Community Articles
- Cloudera Community
- Support
- Community Articles
- NiFi User Authentication with LDAP
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on 12-19-2015 07:51 PM - edited 08-17-2019 01:37 PM
NiFi User Authentication with LDAP in HW Sandbox
Prerequisite
1) Assuming you already have NiFi-0.4.0/HDF-1.1 downloaded on your HW Sandbox, else execute below after ssh connectivity to sandbox is established.
cd /opt/ wget http://public-repo-1.hortonworks.com/HDF/1.1.0.0/nifi-1.1.0.0-10-bin.zip unzip nifi-1.1.0.0-10-bin.zip
2) Make sure Knox is installed on your sandbox and demo LDAP is started via Ambari
Steps:
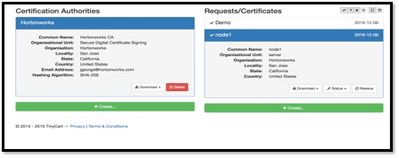
1. I already created Certification Authorities and client certificates at www.tinycert.org
How to create certificates as well configurations can be found in below article:
https://community.hortonworks.com/content/kbentry/886/securing-nifi-step-by-step.html
If you are too lazy to create them, try with mine 🙂 [Attached as certificates.zip]
- Use cert-browser.pfx to load into browser to be a NiFi administrator 'DEMO'
- Upload other two certificates to Sandbox under '/root/scripts/' and execute below commands, while executing last command enter 'hadoop' as password and 'yes' when asked if it can be trusted.
# cd /root/scripts/ # mv cert.pfx cert.p12 # openssl x509 -outform der -in cacert.pem -out cacert.der # keytool -import -keystore cacert.jks -file cacert.der
2. My keystore is saved as ‘/root/scripts/cert.p12’ and a truststore is saved as ‘/root/scripts/cacert.jks’. and password is set as hadoop.
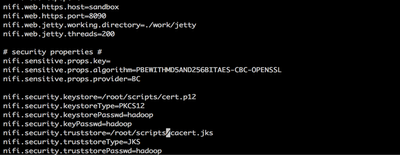
3. Below are the configuration updates you have to do in nifi.properties file in sandbox:
# vi /opt/nifi-1.1.0.0-10/conf/nifi.properties
4. Once opened in editor update below properties to given values [updating https port and certificate details]:
nifi.web.http.host= nifi.web.http.port= nifi.web.https.host=sandbox nifi.web.https.port=9090 nifi.security.keystore=/root/scripts/cert.p12 nifi.security.keystoreType=PKCS12 nifi.security.keystorePasswd=hadoop nifi.security.keyPasswd=hadoop nifi.security.truststore=/root/scripts/cacert.jks nifi.security.truststoreType=JKS nifi.security.truststorePasswd=hadoop nifi.login.identity.provider.configuration.file=./conf/login-identity-providers.xml nifi.security.user.login.identity.provider=ldap-provider
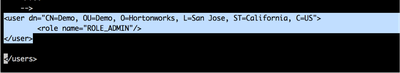
5. Now configure the authorized users in ‘authorized-users.xml’ file, configuration of user is based on certificate. Configure it exactly as you have in your certificate. Following is my configuration:
vi /opt/nifi-1.1.0.0-10/conf/authorized-users.xml
<user dn="CN=Demo, OU=Demo, O=Hortonworks, L=San Jose, ST=California, C=US"> <role name="ROLE_ADMIN"/> </user>
6. Above configuration is to login as NiFi Administrator, every other users can be pulled from LDAP after this administrator assigns roles on request.
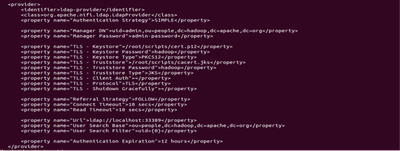
7. Configure ./conf/login-identity-providers.xml as below with reference to Knox Demo LDAP Server.
<provider>
<identifier>ldap-provider</identifier>
<class>org.apache.nifi.ldap.LdapProvider</class>
<property name="Authentication Strategy">SIMPLE</property>
<property name="Manager DN">uid=admin,ou=people,dc=hadoop,dc=apache,dc=org</property>
<property name="Manager Password">admin-password</property>
<property name="TLS - Keystore">/root/scripts/cert.p12</property>
<property name="TLS - Keystore Password">hadoop</property>
<property name="TLS - Keystore Type">PKCS12</property>
<property name="TLS - Truststore">/root/scripts/cacert.jks</property>
<property name="TLS - Truststore Password">hadoop</property>
<property name="TLS - Truststore Type">JKS</property>
<property name="TLS - Client Auth"></property>
<property name="TLS - Protocol">TLS</property>
<property name="TLS - Shutdown Gracefully"></property>
<property name="Referral Strategy">FOLLOW</property>
<property name="Connect Timeout">10 secs</property>
<property name="Read Timeout">10 secs</property>
<property name="Url">ldap://localhost:33389</property>
<property name="User Search Base">ou=people,dc=hadoop,dc=apache,dc=org</property>
<property name="User Search Filter">uid={0}</property>
<property name="Authentication Expiration">12 hours</property>
</provider> 8. Once configured, restart NiFi server.
