Support Questions
- Cloudera Community
- Support
- Support Questions
- How to configure Managed Ranger Authorizer for NiF...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to configure Managed Ranger Authorizer for NiFi LDAP Group based authorization
- Labels:
-
Apache NiFi
-
Apache Ranger
Created on 03-07-2018 05:29 PM - edited 08-18-2019 03:02 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
Is there a document that details on how to configure LDAP Group Authorization for NiFi - Ranger? This is for HDF 3.1.1 or NiFi 1.5
With the default configuration, NiFi still needs the policies to be defined for every user. Group level policies doesn't take into effect. Assuming that there is some configuration that is missing to the configs.
EDIT:
userGroupProvider
<userGroupProvider>
<identifier>ldap-user-group-provider</identifier>
<class>org.apache.nifi.ldap.tenants.LdapUserGroupProvider</class>
<property name="Authentication Strategy">SIMPLE</property>
<property name="Manager DN">uid=admin,cn=blah,cn=blah,dc=blah,dc=com</property>
<property name="Manager Password">blah</property>
<property name="TLS - Keystore"></property>
<property name="TLS - Keystore Password"></property>
<property name="TLS - Keystore Type"></property>
<property name="TLS - Truststore"></property>
<property name="TLS - Truststore Password"></property>
<property name="TLS - Truststore Type"></property>
<property name="TLS - Client Auth"></property>
<property name="TLS - Protocol"></property>
<property name="TLS - Shutdown Gracefully"></property>
<property name="Referral Strategy">FOLLOW</property>
<property name="Connect Timeout">10 secs</property>
<property name="Read Timeout">10 secs</property>
<property name="Url">ldap://blah.ldap.com:389</property>
<property name="Page Size"></property>
<property name="Sync Interval">30 mins</property>
<property name="User Search Base">cn=users,cn=accounts,dc=blah,dc=blah,dc=com</property>
<property name="User Object Class">person</property>
<property name="User Search Scope">SUBTREE</property>
<property name="User Search Filter">(uid={0})</property>
<property name="User Identity Attribute">USE_USERNAME</property>
<property name="User Group Name Attribute"></property>
<property name="User Group Name Attribute - Referenced Group Attribute"></property>
<property name="Group Search Base">cn=groups,cn=accounts,dc=blah,dc=blah,dc=com</property>
<property name="Group Object Class">groupofnames</property>
<property name="Group Search Scope">SUBTREE</property>
<property name="Group Search Filter">(cn={0})</property>
<property name="Group Name Attribute">cn</property>
<property name="Group Member Attribute">member</property>
<property name="Group Member Attribute - Referenced User Attribute">uid</property>
</userGroupProvider>Sample User - LDAP
Sample Group - LDAP
Created 03-07-2018 05:50 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You will need to change the default authorizer in "Advanced nifi-authorizers-env" NiFi config section via Ambari.
You will want to replace the default authorizer:
<authorizer>
<identifier>{{nifi_authorizer}}</identifier>
{% if has_ranger_admin and enable_ranger_nifi %}
<class>org.apache.nifi.ranger.authorization.RangerNiFiAuthorizer</class>
<property name="Ranger Audit Config Path">{{nifi_config_dir}}/ranger-nifi-audit.xml</property>
<property name="Ranger Security Config Path">{{nifi_config_dir}}/ranger-nifi-security.xml</property>
<property name="Ranger Service Type">nifi</property>
<property name="Ranger Application Id">nifi</property>
<property name="Allow Anonymous">true</property>
<property name="Ranger Admin Identity">{{ranger_admin_identity}}</property>
{% if security_enabled %}
<property name="Ranger Kerberos Enabled">true</property>
{% else %}
<property name="Ranger Kerberos Enabled">false</property>
{% endif %}
{% else %}
<class>org.apache.nifi.authorization.FileAuthorizer</class>
<property name="Authorizations File">{{nifi_flow_config_dir}}/authorizations.xml</property>
<property name="Users File">{{nifi_flow_config_dir}}/users.xml</property>
<property name="Initial Admin Identity">{{nifi_initial_admin_id}}</property>
<property name="Legacy Authorized Users File"></property>
{% endif %}
{{nifi_ssl_config_content}}
</authorizerwith the something similar to the following:
<userGroupProvider>
<identifier>ldap-user-group-provider</identifier>
<class>org.apache.nifi.ldap.tenants.LdapUserGroupProvider</class>
<property name="Authentication Strategy">SIMPLE</property>
<property name="Manager DN"></property>
<property name="Manager Password"></property>
<property name="TLS - Keystore"></property>
<property name="TLS - Keystore Password"></property>
<property name="TLS - Keystore Type"></property>
<property name="TLS - Truststore"></property>
<property name="TLS - Truststore Password"></property>
<property name="TLS - Truststore Type"></property>
<property name="TLS - Client Auth"></property>
<property name="TLS - Protocol"></property>
<property name="TLS - Shutdown Gracefully"></property>
<property name="Referral Strategy">FOLLOW</property>
<property name="Connect Timeout">10 secs</property>
<property name="Read Timeout">10 secs</property>
<property name="Url"></property>
<property name="Page Size"></property>
<property name="Sync Interval">30 mins</property>
<property name="User Search Base"></property>
<property name="User Object Class"></property>
<property name="User Search Scope">ONE_LEVEL</property>
<property name="User Search Filter"></property>
<property name="User Identity Attribute"></property>
<property name="User Group Name Attribute"></property>
<property name="User Group Name Attribute - Referenced Group Attribute"></property>
<property name="Group Search Base"></property>
<property name="Group Object Class"></property>
<property name="Group Search Scope">ONE_LEVEL</property>
<property name="Group Search Filter"></property>
<property name="Group Name Attribute"></property>
<property name="Group Member Attribute"></property>
<property name="Group Member Attribute - Referenced User Attribute"></property>
</userGroupProvider>
<authorizer>
<identifier>ranger-authorizer</identifier>
<class>org.apache.nifi.ranger.authorization.ManagedRangerAuthorizer</class>
<property name="User Group Provider">ldap-user-group-provider</property>
<property name="Ranger Audit Config Path"><path to nifi conf dir>/ranger-nifi-audit.xml</property>
<property name="Ranger Security Config Path"><path to nifi conf dir>/ranger-nifi-security.xml</property>
<property name="Ranger Service Type">nifi</property>
<property name="Ranger Application Id">nifi</property>
<property name="Allow Anonymous">true</property>
<property name="Ranger Admin Identity"></property>
<property name="Ranger Kerberos Enabled">false</property>
</authorizer>
Details on the "ldap-user-group-provider can be found in the nifi admin guide:
Make sure the <userGroupProvider> comes before the <authorizer> in this configuration.
Thanks,
Matt
Created 03-07-2018 05:50 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You will need to change the default authorizer in "Advanced nifi-authorizers-env" NiFi config section via Ambari.
