Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: LDAP/AD authentication failed
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
LDAP/AD authentication failed
- Labels:
-
Cloudera Manager
Created on 09-15-2018 01:30 PM - edited 09-15-2018 01:40 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Authentication failure
2018-09-15 16:39:59,185 INFO 1985572916@scm-web-8:org.springframework.security.ldap.SpringSecurityLdapTemplate: Ignoring PartialResultException
2018-09-15 16:08:13,360 ERROR 1386832780@scm-web-13:com.cloudera.server.web.cmf.CmfLdapAuthenticationProvider: LDAP/AD authentication failed
org.springframework.dao.IncorrectResultSizeDataAccessException: Incorrect result size: expected 1, actual 0
at org.springframework.security.ldap.SpringSecurityLdapTemplate.searchForSingleEntryInternal(SpringSecurityLdapTemplate.java:239)
at org.springframework.security.ldap.authentication.ad.ActiveDirectoryLdapAuthenticationProvider.searchForUser(ActiveDirectoryLdapAuthenticationProvider.java:258)
at org.springframework.security.ldap.authentication.ad.ActiveDirectoryLdapAuthenticationProvider.doAuthentication(ActiveDirectoryLdapAuthenticationProvider.java:114)
at org.springframework.security.ldap.authentication.AbstractLdapAuthenticationProvider.authenticate(AbstractLdapAuthenticationProvider.java:61)
at com.cloudera.server.web.cmf.CmfLdapAuthenticationProvider.authenticate(CmfLdapAuthenticationProvider.java:107)
at org.springframework.security.authentication.ProviderManager.authenticate(ProviderManager.java:156)
at org.springframework.security.authentication.ProviderManager.authenticate(ProviderManager.java:174)
at org.springframework.security.web.authentication.UsernamePasswordAuthenticationFilter.attemptAuthentication(UsernamePasswordAuthenticationFilter.java:94)
at org.springframework.security.web.authentication.AbstractAuthenticationProcessingFilter.doFilter(AbstractAuthenticationProcessingFilter.java:194)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:323)
at org.springframework.security.web.authentication.logout.LogoutFilter.doFilter(LogoutFilter.java:105)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:323)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:87)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:323)
at org.springframework.security.web.session.ConcurrentSessionFilter.doFilter(ConcurrentSessionFilter.java:125)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:323)
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:173)
at org.springframework.web.filter.DelegatingFilterProxy.invokeDelegate(DelegatingFilterProxy.java:237)
at org.springframework.web.filter.DelegatingFilterProxy.doFilter(DelegatingFilterProxy.java:167)
at org.mortbay.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1212)
at org.springframework.web.filter.CharacterEncodingFilter.doFilterInternal(CharacterEncodingFilter.java:88)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:76)
at org.mortbay.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1212)
at org.mortbay.jetty.servlet.ServletHandler.handle(ServletHandler.java:399)
at org.mortbay.jetty.security.SecurityHandler.handle(SecurityHandler.java:216)
at org.mortbay.jetty.servlet.SessionHandler.handle(SessionHandler.java:182)
at org.mortbay.jetty.security.SecurityHandler.handle(SecurityHandler.java:216)
at org.mortbay.jetty.security.SecurityHandler.handle(SecurityHandler.java:216)
at org.mortbay.jetty.handler.ContextHandler.handle(ContextHandler.java:767)
at org.mortbay.jetty.webapp.WebAppContext.handle(WebAppContext.java:450)
at org.mortbay.jetty.handler.HandlerWrapper.handle(HandlerWrapper.java:152)
at org.mortbay.jetty.handler.StatisticsHandler.handle(StatisticsHandler.java:53)
at org.mortbay.jetty.handler.HandlerWrapper.handle(HandlerWrapper.java:152)
at org.mortbay.jetty.Server.handle(Server.java:326)
at org.mortbay.jetty.HttpConnection.handleRequest(HttpConnection.java:542)
at org.mortbay.jetty.HttpConnection$RequestHandler.content(HttpConnection.java:945)
at org.mortbay.jetty.HttpParser.parseNext(HttpParser.java:756)
at org.mortbay.jetty.HttpParser.parseAvailable(HttpParser.java:218)
at org.mortbay.jetty.HttpConnection.handle(HttpConnection.java:404)
at org.mortbay.io.nio.SelectChannelEndPoint.run(SelectChannelEndPoint.java:410)
at org.mortbay.thread.QueuedThreadPool$PoolThread.run(QueuedThreadPool.java:582)
2018-09-15 16:08:13,368 INFO 1386832780@scm-web-13:com.cloudera.server.web.cmf.AuthenticationFailureEventListener: Authentication failure for user: 'func_svc_zab_cdh' from 10.99.195.186
1) I have added the group "cloudera_manager_API" in LDAP User Groups.
