Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: Authorization configured for nifi resources i...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Authorization configured for nifi resources in ranger not working properly
- Labels:
-
Apache NiFi
-
Apache Oozie
-
Apache Ranger
Created on
09-20-2023
11:19 AM
- last edited on
09-21-2023
07:01 AM
by
VidyaSargur
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Currently I have configured apache NiFi with Ranger as per discussed in this thread. Ranger NiFi plugin is able to pull resources from ranger and auto suggest in ranger nifi service definition UI. But I don't think the authorizations works properly.
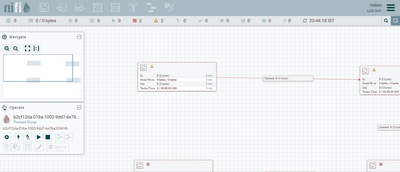
Only the /flow resource specifier has an impact. When I remove that specifier user is not able to view the screen and when I add it back the user is logging back into the Nifi UI. Rest of the resources including processors , ports etc. seems to be unclickable or accessible no matter any of the resource specifier I provide in ranger. I even tried the wild card * but still doesn't seems to work. The UI looks as below.
The Ranger Authorizers file is shown below
<userGroupProvider>
<identifier>file-user-group-provider</identifier>
<class>org.apache.nifi.authorization.FileUserGroupProvider</class>
<property name="Users File">./conf/users.xml</property>
<property name="Legacy Authorized Users File"></property>
<property name="Initial User Identity 1"></property>
</userGroupProvider>
<accessPolicyProvider>
<identifier>file-access-policy-provider</identifier>
<class>org.apache.nifi.authorization.FileAccessPolicyProvider</class>
<property name="User Group Provider">file-user-group-provider</property>
<property name="Authorizations File">./conf/authorizations.xml</property>
<property name="Initial Admin Identity"></property>
<property name="Legacy Authorized Users File"></property>
<property name="Node Identity 1"></property>
<property name="Node Group"></property>
</accessPolicyProvider>
<authorizer>
<identifier>ranger-provider</identifier>
<class>org.apache.nifi.ranger.authorization.RangerNiFiAuthorizer</class>
<property name="Ranger Audit Config Path">./conf/ranger-nifi-audit.xml</property>
<property name="Ranger Security Config Path">./conf/ranger-nifi-security.xml</property>
<property name="Ranger Service Type">nifi</property>
<property name="Ranger Application Id">nifi</property>
<property name="Ranger Admin Identity">CN=localhost, OU=NIFI</property>
<property name="Ranger Kerberos Enabled">false</property>
</authorizer>
The initial admin is specified for resource access through user present in the certificate.
@MattWho any thoughts on this?
Created 09-20-2023 12:50 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@pacman
Are you sure NiFi is still successfully downloading the policy json when you make changes in Ranger?
Within the ranger-nifi-security.xml file there is a configured "ranger.plugin.nifi.policy.cache" directory.
Within that directory you will find the NiFi service .json policy file downloaded on the NiFi node. What is found in this file is what NiFi uses. Can you share that json file?
Have you configured any security zones in Ranger (NiFi does not support this)?
Have you unchecked the "delegate admin" check box on the policies in Ranger?
Matt
Created 09-20-2023 11:57 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @pacman
Thank s for sharing your authorizers.xml configuration.
While you have both the file-user-group-provider and file-access-policy-provider configured in your authorizers.xml, your configured Ranger-provider does not use them. So these do nothing for you.
When it comes to NiFi Resource Identifiers, they are very granular.
The /flow NiFi Resource Identifier simply grants the authorized user access to the UI. It does not grant user ability to view (so you see no processor details or ability to open processor configuration to view it, modify, add, or delete any components. This is why everything on the canvas is ghosted (All users will always see ghosted components, it helps prevent different teams from building dataflows on top of one another).
NiFi does not fully support wildcard in all NiFi Resource Identifiers, "/*" should work, but I would not recommend it. The intent here is to correctly and securely control these granular access controls.
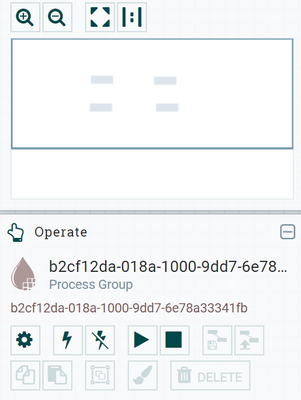
When you access NiFi's UI, you land in the root Process Group (NiFi builds this root process group for you when NiFi is first launched). Just like any other component a PG is assigned uuid. With nothing selected you will see the root PG uuid displayed in the operate panel to the left side of the canvas. Go ahead and copy that uuid. Go over to the Ranger and create a new policy in your NiFi Ranger service. In the NiFi Resource Identifier box paste that uuid. You should then be presented with available NiFi Resource Identifiers associated that PG.
