Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: LDAP/AD users not appearing in Ranger
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
LDAP/AD users not appearing in Ranger
- Labels:
-
Apache Ranger
Created 12-06-2019 05:02 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Attempting to set LDAP/AD users for Ranger (v1.2.0) following the docs (https://docs.cloudera.com/HDPDocuments/HDP3/HDP-3.1.4/configuring-ranger-authe-with-unix-ldap-ad/con...) and this older video (https://www.youtube.com/watch?v=2aZ9GBhCOhA), but when looking at the Ranger Users tab in the Ranger UI, seeing only the original Unix users. In the UI I see...
Looking at the usersync logs, near the tail I see:
....
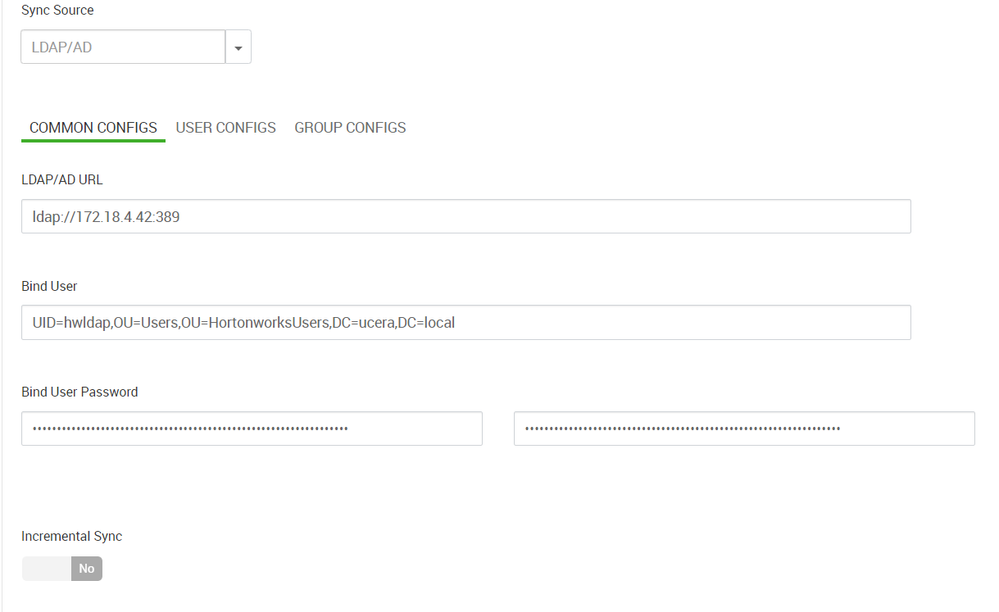
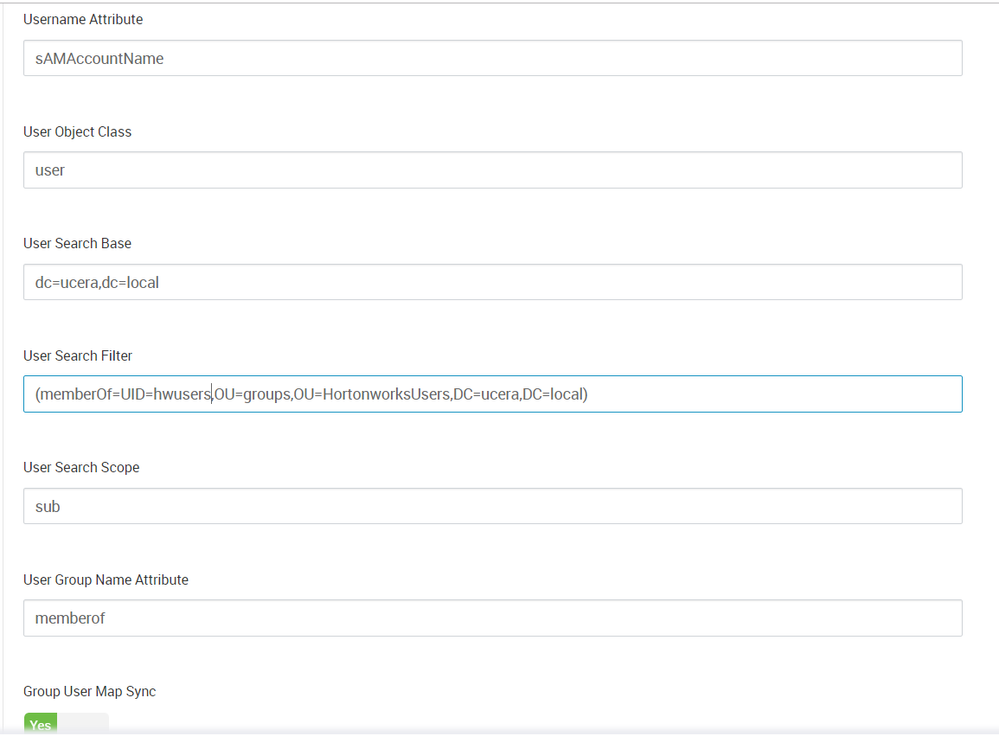
06 Dec 2019 14:21:51 INFO LdapUserGroupBuilder [UnixUserSyncThread] - LdapUserGroupBuilder initialization started
06 Dec 2019 14:21:51 INFO LdapUserGroupBuilder [UnixUserSyncThread] - LdapUserGroupBuilder initialization completed with -- ldapUrl: ldap://172.18.4.42:389, ldapBindDn: UID=hwldap,OU=Users,OU=HortonworksUsers,DC=ucera,DC=local, ldapBindPassword: ***** , ldapAuthenticationMechanism: simple, searchBase: dc=hadoop,dc=apache,dc=org, userSearchBase: [dc=ucera,dc=local], userSearchScope: 2, userObjectClass: user, userSearchFilter: (memberOf=UID=hwusers,OU=groups,OU=HortonworksUsers,DC=ucera,DC=local), extendedUserSearchFilter: (&(objectclass=user)(memberOf=UID=hwusers,OU=groups,OU=HortonworksUsers,DC=ucera,DC=local)), userNameAttribute: sAMAccountName, userSearchAttributes: [sAMAccountName, memberof], userGroupNameAttributeSet: [memberof], pagedResultsEnabled: true, pagedResultsSize: 500, groupSearchEnabled: false, groupSearchBase: [dc=ucera,dc=local], groupSearchScope: 2, groupObjectClass: group, groupSearchFilter: (CN=hwusers), extendedGroupSearchFilter: (&(objectclass=group)(CN=hwusers)(|(cn={0})(cn={1}))), extendedAllGroupsSearchFilter: (&(objectclass=group)(CN=hwusers)), groupMemberAttributeName: cn, groupNameAttribute: UID=hwusers,OU=groups,OU=HortonworksUsers,DC=ucera,DC=local, groupSearchAttributes: [UID=hwusers,OU=groups,OU=HortonworksUsers,DC=ucera,DC=local, cn], groupUserMapSyncEnabled: true, groupSearchFirstEnabled: false, userSearchEnabled: false, ldapReferral: ignore
