Support Questions
- Cloudera Community
- Support
- Support Questions
- How to give permissions to users to access Nifi UI...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to give permissions to users to access Nifi UI through Ranger policy
- Labels:
-
Apache NiFi
-
Apache Ranger
Created on 10-27-2017 02:14 PM - edited 08-17-2019 05:56 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
How to give permissions to users to access Nifi UI through Ranger policy?
Scenario of the setup:
1. Versions used - Nifi 1.2.0, Ranger 0.7.0
2. Cluster setup of Nifi through Ambari.
3. Ranger is authenticated with LDAP. Created Ranger policy to access Nifi UI.
4. Nifi UI is accessible through LDAP users.
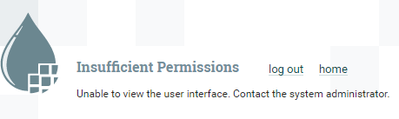
I wanted to give permissions to users to access Nifi UI. When I'm giving specific LDAP user in a policy I won't able to login Nifi UI. I get below message from Nifi UI.
Not authorized for the requested resource. Contact the system administrator.
From Nifi Logs
NiFi Web Server-8342] o.a.n.w.a.c.AccessDeniedExceptionMapper cn=rverma,ou=People,dc=ex,dc=com does not have permission to access the requested resource. Not authorized for the requested resource. Returning Forbidden response.
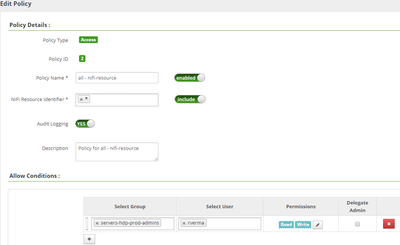
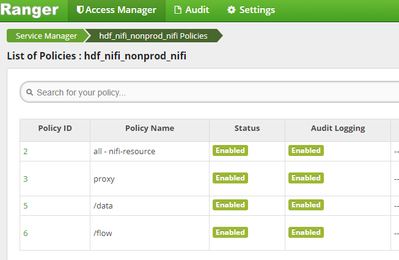
Ranger policy page - screenshot attached.
I have tried to add other users but still no success. If I add {user} in 'select user' field all LDAP users get access to Nifi UI.
Please suggest where I can define permissions/restrictions for the users.
Thanks,
Suraj
Created 10-27-2017 02:49 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looks like Nifi is sending the user name as "cn=rverma,ou=People,dc=ex,dc=com", but in ranger access is given to user "rverma". Check if you can sync users in ranger with the full name Nifi is using.
You can refer the below articles.
Created 10-29-2017 07:23 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks you for the suggestions.
I have gone through the links you've given but still I'm unable to access my Nifi UI through LDAP user. Can you please suggest is there anything that need to do in Ranger policy. As I'm able to access ranger with LDAP user but when same users I give in Ranger policy I'm unable to access NIfi UI.
Thanks
Suraj
Created 10-29-2017 09:32 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have a look at this HCC document
Created 10-30-2017 07:12 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Geoffrey Shelton Okot @vperiasamy
I have made the required changes as per the given links. How to remove anonymous user by getting default login. I ahve not given anonymous user in ranger policy.
Created 10-30-2017 08:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
have you succeeded in giving your Nifi users UI access through ranger? If so well and good , I don't quite understand the next part of your question. "How to remove the anonymous user by getting default login. I have not given anonymous user in ranger policy."
Can you elaborate
Created on 10-30-2017 08:29 AM - edited 08-17-2019 05:56 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
have you succeeded in giving your Nifi users UI access through ranger?
Ans> yes
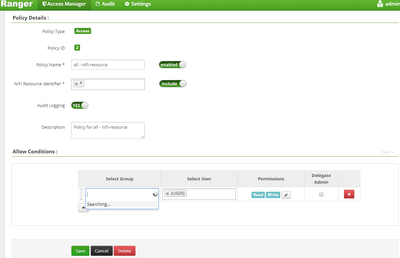
In Ranger policy, when I give {user} in select user tab I can login with LDAP users. Please check screenshot.
Also when I hit the Nifi UI (https://nifihost:9091/nifi) automatically it gets logged in with anonymous user. I do not get login page, but there is option to do login. As per attached screenshot.
My question is, I wanted to remove this default anonymous login. Please suggest, where I can do changes in configurations.
