Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: Connection refused error ! whlie I try enable ...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Connection refused error ! whlie I try enable SSL in Nifi
- Labels:
-
Apache NiFi
Created on 08-03-2017 08:52 AM - edited 08-17-2019 09:59 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am using HDF3.0
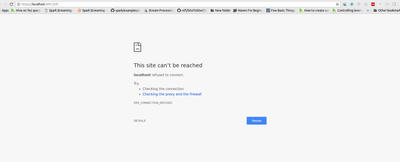
I try to enable SSL in Nifi. I follow this link here. I create client certificate and import keystore.p12 in Chrome browser and nifi-cert.pem as trusted CA. After restart Nifi, Now I open Nifi UI using the Quicklink in Ambari. But i got connection refused error
Created 08-03-2017 12:55 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In order to access a secured NiFi's UI, successful user authentication and authorization must occur.
In HDF a NiFI CA is installed that takes care of building valid keystores and truststores for your NiFi nodes, but it does not create user certificates for you.
Typically the above error indicates NiFi did not trust the client certificate it was passed or a client certificate was not passed at all.
I would suggest staring by getting verbose outputs of your NiFi keystore.jks, truststore.jks, and users keystore.p12.
The verbose output for each of these can be obtained using keytool.
./keytool -v --list -keystore <jks or p12 keystore file>
In your Keystore.jks used by the NiFi server, you will see a single entry with two certificates included in it:
Specifically you are looking for the "PrivateKeyEntry". This PrivateKeyEntry will show a user DN (It will be in the form of CN=<server FQDN>, OU=NIFI). You will then see an issuer line which will also have a DN for the NiFi CA. This PrivateKeyEntry should have an extended key usage that allows the key to be used for both client auth and server auth. Something else (not related to your issue) i noticed was your browser URL is "localhost". The NIFi CA will generate a server certificate based off the hostname of the server and not localhost. This will require you to add an exception in your browser at some point. (This is because the cert passed to your browser from your NiFi server will say it belongs to server XYZ, but your browsers knows it was trying to connect to localhost. So it appears as a man in the middle type attack (some en-point using another end-points cert).
In your truststore.jks used on your NiFi servers, you will see a single certificate. It will be a "TrustedCertEntry" for the NiFi CA. The truststore.jks file can contain 1 to many trusted cert entries. Each trusted cert entry is derived from the public key of a CA or self-signed cert. When a client (user or another server) negotiates a connection with the server a TLS handshake occurs. As part of this negotiation, the server expects to receive a client certificate which it can trust. If a trusted client cert is not received, the connection is typically closed by the server.
Your client keystore.p12 file will also need to contain a PrivateKeyEntry. In TLS negotiation that occurs with the server, the DN associated to that PrivateKeyEntry is passed to the server. If that certificate was self-signed, the truststore would need to contain the public key for that certificate as a TrustedCertEntry before that certificate will be accepted for authentication.
Beyond authentication is authorization, but it does not appear you are getting that far yet.
Thanks,
Matt
Created 08-04-2017 12:59 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Matt Clarke