2) func_svc_zab_cdh is a member of "cloudera_manager_API" group.
3) The configuration.
Created on 09-25-2018 12:09 PM - edited 09-25-2018 12:10 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was able to resolve this issue by moving the user and group under one OU. I think most likely it cannot do a backward search.
Thank you @bgooley much appreciated. I learnt a few things in this process.
Created 09-17-2018 11:24 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi...
A couple of things I noticed:
(1)
Based on the stack trace, you have configured Cloudera Manager's External Authentication with External Authentication Type: Active Directory
This means that the username specified in the login page will be concatenated with the Active Directory Domain value to form a userPrincipalName value.
For example, if I use a login name of "user1" and my Active Directory Domain is "example.com" the result will be a search for an object that has userPrincipalName=user1@example.com
The stack trace shows that the query did not find any such match for that search.
If your users' userPrincipalName values do not contain the string they nornally use to log in as (commonly the sAMAccountName) then you will need to use the LDAP value for External Authentication Type in the Cloudera Manager configuration.
(2)
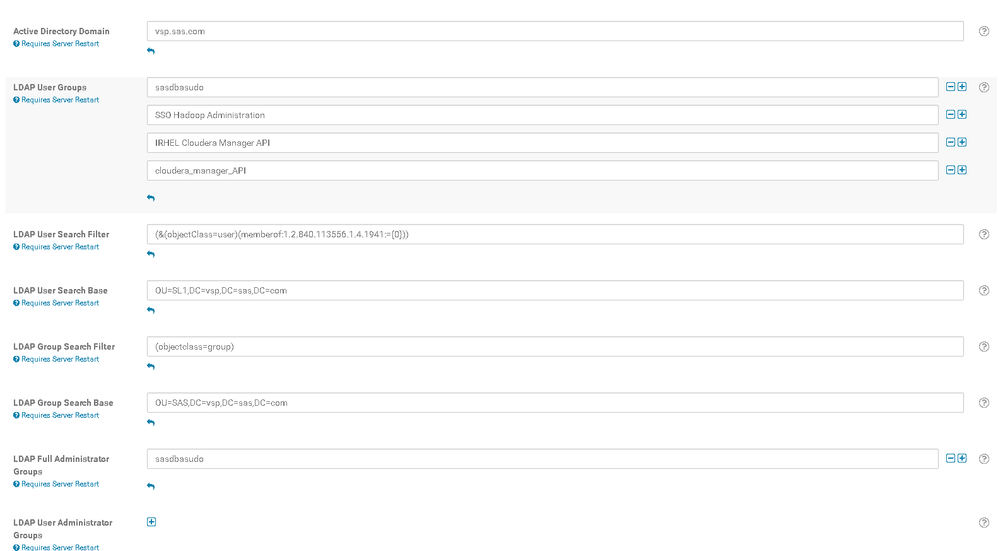
Based on your screen shot, it appears your LDAP User Search Filter may not be configured in a way that will return any search results.