Also, In Ranger Policy if I remove {user} from select user tab and give specific LDAP users then I cannot login Nifi UI. Even it doesn't login with anonymous. I get below in logs
<em>==> /data/log/nifi/nifi-user.log <== 2017-10-30 06:11:54,514 WARN [main] o.a.n.a.util.IdentityMappingUtil Identity Mapping property nifi.security.identity.mapping.pattern.kerb was found, but was empty 2017-10-30 06:11:55,605 WARN [main] o.a.n.a.util.IdentityMappingUtil Identity Mapping property nifi.security.identity.mapping.pattern.kerb was found, but was empty 2017-10-30 06:11:55,652 WARN [main] o.a.n.a.util.IdentityMappingUtil Identity Mapping property nifi.security.identity.mapping.pattern.kerb was found, but was empty 2017-10-30 06:13:06,886 INFO [NiFi Web Server-22] o.a.n.w.a.c.IllegalStateExceptionMapper java.lang.IllegalStateException: Kerberos ticket login not supported by this NiFi.. Returning Conflict response. 2017-10-30 06:13:07,135 INFO [NiFi Web Server-94] o.a.n.w.a.c.AccessDeniedExceptionMapper anonymous does not have permission to access the requested resource. Unable to view the user interface. Returning Unauthorized response. 2017-10-30 06:14:03,287 INFO [NiFi Web Server-20] o.a.n.w.s.NiFiAuthenticationFilter Attempting request for (eyJhcGxlLG91PU1VTV9NdW1iYWkgSW5kaWEsb3U9QXNpYSxvdT1QZW9wbGUgYW5kIFdvcmtzdGF0aW9ucyxkYz1tb3Jua) GET https://10.248.13.199:9091/nifi-api/flow/current-user (source ip: 10.90.18.237) 2017-10-30 06:14:03,290 INFO [NiFi Web Server-20] o.a.n.w.s.NiFiAuthenticationFilter Authentication success for cn=Danny Leo,ou=Asia,ou=People and Workstations,dc=ex,dc=com 2017-10-30 06:14:03,293 INFO [NiFi Web Server-20] o.a.n.w.a.c.AccessDeniedExceptionMapper cn=Danny Leo,ou=People,ou=Asia,ou=People and Workstations,dc=ex,dc=com does not have permission to access the requested resource. Unable to view the user interface. Returning Forbidden response.<br></em>
It seems I have authorizations/permissions issue. Can you please suggest where I'm missing the configurations.
Thanks,
Suraj
Created 10-30-2017 09:43 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see the below error in the logs
INFO [NiFi Web Server-22] o.a.n.w.a.c.IllegalStateExceptionMapper java.lang.IllegalStateException: Kerberos ticket login not supported by this NiFi.. Returning Conflict response.
Your setup looks kerberized did you configuring a Login Identity Provider that integrates with a Kerberos Key?
<provider>
<identifier>kerberos-provider</identifier>
<class>org.apache.nifi.kerberos.KerberosProvider</class>
<property name="Default Realm">NIFI.APACHE.ORG</property>
<property name="Kerberos Config File">/etc/krb5.conf</property>
<property name="Authentication Expiration">12 hours</property>
</provider> With the above configuration, username/password authentication can be enabled by referencing this provider in nifi.properties.
nifi.security.user.login.identity.provider=kerberos-provider
In the Ranger UI your parameter Nifi Resource Identifier, I see you have put * which is open permissions the controlled valid options are
/flow -----Allows users to view the user interface /controller /tenants /site-to-site /system /proxy /counters
The guide linked correctly states that your NiFi must be configured to run securely (HTTPS) and have an authentication mechanism (user certificates. ldap, or kerberos) in place. Without a secure setup, all users who access the NiFi UI get in with anonymous access which gives all of them full access so all aspects of the NiFi UI.
Remove the http configuration to prevent uncontrolled anonymous access in nifi.properties
Created on 10-30-2017 11:35 AM - edited 08-17-2019 05:56 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am not using Kerberos. I dont know from where kerberos entries are coming in logs.
Nifi is already configured with SSL. Also I have created policies in Ranger. Please check below screenshot.
I have added users in all above policies.
Template for login-identity-providers.xml
<provider>
<identifier>ldap-provider</identifier>
<class>org.apache.nifi.ldap.LdapProvider</class>
<property name="Identity Strategy">USE_USERNAME</property>
<property name="Authentication Strategy">SIMPLE</property>
<property name="Manager DN">CN=hadoop_prd_ad_user,OU=Service Accounts,OU=Hadoop,OU=Servers and Services,DC=ex,DC=com</property>
<property name="Manager Password">xxx</property>
<property name="Referral Strategy">FOLLOW</property>
<property name="Connect Timeout">10 secs</property>
<property name="Read Timeout">10 secs</property>
<property name="Url">ldap://ldap.ex.com:389</property>
<property name="User Search Base">DC=ex,DC=com</property>
<property name="User Search Filter">sAMAccountName={0}</property>
<property name="Authentication Expiration">12 hours</property>
</provider>
nifi.security.user.login.identity.provider=ldap-provider
In the Ranger UI your parameter Nifi Resource Identifier I have removed * from policy.
authorizers.xml
<authorizer>
<identifier>ranger-provider</identifier>
<class>org.apache.nifi.ranger.authorization.RangerNiFiAuthorizer</class>
<property name="Ranger Audit Config Path">/usr/hdf/current/nifi/conf/ranger-nifi-audit.xml</property>
<property name="Ranger Security Config Path">/usr/hdf/current/nifi/conf/ranger-nifi-security.xml</property>
<property name="Ranger Service Type">nifi</property>
<property name="Ranger Application Id">nifi</property>
<property name="Allow Anonymous">false</property>
<property name="Ranger Admin Identity"></property>
<property name="Ranger Kerberos Enabled">false</property>
Still my issue is not get resolved. How it is automatically gets logged in with anonymous?
Created 10-30-2017 11:44 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you upload this log /data/log/nifi/nifi-user.log, meanwhile let me spin up a single node Nifi cluster and to try to reproduce your settings. Do you have some specific document or steps you followed?
Please revert