Support Questions
- Cloudera Community
- Support
- Support Questions
- NiFi Error javax.net.ssl.SSLPeerUnverifiedExceptio...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NiFi Error javax.net.ssl.SSLPeerUnverifiedException: Hostname not verified
- Labels:
-
Apache NiFi
Created 04-10-2019 05:01 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Current version: 1.6.0
Upgrade version: 1.8.0
Applying the cluster, accessing the ui results in an error.
(x.x.x.x is hostname, my server ip..)
The key was not created as a wildcard.
---UI Error---
javax.net.ssl.SSLPeerUnverifiedException: Hostname x.x.x.x not verified: certificate: sha256/cj+QcD4F2YafhbXSeRmuLznbS24EWVhAvCbU71aVGWo= DN: CN=x,x,x,x, OU=NIFI subjectAltNames: [x.x.x.x]
---api access error---
https://x.x.x.x:1234/nifi-api/flow/current-user
javax.net.ssl.SSLPeerUnverifiedException: Hostname x.x.x.x not verified: certificate: sha256/!!!#$@!#qtA3h/Nhqm7wcLzM= DN: CN=x.x.x.x, OU=NIFI subjectAltNames: [x.x.x.x]
---log Error---
2019-04-08 08:26:28,522 WARN [Replicate Request Thread-5] o.a.n.c.c.h.r.ThreadPoolRequestReplicator Failed to replicate request GET /nifi-api/flow/current-user to x.x.x.x:9443 due to javax.net.ssl.SSLPeerUnverifiedException: Hostname x.x.x.x not verified: certificate: sha256/IiBnANAzEOL~~~qm7wcLzM= DN: CN=x.x.x.x, OU=NIFI subjectAltNames: [x.x.x.x] 2019-04-08 08:26:28,523 WARN [Replicate Request Thread-5] o.a.n.c.c.h.r.ThreadPoolRequestReplicator javax.net.ssl.SSLPeerUnverifiedException: Hostname x.x.x.x not verified: certificate: sha256/IiBnANAzEOLVg+DipeiOT+fkIDpqtA3h/Nhqm7wcLzM= DN: CN=x.x.x.x, OU=NIFI subjectAltNames: [x.x.x.x] at okhttp3.internal.connection.RealConnection.connectTls(RealConnection.java:316) at okhttp3.internal.connection.RealConnection.establishProtocol(RealConnection.java:270) at okhttp3.internal.connection.RealConnection.connect(RealConnection.java:162) at okhttp3.internal.connection.StreamAllocation.findConnection(StreamAllocation.java:257) at okhttp3.internal.connection.StreamAllocation.findHealthyConnection(StreamAllocation.java:135) at okhttp3.internal.connection.StreamAllocation.newStream(StreamAllocation.java:114) at okhttp3.internal.connection.ConnectInterceptor.intercept(ConnectInterceptor.java:42) at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:147) at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:121) at okhttp3.internal.cache.CacheInterceptor.intercept(CacheInterceptor.java:93) at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:147) at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:121) at okhttp3.internal.http.BridgeInterceptor.intercept(BridgeInterceptor.java:93) at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:147) at okhttp3.internal.http.RetryAndFollowUpInterceptor.intercept(RetryAndFollowUpInterceptor.java:126) at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:147) at okhttp3.internal.http.RealInterceptorChain.proceed(RealInterceptorChain.java:121) at okhttp3.RealCall.getResponseWithInterceptorChain(RealCall.java:200) at okhttp3.RealCall.execute(RealCall.java:77) at org.apache.nifi.cluster.coordination.http.replication.okhttp.OkHttpReplicationClient.replicate(OkHttpReplicationClient.java:138) at