# /opt/nifi-1.1.0.0-10/bin/nifi.sh restart
9. Now say open ‘Chrome’ browser and load client certificate associated with ADMIN user and login to secure https url of NiFi running on sandbox:
10. When asked, confirm for security exception and proceed. Now you are securely logged in as Demo user with admin privileges. You can now grant access to any user requesting access who are part of LDAP Directory.
11. Open another browser say ‘Safari’ to establish another session
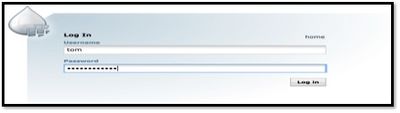
It will popup below screen for login, enter credentials for accounts part of LDAP. Below are credentials part of knox demo ldap we have configured.
tom/tom-password admin/admin-password sam/sam-password guest/guest-password
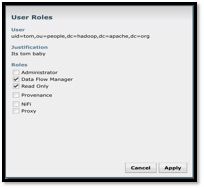
12. Enter the password and hit login, enter justification and it will show up below screen that request is pending with Admin who already have access using certificates.
13. Now go back to chrome browser where ‘Demo’ user is NiFi Administrator and assign role to Tom
14. Go back to the old session as tom in safari, refresh the browser and you will be logged in as tom with privileges assigned by NiFi administrator. You can test if for other users as well.
Created on 01-18-2016 12:48 PM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for sharing!
Created on 04-05-2016 08:33 PM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for the article. I've tried to implement this but messed up something. How can I remove the admin user from Nifi's repository? After I've imported the client certificate into the browser, it requested that I submit a request for authorizing access and now it's stuck because the admin user status is "request pending".
Appreciate any hints. Thanks,
Created on 04-06-2016 04:49 PM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Issues such as the one in my question above can be resolved by stopping Nifi and then removing the `database_repository/nifi-users.h2.db` file and starting fresh again.
Created on 08-12-2016 04:06 PM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Jobin George I configured for ldap as above but only thing is I connected it with AD. SSL works great but I don't see any trace of ldap authentication happening in logs. Certificate based authentication is working but not ldap. I have used ldap-provider and configured the same. Is there any property or anything that needs to be enabled for ldap authentication to be triggered other than using ldap-provider ?
Created on 08-12-2016 06:22 PM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Deep Doradla,
Can you verify if you have ssl certificate details provided in the step 7? as well as all the tags are in step7 above are in place?
Thanks,
Jobin
Created on 08-12-2016 06:38 PM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Jobin George it is working now. I am able to authenticate via AD. I had made a small mistake and corrected it.
Thanks for your quick response and also for the great tutorial.
Thanks
Deep
Created on 08-15-2016 10:58 PM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have LDAP setup and working for me. However whenever I go to /nifi/login page, it throws an exception in User logs. Though it works just fine i.e I can login and logout etc. Just wondering if you have seen this exception (is this by-design?) [Already reported this issue]
2016-08-15 15:43:00,046 ERROR [NiFi Web Server-94] o.a.n.w.s.NiFiAuthenticationFilter Unable to authorize: An Authentication object was not found in the SecurityContext
Created on 08-30-2016 10:00 PM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Jobin George Thank you for the tutorial.
So, I am trying to get Nifi user authentication by binding it to my company's LDAP server. So, I gave in the details in xml file and got the certs from tinycert. I added the browser cert to the login Keychain(Mac). But, when I try to run Nifi and then access through browser, it doesn't load and it says "the site can't be reached". It worked well when I ran Nifi with http. Is it because I am running Nifi from an Ubuntu VM and accessing the browser through my Mac (I don't really think that would be the issue)? Or is it because of proxy server (Again, that wasn't a problem when i ran Nifi as a non-secure instance on an http port)? Any tips would be greatly appreciated. 🙂
Created on 09-15-2023 04:40 AM - edited 09-15-2023 04:42 AM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have already set up NiFi to use LDAP but need to log in as admin. The certificate was not generated by me and I can't view the content because it is protected How can I configure my admin user to log in as NiFi administrator? Your assisted will be appreciated as I am new to NiFi.
Created on 12-11-2023 08:35 AM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
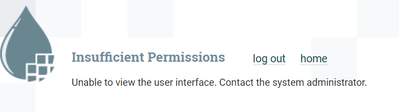
though i gave the permission to view user interface, i am still facing this issue.