Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: Kerberos HDFS security issue
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Kerberos HDFS security issue
Created 12-01-2016 06:18 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
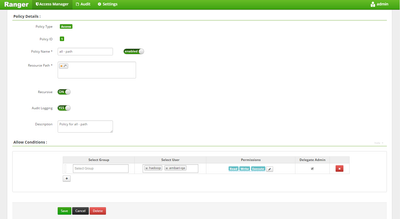
I have ranger plugin enabled for HDFS and the policy is in place and I am not in the list of users that have access to the policy (see picture) but I can still access all the HDFS directories ?
-bash-4.1$ klist Ticket cache: FILE:/tmp/krb5cc_600 Default principal: sami@MY.COM Valid starting Expires Service principal 11/30/16 23:22:44 12/01/16 23:22:44 krbtgt/MY.COM@MY.COM renew until 11/30/16 23:22:44 -bash-4.1$ -bash-4.1$ -bash-4.1$ hdfs dfs -ls /user/flume/ Found 4 items drwx------ - flume hdfs 0 2016-11-28 19:00 /user/flume/.Trash drwxr-xr-x - flume hdfs 0 2016-10-12 16:50 /user/flume/.hiveJars drwxrwxr-x - flume hdfs 0 2016-11-23 10:03 /user/flume/tweets drwxr-xr-x - flume hdfs 0 2016-11-03 10:54 /user/flume/tweets2 -bash-4.1$ <a href="/storage/attachments/10019-capture.jpg">capture.jpg</a>
if I destroy the ticket then I don't get access .
-bash-4.1$ kdestroy -bash-4.1$ -bash-4.1$ -bash-4.1$ klist klist: No credentials cache found (ticket cache FILE:/tmp/krb5cc_600) -bash-4.1$ -bash-4.1$ hdfs dfs -ls /user/flume/ 16/12/01 13:19:08 WARN ipc.Client: Exception encountered while connecting to the server : javax.security.sasl.SaslException: GSS initiate failed [Caused by GSSException: No valid credentials provided (Mechanism level: Failed to find any Kerberos tgt)]
Created 12-02-2016 06:42 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
see ranger audit logs to figure out whether ranger-acl or hadoop-acl is granting access to the user.
Created 12-01-2016 06:33 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you snapshot the page where you have the policies ? If the profile is public, I believe it overrides any other permissions. How about you introducing your user and denying any privileges from him over HDFS.
Created 12-01-2016 06:51 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
on profile it doesn't say its a public profile ? please see the picture below of the policy
Created 12-01-2016 06:35 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Access will be granted with native HDFS permissions if there is no ranger policy. You can check ranger audit to confirm.
Created on 12-01-2016 06:50 PM - edited 08-19-2019 02:10 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
but there is ranger policy in place please see the picture below
Created 12-02-2016 02:50 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can anyone answer this please ?
Created 12-02-2016 06:42 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
see ranger audit logs to figure out whether ranger-acl or hadoop-acl is granting access to the user.
Created 02-08-2017 06:50 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Sami Ahmad: You have an HDFS policy which does not grant permissions to your user for viewing resources. In most of the components, this would boil down to access request being denied. However, in HDFS, if a Ranger policy does not grant access to a resource, native Hadoop privileges are checked as well. If HDFS grants user 'SAMI' access to resources, 'SAMI' will be able to access the same (inspite of Ranger policy not granting permission).
You can check whether its Ranger policy responsible for your user being able to view resources or its native Hadoop ACLs through Audit page->Access tab.
In screenshot, Policy ID is -- and also, Access Enforcer=hadoop-acl which means the user had access through native Hadoop ACL. None of the Ranger Hadoop policies are responsible for the Access/ Deny. Hope this helps.