Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: NiFi 1.5 System Error: Invalid host header
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NiFi 1.5 System Error: Invalid host header
- Labels:
-
Apache NiFi
Created 01-18-2018 02:31 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Guys,
I just upgraded NiFi from v1.4 to v1.5. The cluster is set in secure mode and running in Kubernetes.
But I found below error in Web UI.
System Error The request contained an invalid host header [server:port] in the request [/nifi/]. Check for request manipulation or third-party intercept.
Is it due to nifi.web.proxy.host property? How do I setup it? the IP of the nifi node?
Thanks.
Created 02-26-2018 01:04 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A Jira was raised in Apache Jira (https://issues.apache.org/jira/browse/NIFI-4761) to add a whitelist capability so that users could create a list of hostnames that would be allowed. This Whitelist feature is already part of the HDF 3.1 release from Hortonworks and will be part of the Apache NiFi 1.6 release at a later time.
I am sorry to report there is no way around this host name check in Apache NIFi 1.5.
Thanks,
Matt
Created on 04-13-2018 03:08 PM - edited 08-17-2019 11:40 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure I follow. We are talking about whitelisting configuration needed for NiFi and not Ambari.
The specific nifi.properties property that is used to add a whitelist of allowed http headers is found in the NiFi admin guide:
https://nifi.apache.org/docs/nifi-docs/html/administration-guide.html#web-properties
Thanks,
Matt
Created 04-13-2018 05:05 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Matt Clarke,
It is ok.
"This Whitelist feature is already part of the HDF 3.1 release from Hortonworks and will be part of the Apache NiFi 1.6 release at a later time.
"
I thought that NIFI 1.5 (which is included in HDF 3.1) was not working and that HDF 3.1 provided throught ambari some Work around 🙂
Thanks for your help !
Best Regards
Abdou
Created 04-13-2018 05:21 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HDF is never running exactly the same version of Apache NiFi as you would find in the open community. Each HDF release is based off an Apache release version as the baseline with many bugs and/or enhancements added on top. So you may find apache bugs that are fixed in Apache NiFi 1.6 which are already fixed in the HDF 3.1 release.
Matt
Created 03-06-2018 05:58 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you can build NiFi, it is not so hard to back-port the whitelist feature to 1.5.0. You only need to cherry-pick two commits.
git clone -b rel/nifi-1.5.0 https://github.com/apache/nifi cd nifi # cherry-pick NIFI-4761 git cherry-pick 8cb09c301d6fef70cc8a02a4a7e80f3062ab58ae git cherry-pick e3c661daac69cdb2de43c3d66d9ed1ccc9c8dbc6 # If you need the tar ball mvn -T 2.0C clean install -DskipTests # If you need the RPM package mvn -T 2.0C clean install -DskipTests -Prpm
This works fine for us. Thanks.
Created 03-06-2018 05:38 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'll make sure to try this out, I hadn't thought of doing this.
Created 07-23-2018 06:52 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there a way to turn off the Header Request checking entirely? This is causing hoopla with load balancers. SSL will take care of this on its own, yes?
,Is there a way to disable the Request Header check? This causes hellavu problems with load balancers.
Created on 07-23-2018 07:25 PM - edited 08-17-2019 11:40 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is no way to disable the strict hostname checking. The purpose is prevent NiFI from responding to requests that were directed at a different target host.
-
If the incoming request has hostname abc.example.com in the header, It is expected that the PrivateKeyEntry in the keystore being used by NiFi has that exact same hostname defined either as its CN or as a Subject Alternative Name (SAN).
-
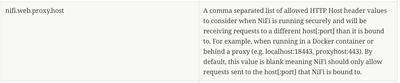
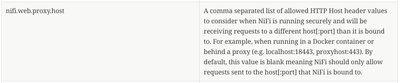
NiFi does provide a mechanism to get around this hostname checking in Apache NIFi 1.6.0 or (HDF 3.1.x) versions.
-
This new property would get added to the nifi.properties file.
-
Thank you,
Matt
-
If you found this Answer addressed your original question, please take a moment to login and click "Accept" below the answer.
Created 07-23-2018 07:42 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks. What I have found is that incoming requests from the LB (aws NLB) were being rejected, even when the LB DNS was part of the SAN in the cert. Setting the nifi.web.proxy.host = <LB DNS>:9091 stopped this from happening, but now there is an error saying that the hostname should be <X>, where X is the private DNS name of the node. I will try adding the private DNS entries to the SAN to see if this resolves. Thanks.
Created 10-21-2019 04:22 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Did adding Nifi hostnames to the load balancer certificate's SAN help?
- « Previous
- Next »