Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: failing while installing Kerberos KDC Server
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
failing while installing Kerberos KDC Server
- Labels:
-
Kerberos
Created on 09-13-2016 03:47 PM - edited 09-16-2022 03:39 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Getting the following message while installing the KDC Server
krb5kdc: Configuration file does not specify default realm, attempting to retrieve default realm kadmind: Configuration file does not specify default realm while initializing, aborting
Created 09-13-2016 05:18 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Sanjib Behera Some more information about your environment (such as OS, HDP version, Ambari version, etc.) would help get a better answer, but for general troubleshooting purposes have you configured a default realm for your KDC? This configuration is usually found in the krb5.conf and kdc.conf files, the location of which may depend on OS and version.
Created 09-13-2016 05:47 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It appears you have a configuration issue in your krb5.conf and kdc.conf files. I assume you are setting up an MIT KDC which is outside the scope of Ambari or HDP.
Have you tried following the MIT KDC install docs like the one at https://web.mit.edu/kerberos/krb5-devel/doc/admin/install_kdc.html?
To help to get going, here is a KDC installation script that I use for installing on CentOS. It creates a realm named EXAMPLE.COM with an admin user - principal: admin/admin@EXAMPLE.COM; password: hadoop
Created 09-14-2016 01:09 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks for you quick response @ Mike and Robert
(such as OS : UBUNTU , HDP version : 2.4.2.0, Ambari Version 2.4.0.1)
@Robert:
Thanks for sharing the MIT KDC install docs, we have been following document but stuck which creating Kerberos client using Amabari.
"Install Kerberos Client" successfully executed But got failed in " Test Kerberos Client" with following error
"stderr: 2016-09-14 18:32:03,887 - Failed to create principal, XXXXXXehdp-091416@XXX.COM - Failed to create service principal for XXXXXXhdp-091416@XXX.COM STDOUT: Authenticating as principal XXXXXXX/admin@XXX.COM with password. Password for XXXXXXXX/admin@XXX.COM: Enter password for principal "XXXXXXXXX-091416@XXX.COM": Re-enter password for principal "XXXXXXXXX-091416@XXX.COM": STDERR: WARNING: no policy specified for XXXXXXXXXhdp-091416@XXX.COM; defaulting to no policy add_principal: Operation requires ``add'' privilege while creating "XXXXXXXXhdp-091416@XXX.COM". stdout: 2016-09-14 18:32:03,866 - Processing identities... 2016-09-14 18:32:03,867 - Processing principal, bigframehdp-091416@CTS.COM"
Though we have full authority given in kadm5.acl file like */admin@XXX.COM
Please suggest and let us know if i missed out anything.
Regards
Sanjib
Created 09-14-2016 02:13 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The ACL file for the MIT KDC package on Ubuntu is typically at /etc/krb5kdc/kadm5.acl and should contain the following line to ensure the admin user has the ability to manage accounts in the KDC :
*/admin@XXX.COM *
If this is set properly, then I would think that you should have no issues.
Attached is my kdc install script for Ubuntu. Maybe it will help?
If you make any changes to kadm5.acl file, be sure to restart both the krb5-admin-server and the krb5-kdc services.
service krb5-kdc restart service krb5-admin-server restart
Created 09-15-2016 09:55 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks again for your valuable suggestion. Now i am able to enable Kerberos on Ambari.
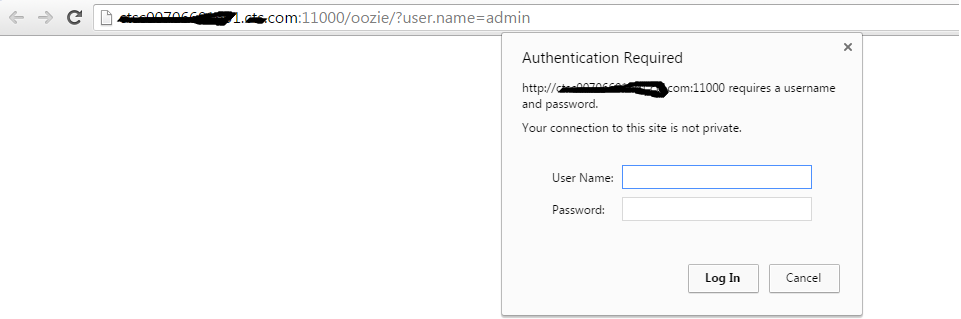
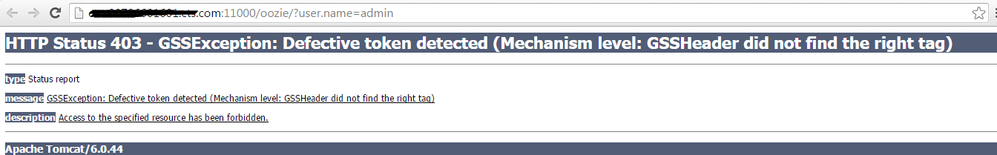
But now i am facing problem in opening the UI for some services like oozie, falcon etc ,, please find the screen shot
Error 403 GSSException: Defective token detected (Mechanism level: GSSHeader did not find the right tag)</title> </head> <body><h2>HTTP ERROR 403</h2> <p>Problem accessing /api/admin/version. Reason: <pre> GSSException: Defective token detected (Mechanism level: GSSHeader did not find the right tag)
For some services( Accumulo, Hbase,HDFS,Yarn etc) the UI is opening without asking for login information.
Could you please let me know what the may be the problem out here.
Regards
Sanjib
Created 09-15-2016 01:32 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
After enabling Kerberos via Ambari, some of the UI's are configured to require Kerberos authentication where others are not. I am not sure why not all of them are changed, but that is the way it is for now. The Hadoop UIs (HDFS, Yarn, etc...), for example, do not have Kerberos enabled by default - though there are directions on how to do it manually.
That said, once Kerberos authentication is required by a (web-based) UI, you cannot simply point your web browser at them. There are a few additional steps needed to enabled your the web browser to send Kerberos tokens. Each browser has a different set of instructions on how to do this.
See https://ping.force.com/Support/PingFederate/Integrations/How-to-configure-supported-browsers-for-Ker... for some instruction on this. However in general you need to do the following:
- Configure your local machine to communicate with the relevant KDC
- On your local machine, kinit (or similar facility) as some Kerberos identity
- Open your web browser (you may need to close and re-open your web browser for it to acknowledge the Kerberos ticket cache)
- Update the settings in your web browser to enable Kerberos authentication (see the link posted above)
- Browse to the protected URL

