Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: How to grant user access to create tag based p...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to grant user access to create tag based policies in ranger?
Created 03-10-2022 08:48 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I want to grant a set of users access to add tag based policies in ranger. I have adde the users to data steward role which grants ranger/atlas admin access but still they get a access denied when create a tag based access policy. Creating resource based policies is working for them.
Ideally we want to grant them permissions to add tag based policies.
We use CDP public cloud 7.2.12 in AWS.
Any pointers are welcome. Thanks.
Created 03-14-2022 08:43 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Granting data steward role has fixed the issue. May be it was just a sync issue. However our requirement is to grant access to only tag based policies and not on resource based policies.
Created 03-14-2022 08:49 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
for tag based policies you can refer to https://docs.cloudera.com/runtime/7.2.10/security-ranger-authorization/topics/security-ranger-tag-ba...
Was your question answered? Make sure to mark the answer as the accepted solution.
If you find a reply useful, say thanks by clicking on the thumbs up button.
Created 03-10-2022 11:08 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @RajeshReddy ,
DataSteward role would usually grant “environments/adminRanger” permission which makes user Ranger and Atlas admin. This would suffice to create a tag based policy. Can we get more info on the error you are getting? Any screenshot or error messages would help us greatly to help you further.
Thanks.
Created 03-11-2022 01:03 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
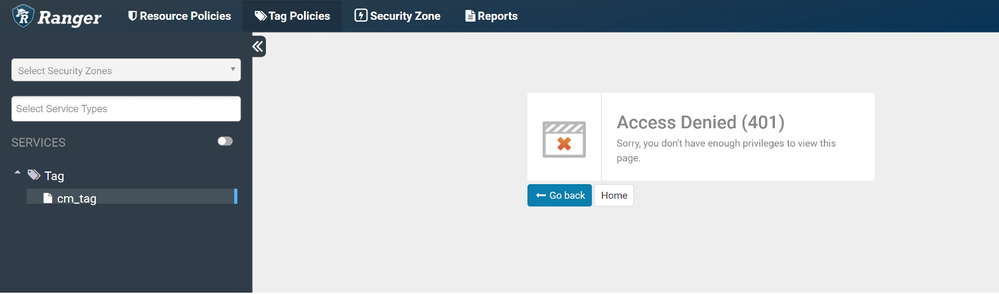
@VR46 Below is the error. The requirement is to grant the user access to only create tag based policies and deny creating resource based policies. But the result is opposite right now. Cant see any exception in ranger logs.
Created 03-14-2022 08:43 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Granting data steward role has fixed the issue. May be it was just a sync issue. However our requirement is to grant access to only tag based policies and not on resource based policies.
Created 03-13-2022 12:50 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Created 03-14-2022 08:42 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is not what we want to do.
Created 03-14-2022 08:49 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
for tag based policies you can refer to https://docs.cloudera.com/runtime/7.2.10/security-ranger-authorization/topics/security-ranger-tag-ba...
Was your question answered? Make sure to mark the answer as the accepted solution.
If you find a reply useful, say thanks by clicking on the thumbs up button.