06 Dec 2019 14:21:51 INFO UserGroupSync [UnixUserSyncThread] - Begin: initial load of user/group from source==>sink
06 Dec 2019 14:21:51 INFO LdapUserGroupBuilder [UnixUserSyncThread] - LDAPUserGroupBuilder updateSink started
06 Dec 2019 14:21:51 INFO LdapUserGroupBuilder [UnixUserSyncThread] - Performing user search first
06 Dec 2019 14:21:51 ERROR LdapUserGroupBuilder [UnixUserSyncThread] - LDAPUserGroupBuilder.getUsers() failed with exception: javax.naming.AuthenticationException: [LDAP: error code 49 - 80090308: LdapErr: DSID-0C09042F, comment: AcceptSecurityContext error, data 52e, v2580]; remaining name 'dc=ucera,dc=local'
06 Dec 2019 14:21:51 INFO LdapUserGroupBuilder [UnixUserSyncThread] - LDAPUserGroupBuilder.getUsers() user count: 0
06 Dec 2019 14:21:51 INFO UserGroupSync [UnixUserSyncThread] - End: initial load of user/group from source==>sink
....
So it seems like Ranger is trying to use AD, encountering an error, and falling back to Unix based users.
Did see this article (https://community.cloudera.com/t5/Community-Articles/Ranger-Ldap-Integration/ta-p/245494), but already have the cluster nodes linked to AD via SSSD, so would think the LDAP/AD sync should already be configured on the nodes and that Ranger should be able to use AD once the configs where entered.
Any idea what is going on here? Any further debugging tips or information (very unfamiliar with AD/LDAP admin stuff)?
Created 12-09-2019 02:42 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Appears to have been able to sync AD users after changing the bing user path to:
CN=hwldap,OU=Users,OU=HortonworksUsers,DC=ucera,DC=local
as opposed to using the "uid" entry key.
IDK why this would make a difference, but seems to have worked. Would anyone with more AD experience have an idea why (note that when I look at the attributes for this entry in our AD both the CN and UID attributes are present)?
Created on 12-07-2019 06:25 PM - edited 12-07-2019 06:30 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Doing a quick search for "LDAP Error 49":
LDAP Error 49 implies an authentication failure .... Typically, the Distinguished Name (DN) or the password is invalid...
I typically go through syncing LDAP users with Ambari, to discover all of the correct LDAP Settings. Once this is compete, only then do I tackle deeper LDAP integration with Ranger.
