Support Questions
- Cloudera Community
- Support
- Support Questions
- problem generating keytab with HTTP SPN
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
problem generating keytab with HTTP SPN
- Labels:
-
Apache Hadoop
-
Cloudera Manager
Created 08-22-2022 11:44 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello cloudera community,
we are trying to create a keytab with the main one:
"HTTP/hostname@DOMAIN.LOCAL"
with the command:
ktpass -princ HTTP/hostname@DOMAIN.LOCAL -mapuser livy-http -crypto ALL -ptype KRB5_NT_PRINCIPAL -pass password2022 -target domain.local -out c:\temp\livy-http.keytab
but I try to validate the ticket with this keytab returns the error:
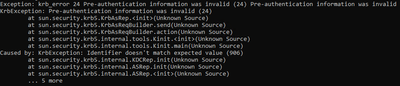
Exception: krb_error 24 Pre-authentication information was invalid (24) Pre-authentication information was invalid
KrbException: Pre-authentication information was invalid (24)
at sun.security.krb5.KrbAsRep.<init>(Unknown Source)
at sun.security.krb5.KrbAsReqBuilder.send(Unknown Source)
at sun.security.krb5.KrbAsReqBuilder.action(Unknown Source)
at sun.security.krb5.internal.tools.Kinit.<init>(Unknown Source)
at sun.security.krb5.internal.tools.Kinit.main(Unknown Source)
Caused by: KrbException: Identifier doesn't match expected value (906)
at sun.security.krb5.internal.KDCRep.init(Unknown Source)
at sun.security.krb5.internal.ASRep.init(Unknown Source)
at sun.security.krb5.internal.ASRep.<init>(Unknown Source)
... 5 more
this user "livy-http" is already created in AD and with the SPN "HTTP/hostname@DOMAIN.LOCAL" attached to it
what are we doing wrong?
Created 08-22-2022 12:28 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi sir,
This command is probably better to be evaluated in an AD forum, It is a power shell command in the AD server. Based on the stack trace you are getting, the pre-authentication is failing. Normally, this may happen because the account is enabled with pre-auth or you are using a cipher that requires pre-auth [0]
We can try to create by using only legacy ciphers:
##########################################
# How to Create a keytab from client application
##########################################
# Step 1: Type ktutil to enter prompt:
ktutil
# Step 2: At the ktutil prompt, add the authentication command below:
ktutil: add_entry -password -p livy-http@DOMAIN.LOCAL-k 1 -e arcfour-hmac-md5
# Step 3: Type password
Password for livy-http@DOMAIN.LOCAL:
# Step 4: Create Keytab file at ktutil prompt:
# ktutil: <command below to create keytab file>
wkt livy-http.keytab
# Step 5: Type quit to exit
quit
# Step 6: Verify Keytab Works Using kinit:
/usr/bin/kinit -V -kt livy-http.keytab livy-http@DOMAIN.LOCAL
[0] refer to the box checks "Do not required Kerberos Preauthentication": https://docs.informatica.com/data-integration/powercenter/10-2/security-guide/kerberos-authenticatio...
Created 08-22-2022 12:36 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Created 08-22-2022 12:43 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @JQUIROS
if create another keytab with the SPN below:
"livy-http/hostname@DOMAIN.LOCAL"
works, no problems.
the problem is when using HTTP
Created 08-22-2022 12:47 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In regards to your first question, it is on the cluster host.
For your second, We only create the keytab against the service SPN ("livy-http/hostname@DOMAIN.LOCAL"), what is the business purpose to create the keytab with HTTP principals? The service is authenticating against Service Principals, not HTTP.
Created 08-22-2022 12:51 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @JQUIROS
we need to create the HTTP SPN keytab to use in the Livy service, as described in the link below:
https://enterprise-docs.anaconda.com/en/latest/admin/advanced/config-livy-server.html
in the link above, kadmin was used, but we don't have kadmin but AD.
Created 08-22-2022 05:09 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ktpass might be purely AD, might be worth it to open an AD case if that is the only option.
Otherwise, Could you please try to create the keytab with the following ktutil commands:
add_entry -password -p HTTP@FQDN_DOMAIN.LO -k 1 -e arcfour-hmac-md5
Created 08-23-2022 08:06 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @JQUIROS
using the ktutil command it was possible to create the principal:
HTTP/hostname@DOMAIN.LOCAL
how to export keytab now?
Created 08-23-2022 08:13 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @JQUIROS
we were able to export the keytab with the command:
write_kt http.keytab
but when validating the ticket with the command:
kinit -kt http.keytab HTTP/hostnamae@DOMAIN.LOCAL
got the same error:
kinit: Preauthentication failed while getting initial credentials
Created 08-23-2022 08:58 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @yagoaparecidoti,
The error is coming directly from the Active Directory KDC, please limit the keytab to RC4 HMAC as commented earlier. Scroll up on the first post.
Then, try to kinit by using the trace to understand the issue better:
KRB5_TRACE=/dev/stdout kinit -kt http.keytab HTTP/hostnamae@DOMAIN.LOCAL