Community Articles
- Cloudera Community
- Support
- Community Articles
- How to enable Knox proxying for Zeppelin
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on 06-08-2017 11:01 PM - edited 08-17-2019 12:34 PM
This article describes how to enable Knox proxying for Zeppelin Notebook for
- Wire encrypted environment (i.e SSL is enabled for Knox and Zeppelin)
- Non Wire encrypted environments
Configuring Knox proxying for Zeppelin Notebook in Wire encrypted Environments
If you have already configured SSL for zeppelin, please proceed to section 2. If not, please read through section 1.
Section 1 : Configuring SSL for Zeppelin
Note : The steps mentioned in section 1 are just for example purpose, and the production setup may be different. Also the steps assume no client-side authentication. For client-side authentication, please follow the Zeppelin Component Guide in HDP release documents
(HDP 2.6.1 Zeppelin Component Guide : https://docs.hortonworks.com/HDPDocuments/HDP2/HDP-2.6.1/bk_zeppelin-component-guide/content/config-... )
Create keystore file, truststore file and certificates for each host on the cluster by following these steps
- Navigate to the directory where you want to create zeppelin keystore, certificate and truststore files
- Create a keystore file on zeppelin server host
keytool -genkey -alias $ZeppelinHostFqdn -keyalg RSA -keysize 1024 -dname CN=$ZeppelinHostFqdn ,OU=$OrganizationalUnit ,O=$OrganizationName,L=$City,ST=$State,C=$Country -keypass $KeyPassword -keystore $KeyStoreFile -storepass $KeyStorePassword
- Create a certificate file on zeppelin server host by exporting key info from keystore file
keytool -export -alias $ZeppelinHostFqdn -keystore $KeyStoreFile -rfc -file $CertificateFile -storepass $KeyStorePassword
- Create a truststore file on zeppelin server host
Keytool -import -noprompt -alias $ZeppelinHostFqdn -file $CertificateFile -keystore $TrustStoreFile -storepass $TrustStorePassword
- Change permissions of keystore file and truststore file to 444 and change owner to ‘zeppelin’ user
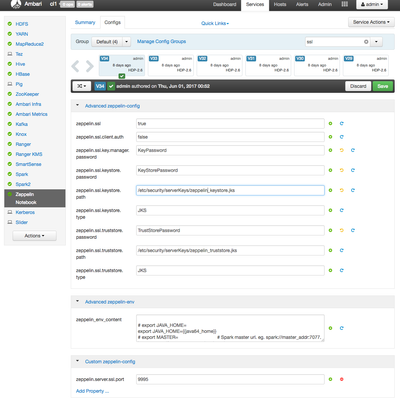
Now configure following through ambari in zeppelin-config section
zeppelin.ssl : true zeppelin.server.ssl.port : $ZeppelinSSLPort zeppelin.ssl.client.auth: false (true in case of client-side authentication enabled) zeppelin.ssl.truststore.type : JKS zeppelin.ssl.truststore.path : $TrustStoreFile zeppelin.ssl.truststore.password : $TrustStorePassword zeppelin.ssl.keystore.path : $KeyStoreFile zeppelin.ssl.keystore.password : $KeyStorePassword zeppelin.ssl.key.manager.password : $KeyPassword
Section 2: Configuring Knox Proxying
- Copy the zeppelin certificate file onto Knox gateway host
- Add zeppelin certificate file into java cacert store of the Knox gateway host using following command on Knox gateway host (This is a way to configure knox gateway to trust incoming request from zeppelin server)
keytool -import -file $CertificateFile -alias $ZeppelinHostFqdn -keystore $JavaCacertPath
Where $JavaCacertPath is typically : path to your java installation dir + /jre/lib/security/cacerts
You will get a prompt asking for the keystore password (i.e java cacert store password) and the default value is ‘changeit’
- Create a topology ui.xml file in $KnoxConfDir/topologies directory on the knox gateway host, and configure the Zeppelin UI using following snippet
<service>
<role>ZEPPELIN</role>
<url>https://$ZeppelinHostFqdn:$ZeppelinSSLPort</url>
</service>
<service>
<role>ZEPPELINUI</role>
<url>https://$ZeppelinHostFqdn:$ZeppelinSSLPort</url>
</service>
<service>
<role>ZEPPELINWS</role>
<url>wss://$ZeppelinHostFqdn:$ZeppelinSSLPort/ws</url>
</service>
Note: make sure to use FQDN of zeppelin host name, as that is the ‘key’(or alias) that we have used in Section 1 to create zeppelin certificate
- There is no need to restart either knox gateway or Zeppelin.
Configuring KNOX proxying for Zeppelin Notebook in non Wire encrypted Environments
- Create a topology ui.xml file in $KnoxConfDir/topologies directory on the knox gateway host, and configure the Zeppelin UI using following snippet
<service>
<role>ZEPPELIN</role>
<url>http://$ZeppelinHostFqdn:$ZeppelinPort</url>
</service>
<service>
<role>ZEPPELINUI</role>
<url>http://$ZeppelinHostFqdn:$ZeppelinPort</url>
</service>
- There is no need to restart either knox gateway or Zeppelin
Using KNOX Proxying For Zeppelin and currently known issues with HDP-2.6.1 release
Once the configurations are finished, you can access Zeppelin UI via Knox proxy using following URL:
https://<knox gateway host>:8443/gateway/ui/zeppelin/
( Note: Please don’t forget to append a trailing ‘/’ with the URL. This bug is work in progress)
The other bug that is still work in progress is that if a user logs out from Zeppelin while using knox’s proxy URL , he does not remain on the Zeppelin’s Login page anymore. ( https://issues.apache.org/jira/browse/ZEPPELIN-2601) The user needs to type the URL again in browser to go back to the Login page