org.apache.nifi.cluster.coordination.http.replication.okhttp.OkHttpReplicationClient.replicate(OkHttpReplicationClient.java:132) at org.apache.nifi.cluster.coordination.http.replication.ThreadPoolRequestReplicator.replicateRequest(ThreadPoolRequestReplicator.java:647) at org.apache.nifi.cluster.coordination.http.replication.ThreadPoolRequestReplicator$NodeHttpRequest.run(ThreadPoolRequestReplicator.java:839) at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:511) at java.util.concurrent.FutureTask.run(FutureTask.java:266) at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) at java.lang.Thread.run(Thread.java:748)
--- keystore.jks------
Keystore type: jks Keystore provider: SUN Your keystore contains 1 entry Alias name: nifi-key Creation date: Apr 5, 2019 Entry type: PrivateKeyEntry Certificate chain length: 2 Certificate[1]: Owner: CN=x.x.x.x, OU=NIFI Issuer: CN=x.x.x.x, OU=NIFI Serial number: 169ec64~~~~00 Valid from: Fri Apr 05 07:26:15 UTC 2019 until: Mon Apr 04 07:26:15 UTC 2022 Certificate fingerprints: MD5: 6B:70:04~~6:FF:CD:D1:29:E4 SHA1: 88:~~~~:AE:8B:9B:10:BF:F4 SHA256: 90:5A:FA:AF:B7:~~~~:7F:CE:89:95:64:BC:C1:53:E8:E6:58:30:7B:AC Signature algorithm name: SHA256withRSA Subject Public Key Algorithm: 2048-bit RSA key Version: 3 Extensions: #1: ObjectId: 2.5.29.35 Criticality=false AuthorityKeyIdentifier [ KeyIdentifier [ 0000: C8 B4~~~~~~~~ D0 12 8D A4 5C ...oNB.(.......\ 0010: 1D 6C 42 FC .lB. ] ] #2: ObjectId: 2.5.29.19 Criticality=false BasicConstraints:[ CA:false PathLen: undefined ] #3: ObjectId: 2.5.29.37 Criticality=false ExtendedKeyUsages [ clientAuth serverAuth ] #4: ObjectId: 2.5.29.15 Criticality=true KeyUsage [ DigitalSignature Non_repudiation Key_Encipherment Data_Encipherment Key_Agreement ] #5: ObjectId: 2.5.29.17 Criticality=false SubjectAlternativeName [ DNSName: x.x.x.x ] #6: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: 0B F7 ~~F5 2C B8 ..Y.vu..?P....,. 0010:~~7 32 ...2 ] ] Certificate[2]: Owner: CN=x.x.x.x, OU=NIFI Issuer: CN=x.x.x.x, OU=NIFI Serial number: 169ec64~~000000 Valid from: Fri Apr 05 07:26:15 UTC 2019 until: Mon Apr 04 07:26:15 UTC 2022 Certificate fingerprints: MD5: 94:F8:68:14~~~~E2:08:29:55:B8:D6:7D SHA1: 5B:E6:A1:D1:2A:4F:27:~~~:9E:85:1F:66:77:68:4C:C9:55:27:95:FD SHA256: 67:33:71~~A:1F:EF:1D:57:7E:BB:13:2F:4C:94:1F:B2:58:59:70 Signature algorithm name: SHA256withRSA Subject Public Key Algorithm: 2048-bit RSA key Version: 3 Extensions: #1: ObjectId: 2.5.29.35 Criticality=false AuthorityKeyIdentifier [ KeyIdentifier [ 0000: C8 B4 80~~E 08 D0 12 8D A4 5C ...oNB.(.......\ 0010: 1D 6C 42 FC ~~.lB. ] ] #2: ObjectId: 2.5.29.19 Criticality=false BasicConstraints:[ CA:true PathLen:21474~~7 ] #3: ObjectId: 2.5.29.37 Criticality=false ExtendedKeyUsages [ clientAuth serverAuth ] #4: ObjectId: 2.5.29.15 Criticality=true KeyUsage [ DigitalSignature Non_repudiation Key_Encipherment Data_Encipherment Key_Agreement Key_CertSign Crl_Sign ] #5: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: C8 B4 80 6F 4E ~~ 8D A4 5C ...oNB.(.......\ 0010: 1D 6C 42 FC .lB. ] ] ******************************************* *******************************************
I don't know what the problem.
+I have no choice but to use the domain name and host name as an ip.
