Support Questions
- Cloudera Community
- Support
- Support Questions
- How to use InvokeHTTP without SSL verification
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to use InvokeHTTP without SSL verification
- Labels:
-
Apache NiFi
Created 11-05-2020 11:09 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
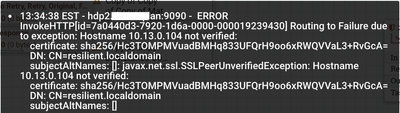
How can I use InvokeHTTP without SSL verification? I followed this article on how to import the public certificate but that cert is not CA-signed, and InvokeHTTP doesn't work. Below is the error I get.
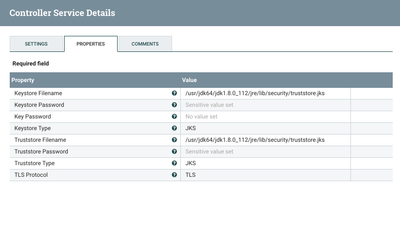
In InvokeHTTP, I'm using the StandardSSLContextService with the following configs:
Thanks.
Valentin
Created 11-09-2020 04:40 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@vatodorov19 If the service you are connecting too is https, there is no way to use invokeHttp without SSL Verification. If the remote host is using a publicly signed cert, try using cacerts in your java location before trying to make keystores and truststores. If you do make keystores and truststores from the service's public or self signed certs you will need to make sure those certs are generated following best practices. For example: using a real hostname for the service and make sure you connect to the same hostname, not an ip or "resilient.localdomain".
If this answer resolves your issue or allows you to move forward, please choose to ACCEPT this solution and close this topic. If you have further dialogue on this topic please comment here or feel free to private message me. If you have new questions related to your Use Case please create separate topic and feel free to tag me in your post.
Thanks,
Steven
Created 11-09-2020 04:40 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@vatodorov19 If the service you are connecting too is https, there is no way to use invokeHttp without SSL Verification. If the remote host is using a publicly signed cert, try using cacerts in your java location before trying to make keystores and truststores. If you do make keystores and truststores from the service's public or self signed certs you will need to make sure those certs are generated following best practices. For example: using a real hostname for the service and make sure you connect to the same hostname, not an ip or "resilient.localdomain".
If this answer resolves your issue or allows you to move forward, please choose to ACCEPT this solution and close this topic. If you have further dialogue on this topic please comment here or feel free to private message me. If you have new questions related to your Use Case please create separate topic and feel free to tag me in your post.
Thanks,
Steven
Created 11-12-2020 06:55 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @stevenmatison
Is there a plan to add a feature to InvokeHTTP to access hosts with a self-signed cert? It is very common for organizations to deploy internal hosts with localhost.localdomain certs, that are only accessible by the IP.
Created 11-12-2020 08:12 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@vatodorov19 I have used tons of self signed certs and not had issues. Maybe you need to just adjust the method to create the self signed certs and/or the keystore and truststores based on known working nifi samples. SSL, Certs, Keystores, Versions, and SSL Context Services each are all very finicky so getting them right can be as easy as a config change, or adjustment in the commands to kick of cert/keystore creations.
Created 06-15-2022 01:23 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have used invokeHTTP in 1.12 version without SSL cert and works fine, however new version 1.16 doesn't. Any settings available to ignore?. Ex: I connect to SQL server with JDBCConnection with property trustServerCertificate=true; post which it works without certifcates.