Community Articles
- Cloudera Community
- Support
- Community Articles
- NiFi Composite Authorization - LDAP and File - Usi...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on 08-19-2019 03:23 PM - edited 08-20-2019 10:26 AM
This article describes the configuration of the authorizers.xml for using the Composite User Group Provider for both LDAP and File based authentication in Cloudera Manager for CDF 1.0
This article assumes TLS has already been configured for NiFi using either the NiFi CA or your own certs.
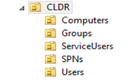
Here is the Active Directory Structure that I will use for my sync:
Here are the groups in the Groups OU:
Here are the users in the Users OU:
Here are the service users in the ServiceUsers OU:
First, I will import my Active Directory root certificate into the NiFi and Java Truststores:
keytool -import -file adcert.pem -alias ad -keystore /var/lib/nifi/cert/truststore.jks
keytool -import -file adcert.pem -alias ad -keystore /etc/pki/java/cacerts
Now login to Cloudera Manager and proceed to the NiFi Configuration.
Update the configuration to use the "composite-user-group-provider" as follows:
xml.authorizers.accessPolicyProvider.file-access-policy-provider.property.User Group Provider=composite-user-group-provider
Next, use the "NiFi Node Advanced Configuration Snippet (Safety Valve) for staging/authorizers.xml" and add the following configurations using the XML view:
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.class</name>
<value>org.apache.nifi.ldap.tenants.LdapUserGroupProvider</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.Manager DN</name>
<value>CN=ldapbind-svc,OU=ServiceUsers,OU=CLDR,DC=nismaily,DC=com</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.Manager Password</name>
<value>hadoop</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.Referral Strategy</name>
<value>FOLLOW</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.Connect Timeout</name>
<value>10 secs</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.Read Timeout</name>
<value>10 secs</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.Url</name>
<value>ldaps://win-ltfjo4jgo4r.nismaily.com:636</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.Sync Interval</name>
<value>15 mins</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.User Search Base</name>
<value>OU=Users,OU=CLDR,DC=nismaily,DC=com</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.User Object Class</name>
<value>user</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.User Search Scope</name>
<value>SUBTREE</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.User Identity Attribute</name>
<value>sAMAccountName</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.User Group Name Attribute</name>
<value>memberof</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.Group Search Base</name>
<value>OU=Groups,OU=CLDR,DC=nismaily,DC=com</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.Group Object Class</name>
<value>group</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.Group Search Scope</name>
<value>SUBTREE</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.Group Name Attribute</name>
<value>cn</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.Group Member Attribute</name>
<value>member</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.composite-user-group-provider.class</name>
<value>org.apache.nifi.authorization.CompositeConfigurableUserGroupProvider</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.composite-user-group-provider.property.Configurable User Group Provider</name>
<value>file-user-group-provider</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.composite-user-group-provider.property.User Group Provider 1</name>
<value>ldap-user-group-provider</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.Authentication Strategy</name>
<value>LDAPS</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.TLS - Keystore</name>
<value>/var/lib/nifi/cert/keystore.jks</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.TLS - Keystore Password</name>
<value>hadoop</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.TLS - Keystore Type</name>
<value>jks</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.TLS - Truststore</name>
<value>/var/lib/nifi/cert/truststore.jks</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.TLS - Truststore Password</name>
<value>hadoop</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.TLS - Truststore Type</name>
<value>jks</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.TLS - Client Auth</name>
<value>WANT</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.TLS - Protocol</name>
<value>TLSv1.2</value>
</property>
<property>
<name>xml.authorizers.userGroupProvider.ldap-user-group-provider.property.TLS - Shutdown Gracefully</name>
<value>false</value>
</property>
Restart NiFi and login to the NiFi UI.
Proceed to the Users Tab:
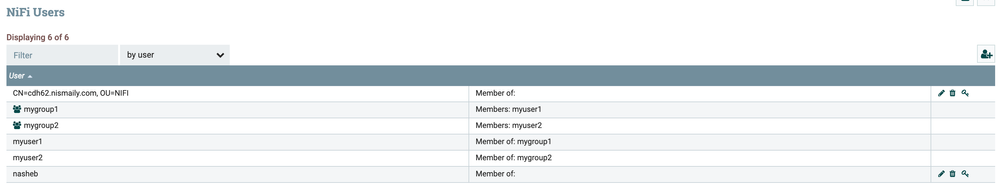
You will see the users synced from Active Directory: