Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: How to set the authority/right of Atlas Web UI...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to set the authority/right of Atlas Web UI User?
Created on 08-26-2016 06:18 AM - edited 08-19-2019 03:31 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I want to add a new user account for atlas Web UI, so I append a line text into <atlas-conf>/users-credentials.properties
zte=ADMIN::8d969eef6ecad3c29a3a629280e686cf0c3f5d5a86aff3ca12020c923adc6c92
This means that, the user name is zte, and the password is 123456.
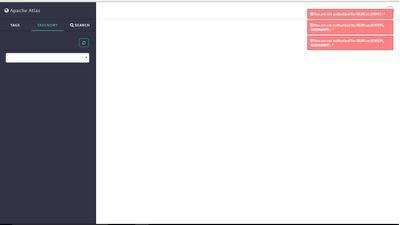
But when I login in the Atlas Web UI by using this user name and password, it shown like this:
The tips which on the top right of this screenshot showed that, this account are not authorized for READ *.
So, how can I set the authority/right of my new user account ?
Thank you very much.
Created 08-26-2016 07:00 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Simple Authorization
The default setting is Simple, and the following properties are automatically set under Advanced application-properties on the Advanced tab.
Table: Apache Atlas Simple Authorization
| Property | Value |
|---|---|
| atlas.authorizer.impl | simple |
| atlas.auth.policy.file | {{conf_dir}}/policy-store.txt |
The policy-store.txt file has the following format:
Policy_Name;;User_Name:Operations_Allowed;;Group_Name:Operations_Allowed;;Resource_Type:Resource_Name
For example:
adminPolicy;;admin:rwud;;ROLE_ADMIN:rwud;;type:*,entity:*,operation:*,taxonomy:*,term:* userReadPolicy;;readUser1:r,readUser2:r;;DATA_SCIENTIST:r;;type:*,entity:*,operation:*,taxonomy:*,term:* userWritePolicy;;writeUser1:rwu,writeUser2:rwu;;BUSINESS_GROUP:rwu,DATA_STEWARD:rwud;;type:*,entity:*,operation:*,taxonomy:*,term:*
In this example readUser1, readUser2, writeUser1 and writeUser2 are the user IDs, each with its corresponding access rights. The User_Name, Group_Name and Operations_Allowed are comma-separated lists.
Authorizer Resource Types:
- Operation
- Type
- Entity
- Taxonomy
- Term
- Unknown
Operations_Allowed are r = read, w = write, u = update, d = delete
Let me know if you have Ranger enabled in your cluster, different operations would be needed for Ranger authorization.
Created 08-26-2016 07:00 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Simple Authorization
The default setting is Simple, and the following properties are automatically set under Advanced application-properties on the Advanced tab.
Table: Apache Atlas Simple Authorization
| Property | Value |
|---|---|
| atlas.authorizer.impl | simple |
| atlas.auth.policy.file | {{conf_dir}}/policy-store.txt |
The policy-store.txt file has the following format:
Policy_Name;;User_Name:Operations_Allowed;;Group_Name:Operations_Allowed;;Resource_Type:Resource_Name
For example:
adminPolicy;;admin:rwud;;ROLE_ADMIN:rwud;;type:*,entity:*,operation:*,taxonomy:*,term:* userReadPolicy;;readUser1:r,readUser2:r;;DATA_SCIENTIST:r;;type:*,entity:*,operation:*,taxonomy:*,term:* userWritePolicy;;writeUser1:rwu,writeUser2:rwu;;BUSINESS_GROUP:rwu,DATA_STEWARD:rwud;;type:*,entity:*,operation:*,taxonomy:*,term:*
In this example readUser1, readUser2, writeUser1 and writeUser2 are the user IDs, each with its corresponding access rights. The User_Name, Group_Name and Operations_Allowed are comma-separated lists.
Authorizer Resource Types:
- Operation
- Type
- Entity
- Taxonomy
- Term
- Unknown
Operations_Allowed are r = read, w = write, u = update, d = delete
Let me know if you have Ranger enabled in your cluster, different operations would be needed for Ranger authorization.
Created 08-26-2016 10:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Ethan Hsieh Just as @Ayub Pathan's explanation you will be able to assign users with permissions if you add the user into policy-store.txt
adminPolicy;;admin:rwud,zte:rwud;;ROLE_ADMIN:rwud;;type:*,entity:*,operation:*,taxonomy:*,term:*
or you should be able add user with different roles into users-credentials.properties by adding entries like below
zte=ROLE_ADMIN::8d969eef6ecad3c29a3a629280e686cf0c3f5d5a86aff3ca12020c923adc6c92 testuser=DATA_SCIENTIST::8d969eef6ecad3c29a3a629280e686cf0c3f5d5a86aff3ca12020c923adc6c92
Created 04-06-2017 10:51 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Ayub Khan
I am trying to add custom policy like
dataAnalyistPolicy;;;;DATA_ANALYST:r;;type:*,entity:contents,taxonomy:*,term:*
I am assuming that if I mention specific type or entity or term it will allow to perform set actions to a particular. I have tried mentioning entity:content but it block all operations. Can you guide on this.
Thanks,
Created 04-06-2017 12:18 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Naseem Rafique, you have to specify * for Atlas 0.8, granular level authorization in pipeline.
Created 04-06-2017 12:29 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You mean currently I can only specify * I can't authorize a user to access to a specific type right?
Version I am using is apache-atlas-0.9-incubating-SNAPSHOT.
Created 04-06-2017 12:58 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, it will allow all (*) or none.
Created 07-05-2018 06:42 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, How do we solve this while using Ranger. I gave the Read access however it shows the same issue.
Created 07-05-2018 07:10 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Varun Nemmani , Please follow this documentation regarding setting up atlas ranger policies.
https://cwiki.apache.org/confluence/display/RANGER/ATLAS+Plugin
Created 07-05-2018 09:09 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Nixon,
Thanks. Yes the relevant permissions for Read are given on all the ATLAS policies. However the user gets the error in the UI.
Regards,
Varun