Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: Kerberos Setup on HDP 2.6
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Kerberos Setup on HDP 2.6
- Labels:
-
Apache Hadoop
-
Apache Knox
Created 05-22-2017 06:45 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I want to setup kerberos on HDP 2.6. i have never done this before. Can anyone share the step by step commands/procedure on how to go about it? i am totally new to kerberos. i am using Centos.
Created 08-09-2017 02:47 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Assumption
REALM=GOLD.COM REALM Password =welcome1 KDC_HOST =KDC_SERVER_FQDN
Install kerberos package
yum install -y krb5-server krb5-libs krb5-workstation
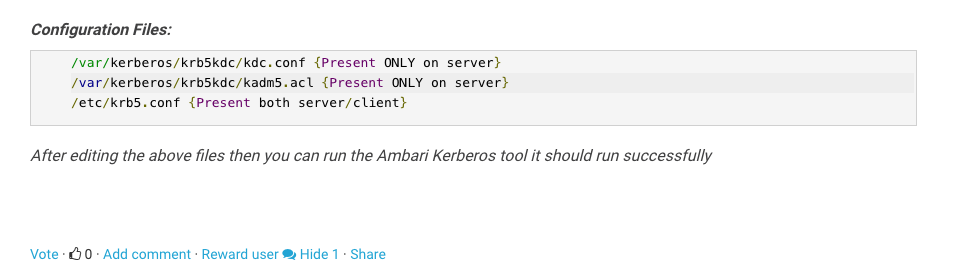
Edit Server Configuration Files
The configuration files for the server are located in the directory /var/kerberos/krb5kdc edit the 2 files
- kdc.conf
- kadm5.acl
- The conf file is the server configuration and the acl file, well the ACL. The ACL grants all privileges to anyone one with the admin role. Change the Kerberos GOLD.COM realm
cd /var/kerberos/krb5kdc/ vi kadm5.acl replace the REALM after the @ with the below */admin@GOLD.COM *
Edit the kdc.conf
[kdcdefaults]
kdc_ports = 88
kdc_tcp_ports = 88
[realms]
GOLD.COM = {
#master_key_type = aes256-cts
acl_file = /var/kerberos/krb5kdc/kadm5.acl
dict_file = /usr/share/dict/words
admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab
supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal camellia256-cts:normal camellia128-cts:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal
}
Edit the Client Configuration
Update the krb.conf on the KDC server copy this file to all the host in the cluster in the below directory /etc/krb5.conf
vi /etc/krb5.conf
# Configuration snippets may be placed in this directory as well
includedir /etc/krb5.conf.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
dns_lookup_realm = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
rdns = false
default_realm = GOLD.COM
default_ccache_name = KEYRING:persistent:%{uid}
[realms]
GOLD.COM = {
kdc = KDC_SERVER_FQDN
admin_server = KDC_SERVER_FQDN
}
[domain_realm]
.gold.com = GOLD.COM
gold.com = GOLD.COM
Create the DC database
When creating the KDC database we will need an entropy pool of random data
sudo kdb5_util create -s -r GOLD.COM Loading random data Initializing database '/var/kerberos/krb5kdc/principal' for realm 'GOLD.COM', master key name 'K/M@GOLD.COM' You will be prompted for the database Master Password. It is important that you NOT FORGET this password.Enter KDC database master key: welcome1 Re-enter KDC database master key to verify: welcome1
Start and Enable Kerberos
Start and enable the two services ensure you run status command to validate that kadmin is running
# sudo systemctl start krb5kdc kadmin # sudo systemctl enable krb5kdc kadmin Created symlink from /etc/systemd/system/multi-user.target.wants/krb5kdc.service to /usr/lib/systemd/system/krb5kdc.service. Created symlink from /etc/systemd/system/multi-user.target.wants/kadmin.service to /usr/lib/systemd/system/kadmin.service.
Check the Principals
# sudo kadmin.local Authenticating as principal root/admin@GOLD.COM with password. kadmin.local: listprincs K/M@GOLD.COM kadmin/admin@GOLD.COM kadmin/changepw@GOLD.COM kadmin/KDC_SERVER_FQDN@GOLD.COM kiprop/KDC_SERVER_FQDN@GOLD.COM krbtgt/UPUTEST.CH@UPUTEST.CH kadmin.local:
Must create a root principal for kerberization
kadmin.local: addprinc root/admin WARNING: no policy specified for root/admin@GOLD.COM; defaulting to no policy Enter password for principal "root/admin@GOLD.COM": Re-enter password for principal "root/admin@GOLD.COM": Principal "root/admin@GOLD.COM" created.
Install kerberos Client package
on tall the hosts in the cluster install the client
yum install -y krb5-libs krb5-workstation
This will deliver the necessary files copy the krb5.conf from the KDC server to all the client hosts
Invoke kerberos tool in Ambari
When running the kerberization tool in Ambari use
root/admin@GOLD.COM password welcome1
Follow the instructions take care that you installed JCE on the KDC server
Created 10-26-2018 11:30 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Created 10-29-2018 02:48 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there an explanation as to why a user can fail to accept an answer because the option is "grayed out"? In this thread, a user wanted to accept my response but somehow he is unable 🙂
Can you help !!!
Created 10-30-2018 12:40 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Only a user who own the thread Or a user with 1000+ points can accept other users answers as accepted.
I have marked your previous answer as "Accepted" which you answered on "Aug 09, 2017" as that answer looks more informative form this HCC thread perspective.
- « Previous
- Next »