NiFi components inherit permissions from PGs. If grant user against a policy on that PG, all components created within that PG will inherit that same level of permissions unless you explicitly set a different policy on the sub component(s) or child process group(s). So if you give grant your user READ and Write on "/process-groups/<root PG uuid>", your user will be able to view and modify this process groups configuration and configuration of all components within this PG.
Granting your user READ and WRITE on "/data/process-groups/<root pg uuid>" with allow you user to view content of FlowFile passed through components within this PG.
The NiFi /resources endpoint returns all the available policies even those that would not be applicable when Ranger is managing authorization. So adding any authorizations related to NiFi Resource Identifiers that contain "policies" make no sense and are not necessary for example.
I created community articles that maps the /NiFi Resource Identifiers used in Ranger to the NiFi user interface human readable policies you would have seen prior to switching to to Ranger as your authorizer (also describes what each grants the user).
https://community.cloudera.com/t5/Community-Articles/NiFi-Ranger-based-policy-descriptions/ta-p/2465...
https://community.hortonworks.com/articles/226382/nifi-restricted-components-policy-descriptions.htm...
These should help you with your journey here.
If you found any of the suggestions/solutions provided helped you with your issue, please take a moment to login and click "Accept as Solution" on one or more of them that helped.
Thank you,
Matt
Created 09-20-2023 12:21 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
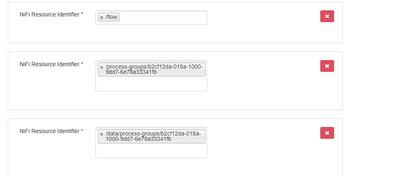
@MattWho I had already configured the process groups endpoints to the resource identifiers, all the four shown in nifi ranger plugin.
The identifier processor group shown in nifi is below.
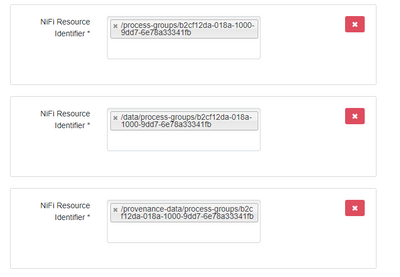
Some of the resource identifiers I configured on nifi ranger service is shown below.
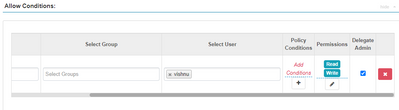
The corresponding allow conditions are shown below.
This was the configurations I was testing in ranger service definition which I believe is what is specified in the answer.
But as I said the /flow resource specifier works perfectly fine.
Is there any other point where there is a chance of this going wrong or is there something wrong in whatever I did?
Created 09-20-2023 12:50 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@pacman
Are you sure NiFi is still successfully downloading the policy json when you make changes in Ranger?
Within the ranger-nifi-security.xml file there is a configured "ranger.plugin.nifi.policy.cache" directory.
Within that directory you will find the NiFi service .json policy file downloaded on the NiFi node. What is found in this file is what NiFi uses. Can you share that json file?
Have you configured any security zones in Ranger (NiFi does not support this)?
Have you unchecked the "delegate admin" check box on the policies in Ranger?
Matt
Created 09-20-2023 01:01 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@MattWho Thank you once again for making my life easier . Looks like the problem is caused by setting security zones in ranger. Once I created polices outside the security zone things are working fine. Is there any reason nifi doesn't support security zones? And do you have any idea why only /flow was working inside security zone?
Created 09-20-2023 01:12 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@pacman
NiFi has never supported security zones. There is no concept of zones in NiFi. NiFi's established policies are extremely granular all the way to the individual low level components (processors, controller services, etc) level. You have that level of individual user and group control within NiFi.
NiFi also does not support "deny" ranger policies. A user is denied all except what they are authorized for directly or through inheritance.
As far as to why /flow was working within a security zone... I have no idea. Would need to see that downloaded policy json and maybe I could figure out why???
Glad I was able to help you get going with your Ranger integration with NiFi.
Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
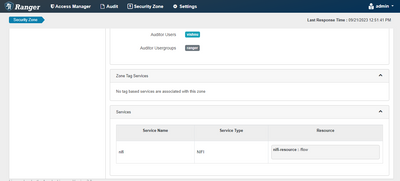
Looks like security zone is also working with nifi when configuring with ranger provided all the resource identifiers that needs to be added is also added in the security zone that we are creating. Probably this is a basic that I left out.
Currently the resources identifiers in policies as shown below.
But the security zone has only /flow as shown below
The policies json corresponding to the above configuration is shown below.
