Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: What extension file does Hue Configuration for...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
What extension file does Hue Configuration for SSL
- Labels:
-
Cloudera Hue
Created on 10-13-2014 10:44 AM - edited 09-16-2022 02:09 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
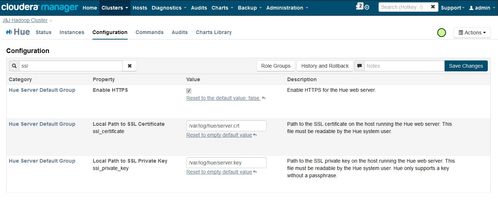
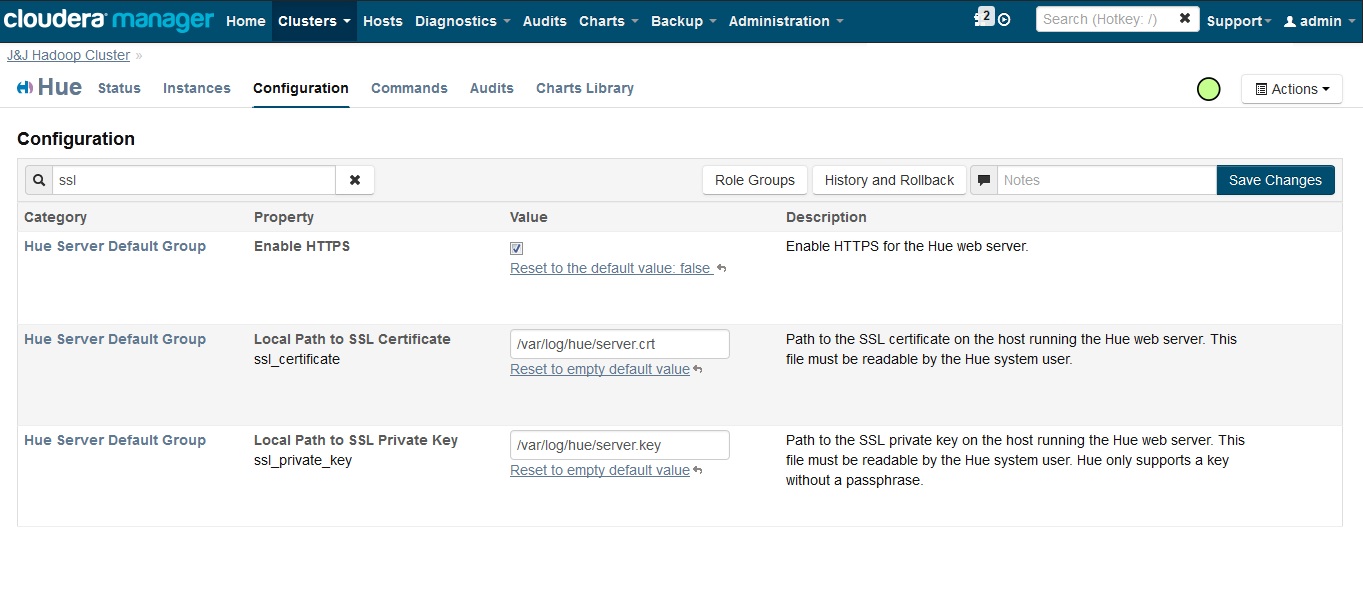
Does ssl_certificate accepts only as .crt file extension or .pem or .cer or .der also works?
because when i did ssl with self signed certificate everything hue starts but when i did with Microsoft generated ssl certificate and key it gave me this error
OpenSSL.SSL.Error: [('PEM routines', 'PEM_read_bio', 'no start line'), ('SSL
routines', 'SSL_CTX_use_certificate_file', 'PEM lib')]
Created 10-13-2014 06:47 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks alot,
I got this issue resolved.
The certificate generated from IIS Microsoft was not correct
Once i got the ptx format for certificate.
I extracted the key and certificate from .ptx format as .key and .crt file like
For the key:-
openssl pkcs12 -in [yourfile.pfx] -nocerts -out [keyfile-encrypted.key]
For the certificate
openssl pkcs12 -in [yourfile.pfx] -clcerts -nokeys -out [certificate.crt]
Just gave all the rights to both key and cert and made the key passphrase less. as
cp [server.key] [server.key.org]
openssl rsa -in [server.key].org -out [server.key]
and gave the path of key and cert in Hue.
Created 10-13-2014 10:46 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Created 10-13-2014 11:20 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The extension does not matter, but the format does. The file should be in "PEM" format. It should contain these lines:
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
-Ben
Created 10-13-2014 06:47 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks alot,
I got this issue resolved.
The certificate generated from IIS Microsoft was not correct
Once i got the ptx format for certificate.
I extracted the key and certificate from .ptx format as .key and .crt file like
For the key:-
openssl pkcs12 -in [yourfile.pfx] -nocerts -out [keyfile-encrypted.key]
For the certificate
openssl pkcs12 -in [yourfile.pfx] -clcerts -nokeys -out [certificate.crt]
Just gave all the rights to both key and cert and made the key passphrase less. as
cp [server.key] [server.key.org]
openssl rsa -in [server.key].org -out [server.key]
and gave the path of key and cert in Hue.