 2.7.1. See AMBARI-25088 - Enable Kerberos fails when Ambari server is not on a registered host.
Created 01-07-2019 08:43 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Robert Levas the server is on the same domain. Kerberos is ok. the only issue is generation of keytabs when I add a new service. The principals are also created it just fails at keytab generation.
Created 01-05-2019 10:39 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Created 01-05-2019 10:41 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@huzaira bashir
Please follow the steps and update this thread, I am sure there is a step you missed follow page by page. On your screenshot I didn't see the Domain
Created on 01-07-2019 08:41 AM - edited 08-17-2019 03:12 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi have done everything accordingly, the domain is defined in the krb5.conf file. The ACL file is also ok.
my process are running as expected. the only problem is Ambari is not able to generate keytabs. Like I said, Ambari creates the principals required in the kerberos db but is unable to generate keytabs..
I can run Kadmin and list the princs.