Community Articles
- Cloudera Community
- Support
- Community Articles
- Setting Up a Secure Apache NiFi Registry
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on 02-08-2018 01:11 AM - edited 08-17-2019 09:07 AM
Objective
This tutorial walks you through how to install and secure a NiFi Registry using client certificates. A quick example of modifying user privileges in the Registry is also included.
A video version of this tutorial can be seen here: https://youtu.be/qD03ao3R-a4
Note: To learn the basics of setting up an unsecured Registry and integrating with Apache NiFi see the HCC article Versioned DataFlows with Apache NiFi 1.5 and Apache NiFi Registry 0.1.0.
Environment
This tutorial was tested using the following environment and components:
- Mac OS X 10.11.6
- Apache NiFi Registry 0.1.0
- Apache NiFi Toolkit 1.5.0
Secure NiFi Registry Configuration
Download & Extract Tarballs
Download the tarball for the 0.1.0 Registry release:
nifi-registry-0.1.0-bin.tar.gz
and the tarball for the 1.5.0 NiFi Toolkit:
Extract the tars:
tar xzvf nifi-registry-0.1.0-bin.tar.gz tar xzvf nifi-toolkit-1.5.0-bin.tar.gz
Generate Configuration and Certificate Files
We will use the Apache NiFi TLS Toolkit to generate the necessary keystore, truststore, and client certificates. In this tutorial, we will create certs for two users: "sys_admin" and "test_user". The user “sys_admin” will have full access to the registry while “test_user” will be configured to have targeted access in the registry.
In the directory of your NiFi Toolkit install, run the following command:
./bin/tls-toolkit.sh standalone -n "localhost" -C "CN=sys_admin, OU=NIFI" -o target
Note: To see the usage information for the TLS Toolkit, run: ./bin/tls-toolkit.sh standalone -h.
TLS Toolkit generates the following in the
target directory:
CN=sys_admin_OU=NIFI.p12
CN=sys_admin_OU=NIFI.p12.password
localhost
nifi-cert.pem
nifi-key.key
The
localhost directory contains:
keystore.jks
nifi.properties
truststore.jks
Registry Configuration
Copy the keystore and trustore to the
conf directory of your Registry install.
Copy the values of the keystore and truststore properties from the
nifi.properties file:
nifi.security.keystore=./conf/keystore.jks nifi.security.keystoreType=jks nifi.security.keystorePasswd=taceJshGdkyBRy4B7mwaSnM3AkbN7ffewjn3nVIGidw nifi.security.keyPasswd=taceJshGdkyBRy4B7mwaSnM3AkbN7ffewjn3nVIGidw nifi.security.truststore=./conf/truststore.jks nifi.security.truststoreType=jks nifi.security.truststorePasswd=WJwg6F2jmUcvpxRHDiseNRc/VV59WOS+SdrZ5amtnsE
into the values for the equivalent properties in the nifi-registry.properties file:
nifi.registry.security.keystore=./conf/keystore.jks nifi.registry.security.keystoreType=jks nifi.registry.security.keystorePasswd=taceJshGdkyBRy4B7mwaSnM3AkbN7ffewjn3nVIGidw nifi.registry.security.keyPasswd=taceJshGdkyBRy4B7mwaSnM3AkbN7ffewjn3nVIGidw nifi.registry.security.truststore=./conf/truststore.jks nifi.registry.security.truststoreType=jks nifi.registry.security.truststorePasswd=WJwg6F2jmUcvpxRHDiseNRc/VV59WOS+SdrZ5amtnsE
While you are in nifi-registry.properties, modify the HTTP and HTTPS web properties as follows:
nifi.registry.web.http.host= nifi.registry.web.http.port= nifi.registry.web.https.host=localhost nifi.registry.web.https.port=18443
In the same Registry conf directory, modify authorizers.xml in two places. First in the userGroupProvider section, add the "sys_admin" DN to the "Initial Admin Identity 1" property:
<property name="Initial User Identity 1">CN=sys_admin, OU=NIFI</property>
Then in the accessPolicyProvider section, add the "sys_admin" DN to the "Initial Admin Identity" property:
<property name="Initial Admin Identity">CN=sys_admin, OU=NIFI</property>
Note: During this step, it is crucial that you specify the exact DN string used when the TLS Toolkit was invoked. A common error is entering "CN=sys_admin,OU=NIFI" which will not work as it has a missing space.