You will want to replace the default authorizer:
<authorizer>
<identifier>{{nifi_authorizer}}</identifier>
{% if has_ranger_admin and enable_ranger_nifi %}
<class>org.apache.nifi.ranger.authorization.RangerNiFiAuthorizer</class>
<property name="Ranger Audit Config Path">{{nifi_config_dir}}/ranger-nifi-audit.xml</property>
<property name="Ranger Security Config Path">{{nifi_config_dir}}/ranger-nifi-security.xml</property>
<property name="Ranger Service Type">nifi</property>
<property name="Ranger Application Id">nifi</property>
<property name="Allow Anonymous">true</property>
<property name="Ranger Admin Identity">{{ranger_admin_identity}}</property>
{% if security_enabled %}
<property name="Ranger Kerberos Enabled">true</property>
{% else %}
<property name="Ranger Kerberos Enabled">false</property>
{% endif %}
{% else %}
<class>org.apache.nifi.authorization.FileAuthorizer</class>
<property name="Authorizations File">{{nifi_flow_config_dir}}/authorizations.xml</property>
<property name="Users File">{{nifi_flow_config_dir}}/users.xml</property>
<property name="Initial Admin Identity">{{nifi_initial_admin_id}}</property>
<property name="Legacy Authorized Users File"></property>
{% endif %}
{{nifi_ssl_config_content}}
</authorizerwith the something similar to the following:
<userGroupProvider>
<identifier>ldap-user-group-provider</identifier>
<class>org.apache.nifi.ldap.tenants.LdapUserGroupProvider</class>
<property name="Authentication Strategy">SIMPLE</property>
<property name="Manager DN"></property>
<property name="Manager Password"></property>
<property name="TLS - Keystore"></property>
<property name="TLS - Keystore Password"></property>
<property name="TLS - Keystore Type"></property>
<property name="TLS - Truststore"></property>
<property name="TLS - Truststore Password"></property>
<property name="TLS - Truststore Type"></property>
<property name="TLS - Client Auth"></property>
<property name="TLS - Protocol"></property>
<property name="TLS - Shutdown Gracefully"></property>
<property name="Referral Strategy">FOLLOW</property>
<property name="Connect Timeout">10 secs</property>
<property name="Read Timeout">10 secs</property>
<property name="Url"></property>
<property name="Page Size"></property>
<property name="Sync Interval">30 mins</property>
<property name="User Search Base"></property>
<property name="User Object Class"></property>
<property name="User Search Scope">ONE_LEVEL</property>
<property name="User Search Filter"></property>
<property name="User Identity Attribute"></property>
<property name="User Group Name Attribute"></property>
<property name="User Group Name Attribute - Referenced Group Attribute"></property>
<property name="Group Search Base"></property>
<property name="Group Object Class"></property>
<property name="Group Search Scope">ONE_LEVEL</property>
<property name="Group Search Filter"></property>
<property name="Group Name Attribute"></property>
<property name="Group Member Attribute"></property>
<property name="Group Member Attribute - Referenced User Attribute"></property>
</userGroupProvider>
<authorizer>
<identifier>ranger-authorizer</identifier>
<class>org.apache.nifi.ranger.authorization.ManagedRangerAuthorizer</class>
<property name="User Group Provider">ldap-user-group-provider</property>
<property name="Ranger Audit Config Path"><path to nifi conf dir>/ranger-nifi-audit.xml</property>
<property name="Ranger Security Config Path"><path to nifi conf dir>/ranger-nifi-security.xml</property>
<property name="Ranger Service Type">nifi</property>
<property name="Ranger Application Id">nifi</property>
<property name="Allow Anonymous">true</property>
<property name="Ranger Admin Identity"></property>
<property name="Ranger Kerberos Enabled">false</property>
</authorizer>
Details on the "ldap-user-group-provider can be found in the nifi admin guide:
Make sure the <userGroupProvider> comes before the <authorizer> in this configuration.
Thanks,
Matt
Created 03-07-2018 05:52 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Matt Clarke, thank you. I will update after I give this a try.
Created 03-07-2018 06:56 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
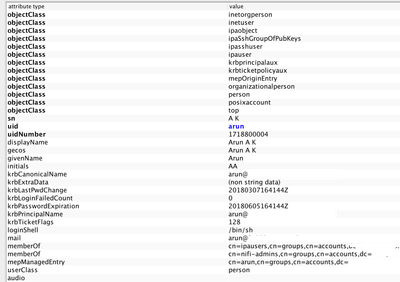
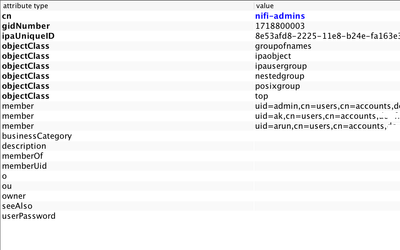
@Matt Clarke I assume I am getting close to the solution. I made the changes as you suggested. However I get the below error on login.
o.a.n.w.a.c.AccessDeniedExceptionMapper identity[user1], groups[] does not have permission to access the requested resource. No applicable policies could be found. Returning Forbidden response.
