Support Questions
- Cloudera Community
- Support
- Support Questions
- No enabled components in top toolbar after logging...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
No enabled components in top toolbar after logging into nifi UI
- Labels:
-
Apache NiFi
Created on 12-12-2021 12:08 PM - edited 12-12-2021 02:09 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello all,
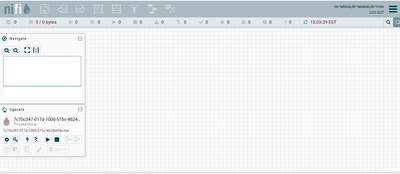
I am getting issues after starting NIFI (LDAP enabled). I started successfully to log in my NIFI, but all components are disabled as below.
I guess the problem may be in setting at authorizers.xml, but I couldn't find anything from there. Below is my authorizers.xml. Could you please give me any ideas for this issue? Thank you in advance.
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<authorizers>
<userGroupProvider>
<identifier>file-user-group-provider</identifier>
<class>org.apache.nifi.authorization.FileUserGroupProvider</class>
<property name="Users File">./conf/users.xml</property>
<property name="Legacy Authorized Users File"></property>
<property name="Initial User Identity 1">cn=admin,dc=ananas,dc=com</property>
</userGroupProvider>
<accessPolicyProvider>
<identifier>file-access-policy-provider</identifier>
<class>org.apache.nifi.authorization.FileAccessPolicyProvider</class>
<property name="User Group Provider">file-user-group-provider</property>
<property name="Authorizations File">./conf/authorizations.xml</property>
<property name="Initial Admin Identity">cn=admin,dc=ananas,dc=com</property>
<property name="Legacy Authorized Users File"></property>
<property name="Node Identity 1"></property>
<property name="Node Group"></property>
</accessPolicyProvider>
<authorizer>
<identifier>managed-authorizer</identifier>
<class>org.apache.nifi.authorization.StandardManagedAuthorizer</class>
<property name="Access Policy Provider">file-access-policy-provider</property>
</authorizer>
<authorizer>
<identifier>file-provider</identifier>
<class>org.apache.nifi.authorization.FileAuthorizer</class>
<property name="Authorizations File">./conf/authorizations.xml</property>
<property name="Users File">./conf/users.xml</property>
<property name="Initial Admin Identity">cn=admin,dc=ananas,dc=com</property>
<property name="Legacy Authorized Users File"></property>
<property name="Node Identity 1"></property>
</authorizer>
</authorizers>
Created 12-13-2021 12:14 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@sunny_de
NiFi can only support a single "authorizer". Your authorizers.xml file attached shows that you have two configured:
1. managed-authorizer
2. file-provider <-- (legacy and deprecated in favor of above)
Which authorizer is actually being used by NiFi's core is determined by what you have configured in the following property in the nifi.properties file:
nifi.security.user.authorizer=
So make sure above is set to "managed-authorizer"
This provider then references the:
file-access-policy-provider This provider is responsible for generating the "authorizations.xml" file which contains all the authorizations created for your users. It will initially seed this file with the minimum authorizations needed for the configured "initial admin identity" string value (Case sensitive),
NOTE: The authorizations.xml file is only generated if it does not already exist. If this file already exists and changes made to the file-access-policy-provider will not be reflected in that file. The expectation is once the initial admin and node policies have been seeded, all additional authorization are granted from within the NiFi UI.
The "file-access-policy-provider" then references the:
file-user-group-providerThis provider is designed to generate the users.xml file if it does not exist and seed it with the initial user identities (initial admin and NiFi nodes if clustered).
Seeing as how you're able to see the NiFi UI, that tells me that your initial admin was successfully created and given at least "view the user interface" policy permissions. The initial policy setup will only grant polciy permission related to the canvas if a flow.xml.gz was already present when NiFi was secured or started for the first time. In this case, it appears that you did not have a flow.xml.gz and NiFi created one on first startup which happens after the initial admin was created and authorized.