Add Certificate to Keychain
Double-click on the .p12 file that was generated by the TLS Toolkit. When prompted, provide the password from the .password file.
Start the Registry
In a terminal window, navigate to the directory where NiFi Registry was installed and run:
./bin/nifi-registry.sh start
Open Registry UI
Navigate to the registry UI in your web browser (Chrome used in the following examples):
https://localhost:18443/nifi-registry
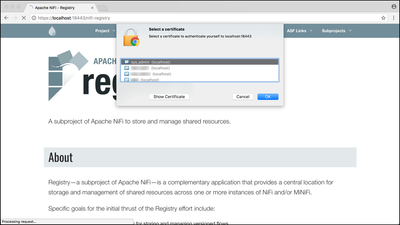
When prompted, select the "sys_admin" cert to add to your browser:
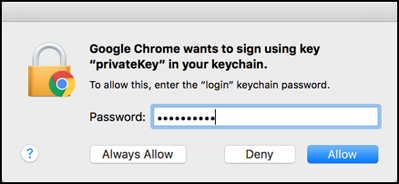
When prompted, enter your "login" keychain password:
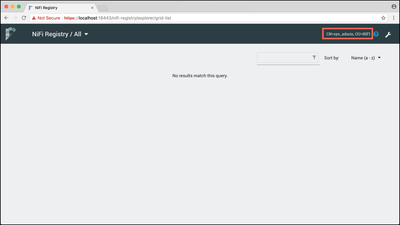
You should now be able to view the Registry UI as the "CN=sys_admin, OU=NIFI" user:
Registry Administration
The "sys_admin" user has full access to the registry. Here are some examples of administration functions immediately available.
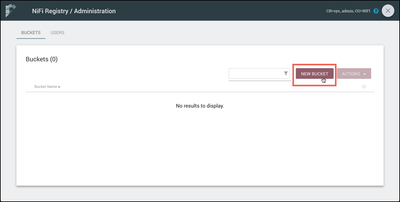
Bucket Creation
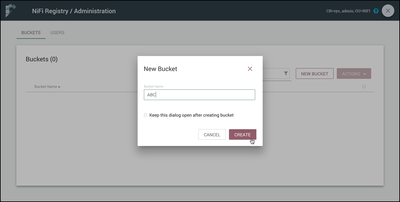
Select the Settings icon (

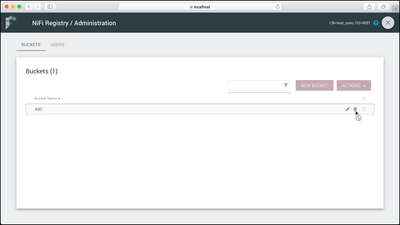
In the dialog that appears, enter the bucket name "ABC" and select the "Create" button.