The Group Name is empty/not picked up. What could be wrong here?
Created 03-07-2018 07:36 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hard to say without knowing exactly what is in your LDAP and what specific you configured in your userGroupProvider.
specifically:
<propertyname="User Group Name Attribute"></property>
<propertyname="User Group Name Attribute - Referenced Group Attribute"></property>
and/or:
<propertyname="Group Member Attribute"></property>
<propertyname="Group Member Attribute - Referenced User Attribute"></property>
Plus - would also need to know how Ranger is creating these users and groups when it syncs with your LDAP. (same case)
Matt
Created 03-12-2018 05:02 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Something I just noticed you have wrong in your provider above:
<propertyname="User Search Filter">(uid={0})</property>and
<propertyname="Group Search Filter">(cn={0})</property>The group provider is trying to return all groups and users sousing {0}to pass some specific input is not going to work here.
That is a valid filter in the login-identity-provoders.xml wheer you are trying to return a very sepcific user for authentication purposes.
Try changing these lines to:
<propertyname="User Search Filter">uid</property>
<propertyname="Group Search Filter">cn</property>
See if that works for you.
Thanks,
Matt
Created 03-12-2018 09:05 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
NiFi failed to start with this change, I rolled back the changes. I am assuming that it expects an expression at the filter.
Created 10-02-2018 01:04 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The "ldap-user-group-provider" is not passed any input, so using things like (cn={0}) will not work. This is perfectly valid in the login-identity-providers.xml since it is being passed the login name the user enters on login screen.
<userGroupProvider> <identifier>ldap-user-group-provider</identifier>
<class>org.apache.nifi.ldap.tenants.LdapUserGroupProvider</class>
<property name="Authentication Strategy">SIMPLE</property>
<property name="Manager DN">uid=admin,cn=blah,cn=blah,dc=blah,dc=com</property>
<property name="Manager Password">blah</property>
<property name="TLS - Keystore"></property>
<property name="TLS - Keystore Password"></property>
<property name="TLS - Keystore Type"></property>
<property name="TLS - Truststore"></property>
<property name="TLS - Truststore Password"></property>
<property name="TLS - Truststore Type"></property>
<property name="TLS - Client Auth"></property>
<property name="TLS - Protocol"></property>
<property name="TLS - Shutdown Gracefully"></property>
<property name="Referral Strategy">FOLLOW</property>
<property name="Connect Timeout">10 secs</property>
<property name="Read Timeout">10 secs</property>
<property name="Url">ldap://blah.ldap.com:389</property>
<property name="Page Size"></property>
<property name="Sync Interval">30 mins</property>
<property name="User Search Base">cn=users,cn=accounts,dc=blah,dc=blah,dc=com</property>
<property name="User Object Class">person</property>
<property name="User Search Scope">SUBTREE</property>
<property name="User Search Filter"></property>
<property name="User Identity Attribute">uid</property>
<property name="User Group Name Attribute">memberOf</property>
<property name="User Group Name Attribute - Referenced Group Attribute"></property> <property name="Group Search Base">cn=groups,cn=accounts,dc=blah,dc=blah,dc=com</property>
<property name="Group Object Class">posixgroup</property>
<property name="Group Search Scope">SUBTREE</property>
<property name="Group Search Filter"></property>
<property name="Group Name Attribute">cn</property>
<property name="Group Member Attribute">member</property>
<property name="Group Member Attribute - Referenced User Attribute"></property> </userGroupProvider>
The above is what you should have at a minimum.
You may need to also specify the two "Referenced User/Group Attribute" values, but can't tell from your sample LDAP output is that is really going to be necessary.
-
Thanks,
Matt