You have:
(&(objectclass=user)(memberof:1.2.840.113556.1.4.1941:={0}))
I don't think that search filter is doing what you want it to do (though I think the issue I mentioned above is causing the direct failure you are seeing now. When using the LDAP Matching Rule in chain, you would need the {0} to be a group Distinguished Name as mentioned on the following page:
https://docs.microsoft.com/en-us/windows/desktop/adsi/search-filter-syntax
For example, this may be more in line with what you were intending:
(&(objectclass=user)(sAMAccountName={0})(memberof:1.2.840.113556.1.4.1941:=CN=hadoop_group,DC=Example,DC=COM))
In the above, only users who are a member of "hadoop_group" or any of the nested groups can auth.
Created on 09-17-2018 11:53 AM - edited 09-17-2018 11:54 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1) So when i login into cloudera manager as func_svc_zab_cdh that will be converted to func_svc_zab_cdh@vsp.sas.com
I logged into AD and see the same in the "userPrincipalname" which looks correct. Please find the attachment.
2) Regarding the second point we want to keep it wide open . {0} will be replaced by the username that was used to login screen.
I also tried removing all groups from "LDAP User Groups" as a test and allowing everyone to login. I , my colleage can login. however "func_svc_zab_cdh" cannot login with the same error. If i enter a wring password for this user i get bad credentials.
I also tried open the search filter to to wide open . event that does not work.
Can you look at maybe debug logs ?
Created 09-17-2018 12:58 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The stack shows that whatever search was generated by spring framework didn't return any matches.
You can get more information by enabling TRACE level logging for the springframework classes involved.
(1)
Edit /etc/cloudera-scm-server/log4j.properties
Add the following lines:
log4j.logger.org.springframework.ldap=TRACE
log4j.logger.org.springframework.security.ldap=TRACE
(2)
Restart Cloudera Manager:
# service cloudera-scm-server restart
-------------------
In general, when encountering the problems you describe, I recommend using the "LDAP" External Authentication Type so you have better control over the search filters.
I still note that it appears your LDAP User Search Filter is not going to return what you expect since the syntax requires "DN" rather than a username. The {0} will be replaced with your username, so I don't believe the search will return any users. The user search filter is only used if you are using the "LDAP" External Authentication so you won't see problems with it unless you do use LDAP (vs Active Directory).
Please feel free to share the debug output from a failed login as it should shed light on the problem. Your UPN does look correct, so it is hard to say why the search is failing to return a result.
Created on 09-18-2018 07:07 AM - edited 09-18-2018 07:11 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
After making changes to log4j and removing all entries from LDAP User Search Filter,LDAP User Search Base,LDAP Group Search Filter,LDAP Group Search Base . Which as you said are only used when ldap is present.
In-addition to following this doc : https://www.cloudera.com/documentation/enterprise/5-15-x/topics/cm_sg_external_auth.html using "Active directory" method i found the below
In the Active Directory Domain property, provide the domain to authenticate against.
LDAP URL and Active Directory are the only settings required to allow anyone in Active Directory to log in to Cloudera Manager.
So i just provided LDAP URL and Active directory, after making this change and restarting cloudera-scm-server . I am able to login however "func_svc_zab_cdh" is not able to login.
LDAP User Groups - same as screenshot above.
