Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: Level 2: Enabling Cloudera Manager Agent Hosts...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Level 2: Enabling Cloudera Manager Agent Hosts to Authenticate the Server's Certificate ---Fails !
- Labels:
-
Cloudera Manager
Created on
12-18-2019
07:59 AM
- last edited on
12-18-2019
01:08 PM
by
ask_bill_brooks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ,
I am running free trial cloudera in pseudo-distributed mod (One host, the server and agent are the same).i am trying now to enable tls/ssl for my cluster
-Level 1 succedeed https://datastore.xxx.fr:7183 tuns correctly with no problem
When i configure level N2 of tls/ssl ,cloudera manager agent fails to connect !.
In CM server fails to have heartbeat:
when i checked :tail -f /var/log/cloudera-scm-agent/cloudera-scm-agent.log
I got ERROR :
File "/opt/cloudera/cm-agent/lib/python2.7/site-packages/M2Crypto/SSL/Connection.py", line 292, in connect_ssl
return m2.ssl_connect(self.ssl, self._timeout)
SSLError: certificate verify failed
The agent config files :
server_host=datastore.xxx.fr
server_port=7182
# Use TLS and certificate validation when connecting to the CM server.
use_tls=1
max_cert_depth=9
verify_cert_file=/opt/cloudera/security/x509/cmhost.pem
---the cmhost.pem get my certifcate correctly
---when i run :
sudo openssl s_client -connect datastore.xxx.fr:7182 < /opt/cloudera/security/x509/cmhost.pem
i got :
CONNECTED(00000003)
depth=2 O = Digital Signature Trust Co., CN = DST Root CA X3
verify return:1
depth=1 C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3
verify return:1
depth=0 CN = xxx.fr
verify return:1
---
Certificate chain
0 s:/CN=xxx.fr
i:/C=US/O=Let's Encrypt/CN=Let's Encrypt Authority X3
1 s:/C=US/O=Let's Encrypt/CN=Let's Encrypt Authority X3
i:/O=Digital Signature Trust Co./CN=DST Root CA X3
........
........
Verify return code: 0 (ok)
---
DONE
?
Created 12-19-2019 07:48 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ,
When i passed to level3 .all seems good and well-configured .
The error is not been re-showen again .
Thanks.
Created 12-18-2019 02:07 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
We no longer refer to levels in our documentation but based on what is posted here it would appear as though are on Step 4 of our current documentation for manual certificate configuration. While we understand that you might not be able to provide the full raw contents of your certificate in this forum please ensure that the certificates you are attempting to use have the following two x509 Extended Key Usage attributes. These 2 EKUs must be present in order to use Client/Server Authentication which is the final step of deployment should you chose to go that far. These two EKUs are noted in our documentation.
X509v3 Extended Key Usage:
TLS Web Client Authentication
TLS Web Server Authentication
https://docs.cloudera.com/documentation/enterprise/6/6.3/topics/how_to_configure_cm_tls.html#topic_3
https://docs.cloudera.com/documentation/enterprise/6/6.3/topics/how_to_configure_cm_tls.html
Also please make sure that there are no leading or trailing spaces on any configuration parameters within the agent configuration file. If your certificate is non-single root, signed by an intermediate, you may have better success using the verify_cert_dir parameter so that all of your CA certificates including the root certificate are present. When using the verify_cert_dir parameter you must use c_rehash provided by openssl-perl.
Customer Operations Engineer | Security SME | Cloudera, Inc.
Created 12-19-2019 03:28 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ,
Thanks for your support and all cloudera team.
i resolved that by ,adding my rootca to my cloudera keystore and trustore .Then i reconfigured the agent config.ini to point to the rootca.pem .
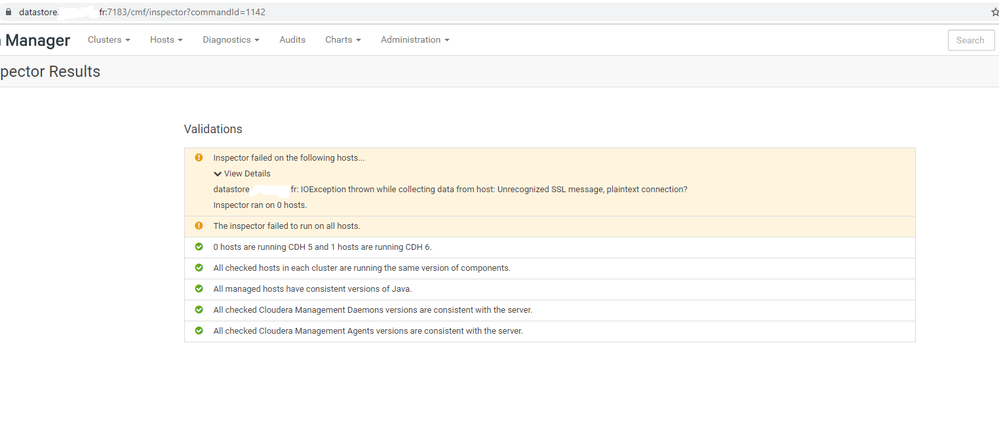
But when i inspect host i got this error .(i am using cdh 6.1.1 on ubuntu 16.04)
Created 12-19-2019 07:04 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Take a look at the Agent configuration on the reported host and make sure that use_tls is set to 1 and not 0. This error usually happens when Cloudera Manager expects TLS from the agent (Based on enabled options
) but the agent is continuing to send data using clear text. If the parameter is set to 1 please restart the agent to ensure that it is set properly.
The agent performs multiple task some of these task are performed with data transmitted through the heartbeat others are handled by a pull method through the agent.
Customer Operations Engineer | Security SME | Cloudera, Inc.
Created 12-19-2019 07:48 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ,
When i passed to level3 .all seems good and well-configured .
The error is not been re-showen again .
Thanks.