Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: NiFi Registry with AWS Load balancer Issue
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NiFi Registry with AWS Load balancer Issue
- Labels:
-
Apache NiFi
-
NiFi Registry
Created 07-08-2022 03:29 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I have configured the nifi registry with an aws load balancer
I have configured both type of load balancer (application(https)/ tcp) but none of them accessible from nifi nodes and not listing the buckets list.
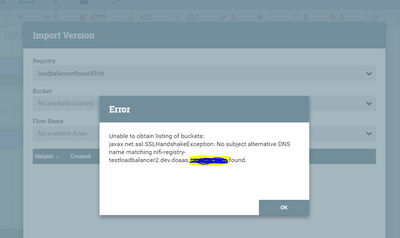
Below are the errors I am getting:
with AWS network type load balancer:
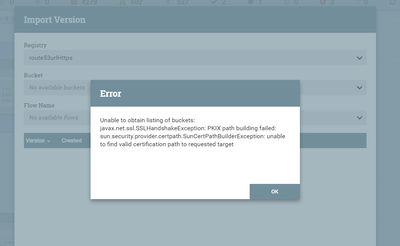
with application (https) load balancer:
but if I add an individual registry node, every thing is working fine.
Issue is with the load balancer only!! Please help what change needs to be done on the load balancer side.
Created 07-08-2022 12:36 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Meeran
Your issue in both exceptions is with the mutual TLS handshake and not really a configuration issue in NiFi or NiFi-Registry. And may not even be an issue with your LBs.
Your first exception shared is telling you that the Registry-Client hostname configured in your NiFi was not found as a SAN in the serverAuth certificate returned by the target server. In order for the mutual TLS handshake to succeed there would need to be a matching hostname SAN entry in the certificate.
The Second exception you shared is telling you that the truststore.jks does not contain the required complete trust chain needed to trust the private certificates DN. The privateKey used by the Server and Client will have an owner DN and Issuer DN. The Issuer DN is the authority that signed that certificate and must be found in the truststore. Some issuers are intermediate authorities meaning that also have an owner DN signed by another issuer authority. This is a trust chain. So your truststore would also need to to contain the trustedCertEntry for that intermediate's issuer as well. Once you reach the issuers certificate where both the owner an issuer DN match, you have reached the root authority of that trust chain.
This is all part of the TLS spec and not specific to anything NiFi is enforcing itself.
you can use openssl in most but not all to get the public certs for the authorities:
openssl s_client -connect <hostname>:<port> -showcerts
If you found this response assisted with your query, please take a moment to login and click on "Accept as Solution" below this post.
Thank you,
Matt
Created 07-13-2022 06:13 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the explanation @Matt.
I have generated the certs to add it to aws loadbalancer using the nifi toolkit with the below command
tls-toolkit.sh client -c nifi-ca.dev.xxx.company.com -D "CN=nifi-registry-testloadbalancer3.dev.xxx.company.com, OU=NIFI" -p 8443 -t somekey
its successfully generation the certs with keystore.jks, truststore.jks, config with required password and cert but aws needs a private key in pem format to upload a certificate.
I have extracted the pem from keystore.jks using openssl but generated pem is not working and aws is not accepting the cert and through error as invalid key.
could you please help me here what I am doing wrong, is there a way that i can get pem key with nifi toolkit
Created 07-14-2022 07:11 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Meeran
Sharing the full exception that was output when you tried to import key maybe helpful, But I am also not sure why you are trying to add a Client private key to your AWS load-balancer?
I am not well versed on AWS load balancer configuration, so helping you get past your LB setup/configuration issue may be difficult for me. I do know TLS very well and explained the meaning of the two TLS exceptions you encountered.
The HTTPS LB exception could be resolved by making sure the TrustedCertEntry(s) for the complete trust chain for the HTTPS LB's privateKey are present in the NiFi-Registry's truststore.jks. You should also add the trustedcertEntry for the NiFi CA you appeared to be using to the truststore used by your HTTPS LB.
Thank you,
Matt