You will however have admin policies assigned for your initial admin that will allow you to setup any additional policy you need. I can see from the "operate" panel in the left hand side of the canvas that the following icon is NOT greyed out:
This means that your authenticated user is authorized to set policies on the current selected component (in this case the root process group). Click on this icon and grant yourself at a minimum the following policies:
1. view the component
2. modify the component
3. view the data
4. modify the data
5. view provenance
After applying above, the icon across the top of the UI should no longer be greyed out since you are now authorized to make modification to the root process group. So now you can drag and drop items to the canvas. When you add new components (processors, input/output ports, funnels, child process groups, etc) to the canvas they will inherit there policies from the parent process group, but you can always select any component and specifically set policies per component. In a multi-team use NiFi, it is common to create a child process group for each team or person and authorized on the desired members to each process group. This prevents user1 from modifying user 2's process group and components within it and vice versa.
For more information on setting users, groups, and policies, here is the link to the NiFi documentation that talks about this topic:
https://nifi.apache.org/docs/nifi-docs/html/administration-guide.html#config-users-access-policies
If you found this response assisted with your query, please take a moment to login and click on "Accept as Solution" below this post.
Thank you,
Matt
Created 12-13-2021 12:14 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@sunny_de
NiFi can only support a single "authorizer". Your authorizers.xml file attached shows that you have two configured:
1. managed-authorizer
2. file-provider <-- (legacy and deprecated in favor of above)
Which authorizer is actually being used by NiFi's core is determined by what you have configured in the following property in the nifi.properties file:
nifi.security.user.authorizer=
So make sure above is set to "managed-authorizer"
This provider then references the:
file-access-policy-provider This provider is responsible for generating the "authorizations.xml" file which contains all the authorizations created for your users. It will initially seed this file with the minimum authorizations needed for the configured "initial admin identity" string value (Case sensitive),
NOTE: The authorizations.xml file is only generated if it does not already exist. If this file already exists and changes made to the file-access-policy-provider will not be reflected in that file. The expectation is once the initial admin and node policies have been seeded, all additional authorization are granted from within the NiFi UI.
The "file-access-policy-provider" then references the:
file-user-group-providerThis provider is designed to generate the users.xml file if it does not exist and seed it with the initial user identities (initial admin and NiFi nodes if clustered).
Seeing as how you're able to see the NiFi UI, that tells me that your initial admin was successfully created and given at least "view the user interface" policy permissions. The initial policy setup will only grant polciy permission related to the canvas if a flow.xml.gz was already present when NiFi was secured or started for the first time. In this case, it appears that you did not have a flow.xml.gz and NiFi created one on first startup which happens after the initial admin was created and authorized.
You will however have admin policies assigned for your initial admin that will allow you to setup any additional policy you need. I can see from the "operate" panel in the left hand side of the canvas that the following icon is NOT greyed out:
This means that your authenticated user is authorized to set policies on the current selected component (in this case the root process group). Click on this icon and grant yourself at a minimum the following policies:
1. view the component
2. modify the component
3. view the data
4. modify the data
5. view provenance
After applying above, the icon across the top of the UI should no longer be greyed out since you are now authorized to make modification to the root process group. So now you can drag and drop items to the canvas. When you add new components (processors, input/output ports, funnels, child process groups, etc) to the canvas they will inherit there policies from the parent process group, but you can always select any component and specifically set policies per component. In a multi-team use NiFi, it is common to create a child process group for each team or person and authorized on the desired members to each process group. This prevents user1 from modifying user 2's process group and components within it and vice versa.
For more information on setting users, groups, and policies, here is the link to the NiFi documentation that talks about this topic:
https://nifi.apache.org/docs/nifi-docs/html/administration-guide.html#config-users-access-policies
If you found this response assisted with your query, please take a moment to login and click on "Accept as Solution" below this post.
Thank you,
Matt
Created 12-13-2021 02:27 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Many thanks @MattWho It seems that I started NIFI based on the old flow.xml.gz. I successfully granted all access for myself.