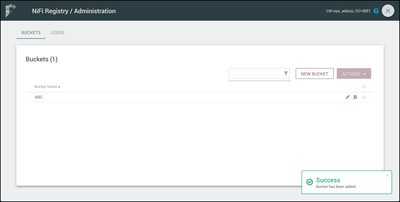
The "ABC" bucket is created:
User Administration
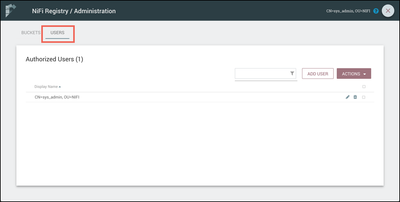
Select "Users" at the top of the UI to access the user administration area of the Registry:
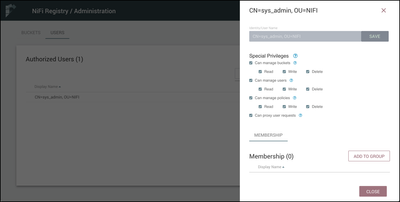
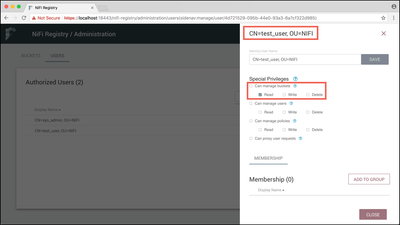
Select the pencil icon (

You can see that the "sys_admin" was given all special privileges as the Initial Admin Identity (IAI). The privileges for the IAI are not editable. Let's create a second user to see how bucket access can be restricted by modifying these privileges.
Second User Creation
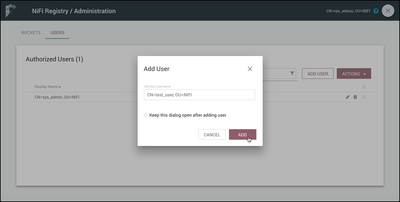
Close the side nav and select the "Add User" button.
Enter "CN=test_user, OU=NIFI" in the Identity field and select the "Add" button:
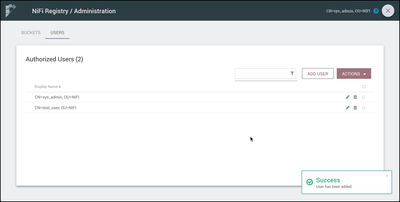
"CN=test_user", OU=NIFI" user is created:
Second User Certificate
Next we need a client certificate for "test_user".
Return to the directory of your NiFi Toolkit installation and run:
./bin/tls-toolkit.sh standalone -C "CN=test_user, OU=NIFI" -o target
NOTE:The output directory must be set to target in order for the existing CA certificate in that directory to be used.
TLS Toolkit generates the following additional files in the
target directory:
CN=test_user_OU=NIFI.p12
CN=test_user_OU=NIFI.p12.password
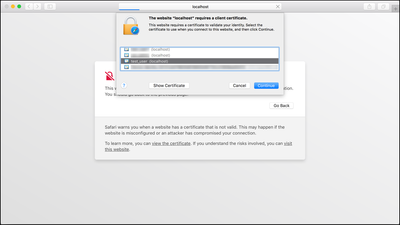
Add the .p12 cert to the Keychain as described earlier. However, choose a different browser this time to access the UI (Safari in the following examples):
https://localhost:18443/nifi-registry
Add the client certificate to the browser:
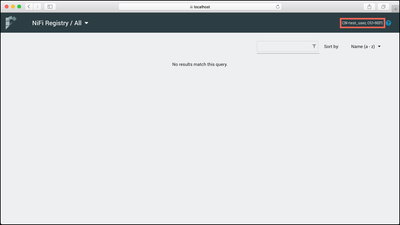
You should now be able to view the Registry UI as the "CN=test_user, OU=NIFI" user:
You can see that "test_user" has no access to Settings.
Return to the Chrome browser where "sys_admin" is the user. Give "test_user" read-only bucket privileges:
Return to the Safari browser where "test_user" is the user. Reload the browser. Select the Settings icon which is now available. The ABC bucket is now visible, but note that the Action to delete the bucket is not enabled, which is consistent with the privileges given to this user:
Additional Help
If you would like to learn more about NiFi Registry functionality and working with versioned flows in NiFi, see the following articles:
- Versioned DataFlows with Apache NiFi 1.5 and Apache NiFi Registry 0.1.0
- Apache NiFi - How do I deploy my flow?
Or documentation: