Support Questions
- Cloudera Community
- Support
- Support Questions
- Is it possible to create a https rest api in nifi
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Is it possible to create a https rest api in nifi
- Labels:
-
Apache NiFi
Created 04-08-2019 06:28 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would to know is nifi capable of handling a https based server client communcation in which the client communicate with nifi http processor over secure channel
Created on 04-08-2019 06:46 PM - edited 08-17-2019 04:04 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
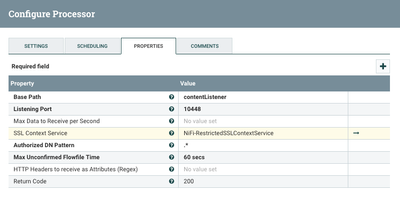
Absolutely, Simply configure your listenHTTP processor with a SSLContextService NiFi Controller Service. The controller service with be used to provide the keystore and truststore necessary to facilitate the two-way TLS/SSL handshake from the connecting client(s).
When configured with a SSL Context Service, the processor's jetty server will only accept TLS 1.2 connections.
-
Thank you,
Matt
-
If you found this answer addressed your question, please take a moment to login in and click the "ACCEPT" link.
Created 05-15-2020 10:45 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear @MattWho ,
Do you have a step by step guide on this?
I have a httphandler running on port 8060. I also have NIFI authentication enabled using ldap. For this particular httphandler processor, i have tried enabling TLS 1.2 but no luck. Could you please help with a step by step guide?
Created 06-05-2020 11:27 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am not sure what configuration step you need help with.
What is not "working"?
What errors are you seeing when processor tries to execute?
NiFi configured method for user authentication has nothing to do with how processors authenticate with external servers/resources. Your user authentication and subsequent authorization simply controls what you as a NiFi user can see and do within the NiFi UI. NiFi components like processors you add via the NiFi UI are not running/executing as your user. All components are executed by the NiFi JVM service user. Any authentication required is configured via the component itself.
If your endpoint httphandler running on port 8060 required mutual TLS authenctication via the TLS handshake, you will need to configure a SSLContextService that has both a keystore and a truststore. The keystore must contain a single "PrivateKeyEntry" that supports clientAuth and is capable of beig trusted by the target endpoint. The Truststore used must contain the complete TLS trust chain for the target endpoint presented server certificate in the TLS hanshake.
If only one-way TLS is required, all that is need is an SSLContextService with the above mentioned truststore.
Using command:
"openssl s_client -connect <servername>:<port> --showcerts"
is a good way to observe the server side handshake and obtain all the public certificates needed for a complete trusts chain in your truststore.
Hope this helps,
Matt