LOGS:
When i login:
2018-09-18 10:03:47,198 DEBUG 936018027@scm-web-6:org.springframework.security.ldap.authentication.ad.ActiveDirectoryLdapAuthenticationProvider: Processing authentication request for user: desind
2018-09-18 10:03:47,324 DEBUG 936018027@scm-web-6:org.springframework.security.ldap.SpringSecurityLdapTemplate: Searching for entry under DN '', base = 'dc=vsp,dc=sas,dc=com', filter = '(&(objectClass=user)(userPrincipalName={0}))'
2018-09-18 10:03:47,335 DEBUG 936018027@scm-web-6:org.springframework.security.ldap.SpringSecurityLdapTemplate: Found DN: cn=desind,ou=Users,ou=Consulting,ou=SAS,dc=vsp,dc=sas,dc=com
2018-09-18 10:03:47,345 INFO 936018027@scm-web-6:org.springframework.security.ldap.SpringSecurityLdapTemplate: Ignoring PartialResultException
2018-09-18 10:03:47,347 DEBUG 936018027@scm-web-6:org.springframework.security.ldap.authentication.ad.ActiveDirectoryLdapAuthenticationProvider: 'memberOf' attribute values: [CN=logon_elv_u_cicld_all,OU=Logon,OU=Groups,OU=CICLD,OU=Customers,OU=AWSSYD,OU=Sites,DC=gsp,DC=vsp,DC=sas,DC=com, CN=CICLD.LOB,OU=ServiceNow,OU=Groups,OU=CICLD,OU=Customers,OU=AWSSYD,OU=Sites,DC=gsp,DC=vsp,DC=sas,DC=com, CN=CICLD Jira - Confluence,OU=Atlassian,OU=Groups,OU=CICLD,OU=Customers,OU=AWSSYD,OU=Sites,DC=gsp,DC=vsp,DC=sas,DC=com, CN=logon_elv_w_cicld_all,OU=Logon,OU=Groups,OU=CICLD,OU=Customers,OU=AWSSYD,OU=Sites,DC=gsp,DC=vsp,DC=sas,DC=com, CN=logon_elv_w_ssovd_desind-dt,OU=Logon,OU=Groups,OU=SSOVD,OU=SL1,DC=vsp,DC=sas,DC=com, CN=SASDB.LOB,OU=ServiceNow,OU=Groups,OU=SASDB,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_std_u_dig_dig93au,OU=Logon,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_std_u_dig_dig95au,OU=Logon,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_std_u_dig_dig96au,OU=Logon,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_std_u_dig_dig99au,OU=Logon,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_std_u_dig_dig97au,OU=Logon,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_std_u_dig_dig98au,OU=Logon,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_std_u_dig_dig94au,OU=Logon,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_ncx_deny,OU=Logon,OU=Groups,OU=NCX,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_std_u_dig_dig92au,OU=Logon,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_std_u_dig_dig91au,OU=Logon,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_tool_securevault,OU=Groups,OU=Infrastructure,OU=SAS,DC=vsp,DC=sas,DC=com, CN=logon_ncj_deny,OU=Logon,OU=Groups,OU=NCJ,OU=SL1,DC=vsp,DC=sas,DC=com, CN=sasdbasudo,OU=Groups,OU=SAS DBA,OU=SAS,DC=vsp,DC=sas,DC=com, CN=logon_std_u_dig_dig64au,OU=Logon,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_std_u_dig_dig65au,OU=Logon,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_elv_u_dig_all,OU=Logon,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=ITM.LOB,OU=ServiceNow,OU=Groups,OU=ITM,OU=SL1,DC=vsp,DC=sas,DC=com, CN=dba,OU=Unix Resources,OU=SAS,DC=vsp,DC=sas,DC=com, CN=SSO Hadoop Administration,OU=Groups,OU=Atlassian,OU=Functional,OU=SAS,DC=vsp,DC=sas,DC=com, CN=DIG Cloudera Manager