Support Questions
- Cloudera Community
- Support
- Support Questions
- Does NiFi CA generate self signed or signed cert?
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Does NiFi CA generate self signed or signed cert?
- Labels:
-
Apache NiFi
Created 08-14-2018 03:11 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Our browser requires interacting with only signed certificates. Does NiFi CA generate self signed or signed certs? I assume it is self signed and not integrated with a real certificate authoruity. But not sure. Feedback appreciated.
Created 08-14-2018 04:47 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Andrew Grande for confirming they are self signed.
Created on 08-14-2018 11:44 AM - edited 08-17-2019 07:34 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-
Just to add some clarity. The NiFi CA is a self-signed certificate authority (Meaning the NiFi CA's certificate is a root level CA and has not had its certificate signed by a higher authority). The NiFi TLS toolkit can be used to create client/server certificates that are then signed by this authority for use by NiFi. The truststore.jks file used by NiFi typically contains all the "trustedCertEntries" needed to authenticate any client certificates used to authenticate against NiFi. So this would include the trustedCertEntry for the NiFi CA. The keystore.jks file used by NiFi could contain the PrivateKeyEntry (which is the certificate that has been signed by the NiFi CA).
-
Within a browser there are certificates and a number of default and possibly user added Authorities. In order for your browser to trust any certificate signed by the NiFi CA, the public certificate for your NiFi CA must be added to your browsers trusted authorities.
-
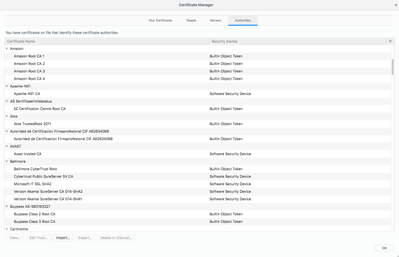
For example, you can see I have done that in Firefox here:
You will see "Apache-NiFi CA" has been added.
Now this browser will trust any certificate that has been signed by that authority.
-
Thank you,
Matt
Created 08-14-2018 06:37 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have provided a feature implementation (NIFI-5476 | PR 2935) in the current Apache NiFi master branch which allows the TLS Toolkit running in standalone mode to use an externally-signed CA certificate to sign node certificates. With this capability, you can purchase/obtain a certificate signed by a known (browser-installed) CA, which will be trusted by browsers. You can then use this certificate to sign node certificates. I am currently working on enabling the same feature in client/server mode, but it is not yet present.
Created on 05-19-2020 08:46 PM - edited 05-19-2020 08:52 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@MattWho Can you please tell how to add NIFI CA in authorities?
Currently we have use p12 file everytime for new DN generated by toolkit.
Do we need to add nifi-cert.pem while creating authority?
Created 06-05-2020 11:17 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is not clear to me what you are asking when you say "add NIFI CA in authorities".
Instructions on using the NiFi TLS toolkit can be found here:
https://nifi.apache.org/docs/nifi-docs/html/toolkit-guide.html#tls_toolkit
Using the Client/Server Tls Toolkit operational mode covered here:
https://nifi.apache.org/docs/nifi-docs/html/toolkit-guide.html#client-server
Will give you the ability to create a running NiFi CA authority "server" which will sign your NiFi node certificates created using the "client" mode.
Thanks,
Matt