Community Articles
- Cloudera Community
- Support
- Community Articles
- Configuring Ranger Usersync with AD/LDAP for a com...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on 05-31-2017 06:24 PM
Configuring Ranger Usersync with AD/LDAP is highly dependent on the customer environment. This requires understanding of the customer environment as well as the specific requirements for syncing users and groups.
In order to get some background on User management in Hadoop, please refer to this Dataworks Summit Presentation. Corresponding slides are available at: Slides
In this article we will take a common use case and see how Ranger Usersync can be configured in that scenario. Ranger Usersync supports various configuration options with AD/LDAP and details are available here
Use case: Sync all the users who are members of a specific group(s)
This use case can be handled in multiple ways and is also based on the AD/LDAP attributes available in the server. In case of Active Directory, users contain information of the group(s) they belong to using the “memberof” attribute. Similarly groups contain information about the user(s) that belong to them using the “member” attribute. Whereas in default installation of openLdap server doesn’t contain “memberof” attribute for the user. So the only way to retrieve user that belong to a group is by using “member” attribute of the group.
Let’s take an example in Active directory where we want to sync all the users that belong to groups - “hdp_testing”, “hdp_admin”, or “dev_ops”
------------------------------------------------------------------------------------------
Sample ldapsearch command to search a particular group (hdp_testing) and determine what attributes are available for the group:
ldapsearch -x -LLL -h 10.10.10.10:389 -D 'cn=administrator,CN=Users,dc=hortonworks,dc=com' -W -b 'ou=Hadoop Groups,dc=hortonworks,dc=com' 'cn=hdp_testing’
Enter LDAP Password:
dn: CN=hdp_testing,ou=Hadoop Groups,dc=hortonworks,dc=com
objectClass: top
objectClass: group
cn: hdp_testing
member: CN=test11 test,ou=Hadoop Users,dc=hortonworks,dc=com
member: CN=user12 user,ou=Hadoop Users,dc=hortonworks,dc=com
member: CN=user8 user,ou=Hadoop Users,dc=hortonworks,dc=com
member: CN=user7 user,ou=Hadoop Users,dc=hortonworks,dc=com
member: CN=user6 user,ou=Hadoop Users,dc=hortonworks,dc=com
member: CN=user1 user,ou=Hadoop Users,dc=hortonworks,dc=com
distinguishedName: CN=hdp_testing,ou=Hadoop Groups,dc=hortonworks,dc=com
instanceType: 4
uSNChanged: 1312771
name: group5
sAMAccountName: hdp_testing
sAMAccountType: 222431111
Above output shows all the available attributes for hdp_testing. Note:- Highlighted are the attributes that are interested for usersync configuration.
In this case hdp_testing has multiple members (highlighted “member” attribute) like
member: CN=test11 test,ou=Hadoop Users,dc=hortonworks,dc=com
member: CN=user12 user,ou=Hadoop Users,dc=hortonworks,dc=com
member: CN=user8 user,ou=Hadoop Users,dc=hortonworks,dc=com
member: CN=user7 user,ou=Hadoop Users,dc=hortonworks,dc=com
etc…
Sample ldapsearch command to search a particular user (user8) and determine what attributes are available for the user:
ldapsearch -x -LLL -h 10.10.10.10:389 -D 'cn=administrator,CN=Users,dc=hortonworks,dc=com' -W -b 'ou=Hadoop Users,dc=hortonworks,dc=com' 'samaccountname=user8'
Enter LDAP Password:
dn: CN=user8 user,ou=Hadoop Users,dc=hortonworks,dc=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: user8 user
sn: user
givenName: user8
distinguishedName: CN=user8 user,ou=Hadoop Users,dc=hortonworks,dc=com
instanceType: 4
memberOf: CN=hdp_testing,ou=Hadoop Groups,dc=hortonworks,dc=com
memberOf: CN=dev_ops,ou=Hadoop Groups,dc=hortonworks,dc=com
memberOf: CN=test_groups,ou=Hadoop Groups,dc=hortonworks,dc=com
memberOf: CN=security_groups,ou=groups,dc=hortonworks,dc=com
uSNChanged: 973651
userAccountControl: 512
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 0
primaryGroupID: 513
logonCount: 0
sAMAccountName: user8
Above output shows all the available attributes for a user. Note:- Highlighted are the attributes that are interested for usersync configuration.
In this case user8 is a “memberof” 4 groups - hdp_testing, dev_ops, test_groups, and security_groups
As you can see, users from hdp_testing, dev_ops, or hdp_admins can be sync’d to ranger by performing
- a user search using the “memberof” attribute in the user search filter -- User based search
or
- a group search using the “member” attribute -- Group based search
Ranger Usersync configuration contains three sets of configuration:
- Common Configs: Ldap Url and bind credentials
- User Configs: Attributes related to user like sAMAccountName, OU(s) of the users, user search filter, memberof, etc…
- Group Configs: Attributes related to group like sAMAccountName, OU(s) of the groups, group search filter, member, etc…
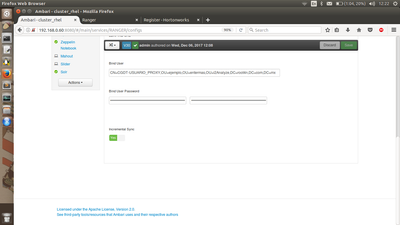
Following is the screenshot of the Common Configs properties configured for the above example:
Please note the following:
- From HDP 2.6 onwards Ranger Usersync supports “Incremental Sync” and is enabled by default.