Admins,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=CICLD.AllUsers,OU=Groups,OU=CICLD,OU=Customers,OU=AWSSYD,OU=Sites,DC=gsp,DC=vsp,DC=sas,DC=com, CN=digsudo,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=digsasauth,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_elv_u_aid_all,OU=Logon,OU=Groups,OU=AID,OU=SL1,DC=vsp,DC=sas,DC=com, CN=sas_samviewer,OU=Groups,OU=Functional,OU=SAS,DC=vsp,DC=sas,DC=com, CN=DIG.LOB,OU=ServiceNow,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_elv_w_dig_all,OU=Logon,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_elv_w_aid_all,OU=Logon,OU=Groups,OU=AID,OU=SL1,DC=vsp,DC=sas,DC=com, CN=AID.LOB,OU=ServiceNow,OU=Groups,OU=AID,OU=SL1,DC=vsp,DC=sas,DC=com, CN=DIG Jira - Confluence,OU=Atlassian,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=digunix,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=digapp,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=DIG RDC,OU=Groups,OU=DIG,OU=SL1,DC=vsp,DC=sas,DC=com, CN=MISTK.LOB,OU=ServiceNow,OU=Groups,OU=MISTK,OU=SL1,DC=vsp,DC=sas,DC=com, CN=logon_tool_vpn_rdp,OU=Groups,OU=Infrastructure,OU=SAS,DC=vsp,DC=sas,DC=com, CN=SAS.LOBi,OU=Internal LOBs,OU=ServiceNow,OU=Functional,OU=SAS,DC=vsp,DC=sas,DC=com, CN=SASDB Jira - Confluence,OU=Atlassian,OU=Groups,OU=SASDB,OU=SL1,DC=vsp,DC=sas,DC=com, CN=SASDB.AllUsers,OU=Groups,OU=SASDB,OU=SL1,DC=vsp,DC=sas,DC=com, CN=SAS Solutions OnDemand.LOBi,OU=Internal LOBs,OU=ServiceNow,OU=Functional,OU=SAS,DC=vsp,DC=sas,DC=com, CN=MISTK.AllUsers,OU=Groups,OU=MISTK,OU=SL1,DC=vsp,DC=sas,DC=com, CN=ITM.AllUsers,OU=Groups,OU=ITM,OU=SL1,DC=vsp,DC=sas,DC=com, CN=AID.AllUsers,OU=Groups,OU=AID,OU=SL1,DC=vsp,DC=sas,DC=com, CN=dbasudo,OU=Groups,OU=SAS DBA,OU=SAS,DC=vsp,DC=sas,DC=com, CN=AID Jira - Confluence,OU=Atlassian,OU=Groups,OU=AID,OU=SL1,DC=vsp,DC=sas,DC=com, CN=SAS Internal - ASP,OU=Groups,OU=Atlassian,OU=Functional,OU=SAS,DC=vsp,DC=sas,DC=com, CN=jira-users,OU=Groups,OU=Atlassian,OU=Functional,OU=SAS,DC=vsp,DC=sas,DC=com, CN=confluence-users,OU=Groups,OU=Atlassian,OU=Functional,OU=SAS,DC=vsp,DC=sas,DC=com, CN=SAS Internal - All,OU=Groups,OU=Atlassian,OU=Functional,OU=SAS,DC=vsp,DC=sas,DC=com, CN=SSO Database Administration,OU=Groups,OU=Atlassian,OU=Functional,OU=SAS,DC=vsp,DC=sas,DC=com, CN=SSO Demo,OU=Groups,OU=Atlassian,OU=Functional,OU=SAS,DC=vsp,DC=sas,DC=com, CN=SSO Share Access,OU=Groups,OU=SSO,OU=SAS,DC=vsp,DC=sas,DC=com, CN=SAS Employees,OU=SAS,DC=vsp,DC=sas,DC=com, CN=ssosvn,OU=Groups,OU=SSO,OU=SAS,DC=vsp,DC=sas,DC=com, CN=SSO Developers,OU=Groups,OU=SSO,OU=SAS,DC=vsp,DC=sas,DC=com, CN=SSO Users,OU=Groups,OU=SSO,OU=SAS,DC=vsp,DC=sas,DC=com, CN=SW-UltraEdit32,OU=Groups,OU=SSO,OU=SAS,DC=vsp,DC=sas,DC=com, CN=SAS Admins,OU=Groups,OU=SASAdmins,OU=SAS,DC=vsp,DC=sas,DC=com, CN=sasdba,OU=Groups,OU=SAS DBA,OU=SAS,DC=vsp,DC=sas,DC=com, CN=SAS Admin Restricted,OU=Groups,OU=SASAdmins,OU=SAS,DC=vsp,DC=sas,DC=com]
2018-09-18 10:03:47,357 DEBUG 936018027@scm-web-6:org.springframework.security.ldap.userdetails.LdapUserDetailsMapper: Mapping user details from context with DN: cn=desind,ou=Users,ou=Consulting,ou=SAS,dc=vsp,dc=sas,dc=com
2018-09-18 10:03:48,209 INFO 936018027@scm-web-6:com.cloudera.server.web.cmf.AuthenticationSuccessEventListener: Authentication success for user: 'desind' from 10.99.195.186
2018-09-18 10:03:51,430 INFO avro-servlet-hb-processor-1:com.cloudera.server.common.AgentAvroServlet: (23 skipped) AgentAvroServlet: heartbeat processing stats: average=79ms, min=26ms, max=839ms.