I understand that the key tool provided by the nifi only provides the domain name of the character. as follows
SubjectAlternativeName [
DNSName: nifi-1
]
But I want to use it as follows.
(x.x.x.x is my ip address.)
SubjectAlternativeName [
DNSName: x.x.x.x
IPAddress: x.x.x.x
]
tell me how to create a key with Java toolkit.
Created 09-17-2020 10:14 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have also faced the same issue, where i was running two instances of nifi on VM. As forwarding of ports and its connectivitiy from host browser(like chrome) are having issues, I recreated certificates using SAN - subjectAltNames using tls-toolkit.
I was trying to access https://192.168.56.31:9441/nifi from windows maching and said address 192.168.56.31 is of local VM running centos 7.x. Earlier default certificate was not having safe IP 192.168.56.31, it was throwing error.
bin/tls-toolkit.sh standalone -n '192.168.56.31(2)' -C 'CN=username,OU=NIFI' --subjectAlternativeNames '192.168.56.31,0.0.0.0'This has created necessary certificates and keystores. I have copied this keystores at appropriate nifi conf directory(excluding nifi.properties, to make sure, earlier configuration done is not messed up).
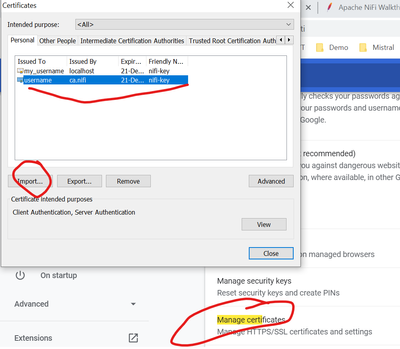
Once done, import generated .p12 certifcate and password file in chrome using settings->manage
certificates
master:[root]/root/nifi/nifi-toolkit-1.12.0>ll
total 92
-rw-r--r--. 1 root root 6673 Jan 22 2020 NOTICE
-rw-r--r--. 1 root root 41590 Jan 22 2020 LICENSE
drwxr-xr-x. 3 root root 12288 Jan 22 2020 lib
drwxr-xr-x. 3 root root 69 Jan 22 2020 classpath
drwxr-xr-x. 4 root root 160 Sep 10 17:36 target
drwxr-xr-x. 2 root root 194 Sep 15 21:11 conf
drwxr-xr-x. 4 root root 4096 Sep 15 21:14 bin
-rw-------. 1 root root 1196 Sep 17 10:17 nifi-cert.pem
-rw-------. 1 root root 1679 Sep 17 10:17 nifi-key.key
drwx------. 2 root root 71 Sep 17 10:17 node1.nifi
drwx------. 2 root root 71 Sep 17 10:18 node2.nifi
drwxr-xr-x. 5 root root 148 Sep 17 10:25 ..
drwx------. 2 root root 71 Sep 17 16:26 192.168.56.31
drwx------. 2 root root 71 Sep 17 16:26 192.168.56.31_2
-rw-------. 1 root root 3469 Sep 17 16:26 CN=username_OU=NIFI.p12
drwxr-xr-x. 11 root root 4096 Sep 17 16:26 .
-rw-------. 1 root root 43 Sep 17 16:26 CN=username_OU=NIFI.passwordAbove shows generated .p12 file and other configurations.
In chrome, after importing certificates, it looks like this:
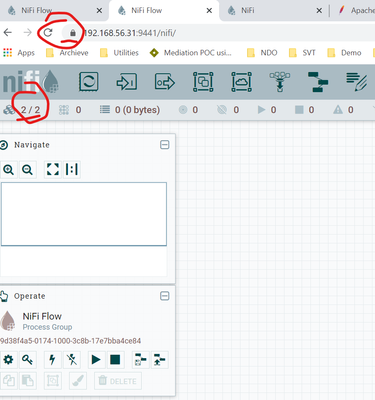
UI looks like below:
Created 05-14-2019 02:52 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I solve this problem my self Using 'KeyStore Explore'.