Created 12-09-2019 02:43 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Created 12-09-2019 02:42 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Appears to have been able to sync AD users after changing the bing user path to:
CN=hwldap,OU=Users,OU=HortonworksUsers,DC=ucera,DC=local
as opposed to using the "uid" entry key.
IDK why this would make a difference, but seems to have worked. Would anyone with more AD experience have an idea why (note that when I look at the attributes for this entry in our AD both the CN and UID attributes are present)?
Created 12-11-2019 11:30 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From the Ranger email list, this is another bit of information that I found helpful:
----------
I’ve configured ranger using the following approach to control who must be synced with AD. Only users belonging to groups inside a specific OU will be synced.
- I’ve created the OU OU=ArthurAmericasGroups,OU=Security Groups,OU=Groups,OU=SHARED,OU=Brazil,DC=domain,DC=com
- Create a group called R2Users inside that OU. I put all desired sync users as its members. Also, you can put other groups as its member. And, you can create other groups like R2TEAM as well. Remember to update this property ranger.usersync.ldap.user.searchfilter to include more than one.
- I’ve configured ranger to sync groups before users.
Here is the configuration.
in COMMON CONFIGS
Label | Property | Value |
LDAP/AD URL | ranger.usersync.ldap.url | ldap://myacticedirectoryserver.domain.com:389 |
Bind User | ranger.usersync.ldap.binddn | CN=LDAP_AD_ACCOUNT,OU=Service Accounts,OU=LCB,OU=Brazil,DC=domain,DC=com |
Bind User Password | ranger.usersync.ldap.ldapbindpassword | LDAP_AD_ACCOUNT user’s password |
Inclemetal Sync | ranger.usersync.ldap.deltasync | Yes |
Enable LDAP STARTTLS | ranger.usersync.ldap.starttls | No |
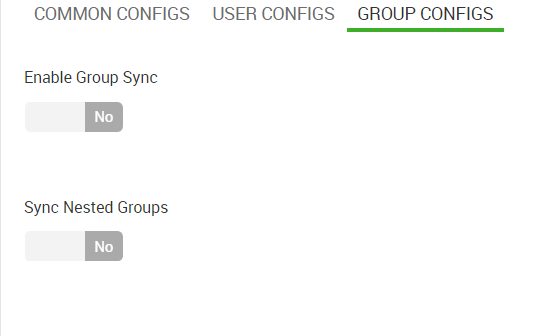
GROUP CONFIGS
Label | Property | Value |
Enable Group Sync | ranger.usersync.group.searchenable | Yes |
Group Member Attribute | ranger.usersync.group.memberattributename | member |
Group Name Attribute | ranger.usersync.group.nameattribute | Cn |
Group Object Class | ranger.usersync.group.objectclass | Group |
Group Search Base | ranger.usersync.group.searchbase | OU=ArthurAmericasGroups,OU=Security Groups,OU=Groups,OU=SHARED,OU=Brazil,DC=domain,DC=com |
Group Search Filter | ranger.usersync.group.searchfilter | |
Enable Group Search First | ranger.usersync.group.search.first.enabled | Yes |
Sync Nested Groups | is_nested_groupsync_enabled | Yes |
Group Hierarchy Levels | ranger.usersync.ldap.grouphierarchylevels | 5 |
USER CONFIGS
Label | Property | Value |
Username Attribute | ranger.usersync.ldap.user.nameatributte | sAMAccountName |
User Object Class | ranger.usersync.ldap.objectclass | User |
User Search Base | ranger.usersync.ldap.searchbase | DC=domain,DC=com |
User Search Filter | ranger.usersync.ldap.user.searchfilter | (memberOf=CN=R2Users,OU=ArthurAmericasGroups,OU=Security Groups,OU=Groups,OU=SHARED,OU=Brazil,DC=domain,DC=com) |
User Search Scope | ranger.usersync.ldap.user.searchscope | Sub |
User Group Name Attribute | ranger.usersync.ldap.groupnameattribute | sAMAccountName |
Group User Map Sync | ranger.usersync.group.usermapsyncenabled | Yes |
Enable User Search | ranger.usersync.user.searchenabled | Yes |
ADVANCED
Ranger Settings
Label | Property | Value |
Authentication method | ACTIVE_DIRECTORY |
AD Settings
Label | Property | Value |
AD Bind Password | ranger.ldap.ad.bind.password | LDAP_AD_ACCOUNT user’s password |
Domain Name (Only for AD) | anger.ldap.ad.domain | DC=domain,DC=com |
AD Base DN | ranger.ldap.ad.base.dn | DC=domain,DC=com |
AD Referreal | ranger.ldap.ad.referreal | Follow |
AD User Serach Filter | ranger.ldap.ad.user.search | (sAMAccountName={0}) |
Advanced ranger-ugsync-site
Label | Property | Value |
ranger.usersync.ldap.referral | ranger.usersync.ldap.referral | Follow |