#############When "func_svc_zab_cdh" user logins################
2018-09-18 10:04:40,227 DEBUG 1978563421@scm-web-13:org.springframework.security.ldap.authentication.ad.ActiveDirectoryLdapAuthenticationProvider: Processin g authentication request for user: func_svc_zab_cdh
2018-09-18 10:04:40,290 DEBUG 1978563421@scm-web-13:org.springframework.security.ldap.SpringSecurityLdapTemplate: Searching for entry under DN '', base = 'd c=vsp,dc=sas,dc=com', filter = '(&(objectClass=user)(userPrincipalName={0}))'
2018-09-18 10:04:40,290 INFO 1978563421@scm-web-13:org.springframework.security.ldap.SpringSecurityLdapTemplate: Ignoring PartialResultException
2018-09-18 10:04:40,292 ERROR 1978563421@scm-web-13:com.cloudera.server.web.cmf.CmfLdapAuthenticationProvider: LDAP/AD authentication failed
org.springframework.dao.IncorrectResultSizeDataAccessException: Incorrect result size: expected 1, actual 0
at org.springframework.security.ldap.SpringSecurityLdapTemplate.searchForSingleEntryInternal(SpringSecurityLdapTemplate.java:239)
at org.springframework.security.ldap.authentication.ad.ActiveDirectoryLdapAuthenticationProvider.searchForUser(ActiveDirectoryLdapAuthenticationProv ider.java:258)
at org.springframework.security.ldap.authentication.ad.ActiveDirectoryLdapAuthenticationProvider.doAuthentication(ActiveDirectoryLdapAuthenticationP rovider.java:114)
at org.springframework.security.ldap.authentication.AbstractLdapAuthenticationProvider.authenticate(AbstractLdapAuthenticationProvider.java:61)
at com.cloudera.server.web.cmf.CmfLdapAuthenticationProvider.authenticate(CmfLdapAuthenticationProvider.java:107)
at org.springframework.security.authentication.ProviderManager.authenticate(ProviderManager.java:156)
at org.springframework.security.authentication.ProviderManager.authenticate(ProviderManager.java:174)
at org.springframework.security.web.authentication.UsernamePasswordAuthenticationFilter.attemptAuthentication(UsernamePasswordAuthenticationFilter.j ava:94)
at org.springframework.security.web.authentication.AbstractAuthenticationProcessingFilter.doFilter(AbstractAuthenticationProcessingFilter.java:194)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:323)
at org.springframework.security.web.authentication.logout.LogoutFilter.doFilter(LogoutFilter.java:105)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:323)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:87)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:323)
at org.springframework.security.web.session.ConcurrentSessionFilter.doFilter(ConcurrentSessionFilter.java:125)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:323)
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:173)
at org.springframework.web.filter.DelegatingFilterProxy.invokeDelegate(DelegatingFilterProxy.java:237)
at org.springframework.web.filter.DelegatingFilterProxy.doFilter(DelegatingFilterProxy.java:167)
at org.mortbay.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1212)
at org.springframework.web.filter.CharacterEncodingFilter.doFilterInternal(CharacterEncodingFilter.java:88)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:76)
at org.mortbay.jetty.servlet.ServletHandler$CachedChain.doFilter(ServletHandler.java:1212)
at org.mortbay.jetty.servlet.ServletHandler.handle(ServletHandler.java:399)
at org.mortbay.jetty.security.SecurityHandler.handle(SecurityHandler.java:216)
at org.mortbay.jetty.servlet.SessionHandler.handle(SessionHandler.java:182)
at org.mortbay.jetty.security.SecurityHandler.handle(SecurityHandler.java:216)
at org.mortbay.jetty.security.SecurityHandler.handle(SecurityHandler.java:216)
at org.mortbay.jetty.handler.ContextHandler.handle(ContextHandler.java:767)
at org.mortbay.jetty.webapp.WebAppContext.handle(WebAppContext.java:450)
at org.mortbay.jetty.handler.HandlerWrapper.handle(HandlerWrapper.java:152)
at org.mortbay.jetty.handler.StatisticsHandler.handle(StatisticsHandler.java:53)
at org.mortbay.jetty.handler.HandlerWrapper.handle(HandlerWrapper.java:152)
at org.mortbay.jetty.Server.handle(Server.java:326)
at org.mortbay.jetty.HttpConnection.handleRequest(HttpConnection.java:542)
at org.mortbay.jetty.HttpConnection$RequestHandler.content(HttpConnection.java:945)
at org.mortbay.jetty.HttpParser.parseNext(HttpParser.java:756)
at org.mortbay.jetty.HttpParser.parseAvailable(HttpParser.java:218)
at org.mortbay.jetty.HttpConnection.handle(HttpConnection.java:404)
at org.mortbay.io.nio.SelectChannelEndPoint.run(SelectChannelEndPoint.java:410)
at org.mortbay.thread.QueuedThreadPool$PoolThread.run(QueuedThreadPool.java:582)
2018-09-18 10:04:40,298 INFO 1978563421@scm-web-13:com.cloudera.server.web.cmf.AuthenticationFailureEventListener: Authentication failure for user: 'func_sv c_zab_cdh' from 10.99.195.186
2018-09-18 10:04:51,465 INFO avro-servlet-hb-processor-1:com.cloudera.server.common.AgentAvroServlet: (23 skipped) AgentAvroServlet: heartbeat processing stats: average=68ms, min=25ms, max=839ms.
func_svc_zab_cdh is like any other user and must be able to login and user is present in the vsp.sas.com domain and in group "cloudera_manager_API"
Created 09-18-2018 11:36 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One of the only things I can think of that could have the results you are seeing is if the func_svc_zab_cdh user belongs to another Domain Controller. You could try looking at the user's LDAP DN as a clue, but if I'm right, you can try using the Global Catalog to see if that allows you and the func_svc_zab_cdh user to authenticate.
In your Administration --> Settings search for LDAP URL
If you are using ldap, change the port to 3268
If you are using ldaps, change the port to 3269
For instance:
change ldap://ad.example.com to ldap://ad.example.com:3268
Save the change Restart Cloudera Manager (service cloudera-scm-server restart)
Reasoning:
- The exception shows that no result was returned for a search for userPrincipalName=func_svc_zab_cdh@vsp.sas.com in the dc=vsp,dc=sas,dc=com subtree
- You see in an Active Directory UI that the func_svc_zab_cdh user does have that UPN value
- You can log in
All these factors seem to indicate that the ldap search just cannot return the user's object. Global Catalog keeps a copy of user objects that span DCs so if that user is in the domain (which the user appears to be) then a search of the GC may get the results you seek.
Created on 09-25-2018 12:09 PM - edited 09-25-2018 12:10 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was able to resolve this issue by moving the user and group under one OU. I think most likely it cannot do a backward search.
Thank you @bgooley much appreciated. I learnt a few things in this process.