- For clusters that are upgraded from older version to 2.6, “Incremental Sync” is disabled.
- When “Incremental sync” is enabled, “Enable Group Sync” is set to “true” by default and the properties under “Group Configs” is mandatory.
Configuring Ranger Usersync for User based search:
============================================
Here Users are searched based on the attributes available from the user attribute and group information is available as part of the “memberof”. In this case two main parts that need to be configured in Ranger Usersync configuration are the properties under - “Common Configs” and “User Configs”. Optionally properties under “Group Configs” can be configured in cases where customers want to limit or filter the groups that these users belong to. As you can see in the above example, user8 belongs to 4 groups - hdp_testing, dev_ops, test_groups, and security_groups. But if we are interested only in groups hdp_testing and dev_ops, then “Group Configs” properties can be set accordingly.
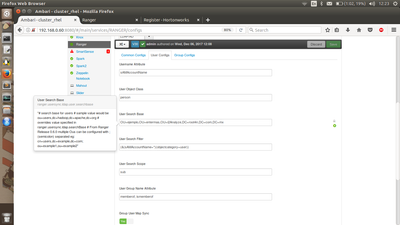
Following are the screenshots of User Configs and Group Configs properties configured for the above example with User based search:
User Configs:
-------------------------------
Group Configs:
-------------------------------
Configuring Ranger Usersync for Group based search:
============================================
In this case Ranger Usersync performs group search first based on the group configuration. Here users are searched based on the attributes available from the group attributes and user information is available as part of the “member”. In this case two main parts that need to be configured in Ranger Usersync configuration are the properties under - “Common Configs” and “Group Configs”. Optionally properties under “User Configs” can be configured in cases where customers want to limit or filter the users that belong to these groups.
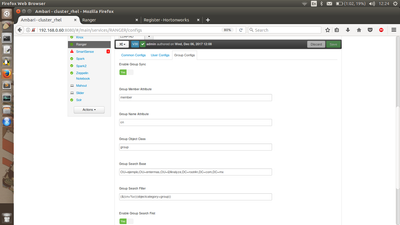
Following are the screenshots of Group Configs, and User Configs properties configured for the above example with Group based search:
Group Configs:
-------------------------------
Note:- “Enable Group First Search” must be set to “true” in order to perform Group based search.
User Configs:
-------------------------------
Please note the following:
- “Enable User Search” is set to false by default.
- When “Enable User Search” is set to “false”
- none of the properties under “User Configs” will be used by Ranger Usersync
- Users are sync’d using group’s member attribute which in many cases contains CN (Firstname Lastname) of the user.
- In order to sync users using sAMAccountName, then “Enable User Search” must be set to “true” and “Username Attribute” must be set to “sAMAccountName”.
Note:- With “Enable User Search” set to true, it is still required to set all other user configs appropriately like the user search base and user object class. User search filter can be set to “sAMAccountName=*”
Created on 06-01-2017 08:39 PM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Nice and descriptive article @spolavarapu, keep it up !!!
Created on 12-07-2017 06:11 PM - edited 08-17-2019 12:43 PM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello spolavarapu,
I've been trying to sync users from an AC into my Ranger following your tutorial and I haven't been able to get the correct user id through the sAMAccountname attribute, instead, the attribute that is synchronized is the long name, which happens to be the cn too. Any ideas? I attach some of the screen shots from my AC, Ranger configs and the results.
Thanks!
AC
Ranger Configs
Here the fields username and CN are the same
06 dic 2017 12:26:54 INFO LdapDeltaUserGroupBuilder [UnixUserSyncThread] - longUserName: CN=RPM-ROBERTO_PAZ,OU=ejemplo,OU=entermas,OU=i2Analyze,DC=root4n,DC=com,DC=mx, userName: RPM-ROBERTO_PAZ
Created on 12-07-2017 06:29 PM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This issue is fixed as part of https://issues.apache.org/jira/browse/RANGER-1632
Created on 05-03-2021 06:14 AM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
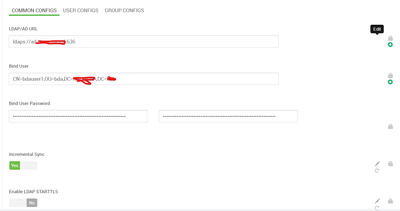
Hi @spolavarapu ,
I have followed your steps but still not able to sync AD users & groups ,please find details below for config and could you please suggest any solution here.

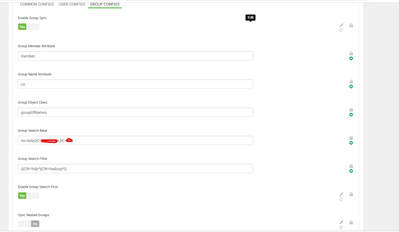
Created on 05-03-2021 09:32 AM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @somesh, as this is an older post, you would have a better chance of receiving a resolution by starting a new thread. This will also be an opportunity to provide details specific to your environment that could aid others in assisting you with a more accurate answer to your question. You can link this thread as a reference in your new post.
Created on 05-03-2021 10:01 AM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@VidyaSargur Thanks, will open a new thread.