{"serviceName":"nifi","serviceId":1,"policyVersion":140,"policyUpdateTime":"20230921-12:51:41.126-+0530","policies":[],"serviceDef":{"name":"nifi","displayName":"nifi","implClass":"org.apache.ranger.services.nifi.RangerServiceNiFi","label":"NIFI","description":"NiFi","options":{"enableDenyAndExceptionsInPolicies":"false"},"configs":[{"itemId":400,"name":"nifi.url","type":"string","mandatory":true,"defaultValue":"http://localhost:8080/nifi-api/resources","uiHint":"{\"TextFieldWithIcon\":true, \"info\": \"The URL of the NiFi REST API that provides the available resources.\"}","label":"NiFi URL"},{"itemId":410,"name":"nifi.authentication","type":"enum","subType":"authType","mandatory":true,"defaultValue":"NONE","label":"Authentication Type"},{"itemId":411,"name":"nifi.ssl.use.default.context","type":"bool","subType":"YesTrue:NoFalse","mandatory":true,"defaultValue":"false","uiHint":"{\"TextFieldWithIcon\":true, \"info\": \"If true, then Ranger\u0027s keystore and truststore will be used to communicate with NiFi. If false, the keystore and truststore properties must be provided.\"}","label":"Use Ranger\u0027s Default SSL Context"},{"itemId":500,"name":"nifi.ssl.keystore","type":"string","mandatory":false,"label":"Keystore"},{"itemId":510,"name":"nifi.ssl.keystoreType","type":"string","mandatory":false,"label":"Keystore Type"},{"itemId":520,"name":"nifi.ssl.keystorePassword","type":"password","mandatory":false,"label":"Keystore Password"},{"itemId":530,"name":"nifi.ssl.truststore","type":"string","mandatory":false,"label":"Truststore"},{"itemId":540,"name":"nifi.ssl.truststoreType","type":"string","mandatory":false,"label":"Truststore Type"},{"itemId":550,"name":"nifi.ssl.truststorePassword","type":"password","mandatory":false,"label":"Truststore Password"},{"itemId":560,"name":"ranger.plugin.audit.filters","type":"string","mandatory":false,"defaultValue":"[]","label":"Ranger Default Audit Filters"}],"resources":[{"itemId":100,"name":"nifi-resource","type":"string","level":10,"mandatory":true,"lookupSupported":true,"recursiveSupported":false,"excludesSupported":false,"matcher":"org.apache.ranger.plugin.resourcematcher.RangerDefaultResourceMatcher","matcherOptions":{"wildCard":"true","ignoreCase":"true"},"label":"NiFi Resource Identifier","description":"NiFi Resource","accessTypeRestrictions":[],"isValidLeaf":true}],"accessTypes":[{"itemId":100,"name":"READ","label":"Read","impliedGrants":[]},{"itemId":200,"name":"WRITE","label":"Write","impliedGrants":[]}],"policyConditions":[{"itemId":1,"name":"_expression","evaluator":"org.apache.ranger.plugin.conditionevaluator.RangerScriptConditionEvaluator","evaluatorOptions":{"ui.isMultiline":"true"},"uiHint":"{ \"isMultiline\":true }","label":"Enter boolean expression","description":"Boolean expression"}],"contextEnrichers":[],"enums":[{"itemId":1,"name":"authType","elements":[{"itemId":1,"name":"NONE","label":"None"},{"itemId":2,"name":"SSL","label":"SSL"}],"defaultIndex":0}],"dataMaskDef":{"maskTypes":[],"accessTypes":[],"resources":[]},"rowFilterDef":{"accessTypes":[],"resources":[]},"id":10,"guid":"a23a32e1-4b74-4cbf-8b60-3e161d748954","isEnabled":true,"createTime":"20230912-17:43:16.455-+0530","updateTime":"20230912-17:43:16.798-+0530","version":1},"auditMode":"audit-default","securityZones":{"nifi":{"zoneName":"nifi","resources":[{"nifi-resource":["/flow"]}],"policies":[{"service":"nifi","name":"nifi-zone-policy","policyType":0,"policyPriority":0,"isAuditEnabled":true,"resources":{"nifi-resource":{"values":["/proxy"],"isExcludes":false,"isRecursive":false}},"additionalResources":[{"nifi-resource":{"values":["/flow"],"isExcludes":false,"isRecursive":false}},{"nifi-resource":{"values":["/process-groups/b2cf12da-018a-1000-9dd7-6e78a33341fb"],"isExcludes":false,"isRecursive":false}},{"nifi-resource":{"values":["/data/process-groups/b2cf12da-018a-1000-9dd7-6e78a33341fb"],"isExcludes":false,"isRecursive":false}}],"policyItems":[{"accesses":[{"type":"READ","isAllowed":true},{"type":"WRITE","isAllowed":true}],"users":["vishnu"],"groups":[],"roles":["ranger_users"],"conditions":[],"delegateAdmin":true}],"denyPolicyItems":[],"allowExceptions":[],"denyExceptions":[],"dataMaskPolicyItems":[],"rowFilterPolicyItems":[],"serviceType":"nifi","options":{},"validitySchedules":[],"policyLabels":[],"zoneName":"nifi","isDenyAllElse":false,"id":4,"guid":"b4577f50-f5fc-40ae-b745-7ec9380e2705","isEnabled":true,"version":13}],"containsAssociatedTagService":false}}}
Since only flow was in the security zone the other configurations was not working. If I add other two resource specifiers in the nifi security zone, then then things are working properly. Also not sure if there is some other thing that you mentioned as security zone.