Support Questions
- Cloudera Community
- Support
- Support Questions
- Duas fontes de autenticação do Nifi funcionando ao...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Duas fontes de autenticação do Nifi funcionando ao mesmo tempo
- Labels:
-
Apache NiFi
Created 05-09-2023 06:44 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Existe alguma forma de deixar dois tipos de autenticação no Nifi funcionando ao mesmo tempo? Exemplo: SAML + Autenticação Local (próprio nifi).
Ou ele só permite o uso de uma única fonte de autenticação configurada por vez?
Created 05-09-2023 09:51 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@orodriguesrenan
The "Single-User-Provider" and corresponding "Single-user-authorizer" were only developed and intended to be used when initially experimenting with NiFi. It was developed so that NiFi out of the box startup would be secured to help end-user avoid unsecured access to their NiFi. Prior to the introduction of these default authentication provider and Authorizer. NiFi out of the box startup would be unsecured HTTP. It was never the intent to use the single-user in production and it does not support configuring additional local user nor does the single-user-authorizer allow you to create/set unique authorization policies for other users.
For a multi-user environment you want to stop using the single-user-provider and single-user-authorizer and switch to authentication methods that support multiple users and an authorizer that supports configuring authorization policies.
NiFi does support multiple method of user authentication (Single-user-provider not included)
When you secure your NiFi so it is accessible only over an HTTPS connection, your NiFi must have a keystore and truststore. With only HTTPS enabled, the only user authentication support would be via a mutual TLS exchange with a user issues certificate that can be trusted by the NiFi truststore. TLS based user/client auth is ALWAYS enabled.
You can then configure additional methods of multi-tenant authentication. For example:
Since out of the box default is configured to use:
nifi.security.user.login.identity.provider=single-user-provider
You'll need to clear this property to use SAML or set it to another "login" based provider like ldap or kerberos.
Then you need to change your authorizers.xml from the default " single-user-authorizer" to an authorizer that supports mutli-tenant based authorization:
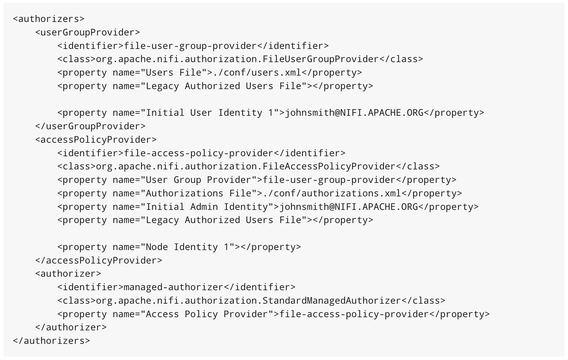
Example authorizers.xml
Here you would change the "Initial User Identity 1" and "Initial Admin Identity" to the SAML account user you want to act as the initial admin. The admin user would then be able to add authorization via the NiFi UI to allow other SAML users authorized access to the NiFI UI and control what those user are authorized once they are allowed in.
In the nifi.properties file you would need to tell NiFi to use this "managed-authorizer"
nifi.security.user.authorizer=managed-authorizer
It would be by default set to the "single-user-authorizer".
If you found that the provided solution(s) assisted you with your query, please take a moment to login and click Accept as Solution below each response that helped.
Thank you,
Matt
Created 05-09-2023 09:51 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@orodriguesrenan
The "Single-User-Provider" and corresponding "Single-user-authorizer" were only developed and intended to be used when initially experimenting with NiFi. It was developed so that NiFi out of the box startup would be secured to help end-user avoid unsecured access to their NiFi. Prior to the introduction of these default authentication provider and Authorizer. NiFi out of the box startup would be unsecured HTTP. It was never the intent to use the single-user in production and it does not support configuring additional local user nor does the single-user-authorizer allow you to create/set unique authorization policies for other users.
For a multi-user environment you want to stop using the single-user-provider and single-user-authorizer and switch to authentication methods that support multiple users and an authorizer that supports configuring authorization policies.
NiFi does support multiple method of user authentication (Single-user-provider not included)
When you secure your NiFi so it is accessible only over an HTTPS connection, your NiFi must have a keystore and truststore. With only HTTPS enabled, the only user authentication support would be via a mutual TLS exchange with a user issues certificate that can be trusted by the NiFi truststore. TLS based user/client auth is ALWAYS enabled.
You can then configure additional methods of multi-tenant authentication. For example:
Since out of the box default is configured to use:
nifi.security.user.login.identity.provider=single-user-provider
You'll need to clear this property to use SAML or set it to another "login" based provider like ldap or kerberos.
Then you need to change your authorizers.xml from the default " single-user-authorizer" to an authorizer that supports mutli-tenant based authorization:
Example authorizers.xml
Here you would change the "Initial User Identity 1" and "Initial Admin Identity" to the SAML account user you want to act as the initial admin. The admin user would then be able to add authorization via the NiFi UI to allow other SAML users authorized access to the NiFI UI and control what those user are authorized once they are allowed in.
In the nifi.properties file you would need to tell NiFi to use this "managed-authorizer"
nifi.security.user.authorizer=managed-authorizer
It would be by default set to the "single-user-authorizer".
If you found that the provided solution(s) assisted you with your query, please take a moment to login and click Accept as Solution below each response that helped.
Thank you,
Matt
Created 05-15-2023 05:25 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@orodriguesrenan
Have you resolved your issue? If so please mark the appropriate reply as the solution, as it will make it easier for others to find the answer in the future.
Cy Jervis, Manager, Community Program
Was your question answered? Make sure to mark the answer as the accepted solution.
If you find a reply useful, say thanks by clicking on the thumbs up button.