SubjectAlternativeName [
DNSName: x.x.x.x
IPAddress: x.x.x.x
]
Created 03-25-2020 05:55 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @juhee13_kim ,
How did you resolved the issue. I am also getting the same exception.
An unexpected error has occurred
javax.net.ssl.SSLPeerUnverifiedException: Hostname XXXXXXX not verified: certificate: sha256/Kt0
Any help is apprecieted.
Created 05-16-2019 05:52 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
how to add the IPAddress into the SubjectAlternativeName with the tls-toolkit.sh?
Created 09-17-2020 10:14 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have also faced the same issue, where i was running two instances of nifi on VM. As forwarding of ports and its connectivitiy from host browser(like chrome) are having issues, I recreated certificates using SAN - subjectAltNames using tls-toolkit.
I was trying to access https://192.168.56.31:9441/nifi from windows maching and said address 192.168.56.31 is of local VM running centos 7.x. Earlier default certificate was not having safe IP 192.168.56.31, it was throwing error.
bin/tls-toolkit.sh standalone -n '192.168.56.31(2)' -C 'CN=username,OU=NIFI' --subjectAlternativeNames '192.168.56.31,0.0.0.0'This has created necessary certificates and keystores. I have copied this keystores at appropriate nifi conf directory(excluding nifi.properties, to make sure, earlier configuration done is not messed up).
Once done, import generated .p12 certifcate and password file in chrome using settings->manage
certificates
master:[root]/root/nifi/nifi-toolkit-1.12.0>ll
total 92
-rw-r--r--. 1 root root 6673 Jan 22 2020 NOTICE
-rw-r--r--. 1 root root 41590 Jan 22 2020 LICENSE
drwxr-xr-x. 3 root root 12288 Jan 22 2020 lib
drwxr-xr-x. 3 root root 69 Jan 22 2020 classpath
drwxr-xr-x. 4 root root 160 Sep 10 17:36 target
drwxr-xr-x. 2 root root 194 Sep 15 21:11 conf
drwxr-xr-x. 4 root root 4096 Sep 15 21:14 bin
-rw-------. 1 root root 1196 Sep 17 10:17 nifi-cert.pem
-rw-------. 1 root root 1679 Sep 17 10:17 nifi-key.key
drwx------. 2 root root 71 Sep 17 10:17 node1.nifi
drwx------. 2 root root 71 Sep 17 10:18 node2.nifi
drwxr-xr-x. 5 root root 148 Sep 17 10:25 ..
drwx------. 2 root root 71 Sep 17 16:26 192.168.56.31
drwx------. 2 root root 71 Sep 17 16:26 192.168.56.31_2
-rw-------. 1 root root 3469 Sep 17 16:26 CN=username_OU=NIFI.p12
drwxr-xr-x. 11 root root 4096 Sep 17 16:26 .
-rw-------. 1 root root 43 Sep 17 16:26 CN=username_OU=NIFI.passwordAbove shows generated .p12 file and other configurations.
In chrome, after importing certificates, it looks like this:
UI looks like below:
Created 09-17-2020 10:20 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Parag!
For shareing this information , with your solution we are able to fix our issue good job!
Created 03-30-2023 02:31 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Solo quiero aumentar el nifi con https y no autenticación con un certificado, si no lo que necesito es autenticación con Azure AD y ¿cómo resolvería ese error?
javax.net.ssl.SSLPeerUnverifiedException: Hostname x.x.x.x no verificado: certificado: sha256 / IV5FlhE254QHOs5b0WnJ4znmiEpdb71ItqIVK7CiekM = DN: EMAILADDRESS = juan@gmail
Created 03-31-2023 02:32 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ABel-asd as this is an older post, you would have a better chance of receiving a resolution by starting a new thread. This will also be an opportunity to provide details specific to your environment that could aid others in assisting you with a more accurate answer to your question. You can link this thread as a reference in your new post.
Regards,
Vidya Sargur,Community Manager
Was your question answered? Make sure to mark the answer as the accepted solution.
If you find a reply useful, say thanks by clicking on the thumbs up button.
Learn more about the Cloudera Community: