Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: [RESOLVED] : NIFI : LISTENHTTP SSL
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
[RESOLVED] : NIFI : LISTENHTTP SSL
- Labels:
-
Apache NiFi
Created 10-24-2016 09:36 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
I'm trying use listenhttp with ssl.
I've read this post : http://www.simonellistonball.com/technology/nifi-ssl-listenhttp/
But i don't know how use keystore from client. It is the same keystore than keystore used in nifi.properties ?
thanks
Created 10-24-2016 12:45 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SSL Certificates are generally issued per server. It would be extremely unusual to have multiple certificates issued for the same server or to issue certificates per piece of software. I am not saying you can't, but unnecessary.
Having said that, when you installed NiFi via Ambari, The NIfI CA that was installed likely generated the certificates needed for all your servers where NiFi is running its nodes. A quick look in the nifi.properties file for these jks files will reveal where to find them and the passwords for them as well (Default nifi.properties location on each node --> /etc/nifi/2.0.0.0-579/0/nifi.properties)
Now here is the hitch.... When the NiFi CA generates these keystores for your NiFi nodes, the keystore and truststore on every node end up with its own unique password. This will not work for the ssl context service you need to configure to make your ListenHTTP processor operate using SSL. This is because the same identical ssl context service will be used by the listenHTTP processor on each node.
There is a little work that needs to be done on each node to get you setup here, I suggest you make a copy of the keystore.jks and truststore.jks files on every node in to some new directory. Then capture the following lines from the nifi.properties file on each node:
nifi.security.keyPasswd=<keypass> nifi.security.keystore=/<path>/keystore.jks nifi.security.keystorePasswd=<keystore-password> nifi.security.keystoreType=jks nifi.security.truststore=/<path>/truststore.jks nifi.security.truststorePasswd=<truststore-password> nifi.security.truststoreType=jks
Lets assume you create a /opt/nifi-certs/ directory n every node and placed them there.
Next you will want to use the keytool command to change the password on the copies so that nifi.security.keyPasswd= uses the same password on every node, nifi.security.keystorePasswd= uses the same password on every node, and nifi.security.truststorePasswd= uses the same password on every node. While the contents of each certificate is unique to the server, the passwords used to access that key and keystore will then all be the same. This will allow you to configure your ssl-context service to use common passwords to access these server keystores on each node.
Below are the command you can use to change the keystore/trustore passwords and the key passwords within the keystore files.
For each keystore do the following:
keytool -storepasswd -new <new_storepass> -keystore keystore.jks
(Make sure you use the same <new_storepass> on every node in your nifi cluster.
keytool -keypasswd -alias [Alias name for private key] -keystore [path to key store]
(If you don't know your private key <alias>, you can get it by running the following command against your keystore.jks file. You will be prompted for yoru <new_storepassword> and the original <key-password>, and then allowed to set a >new-key-password>)
keytool -v --list -keystore keystore.jks
For each Truststore do the following:
keytool -storepasswd -new <new_trustpass> -keystore truststore.jks
(Make sure you use the same <new_trustpass> on every node in your nifi cluster.
After you have completed the above on every node you are ready to configure and start using the ssl-context service.
Thanks,
Matt
Created 09-17-2019 02:42 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Mat,
Sorry to post my question here not getting the way out.
I have configured SSL with CA signed certs on the Server.By CA signed i mean actual CA and not NIFI CA.
I am using Nifi on a single machine without Ambari.
Now i want a client to authenticate and use nifi , how to create the client cert so that it authenticates to the CA signed cert on server.
Created on 10-28-2016 09:21 AM - edited 08-18-2019 06:20 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
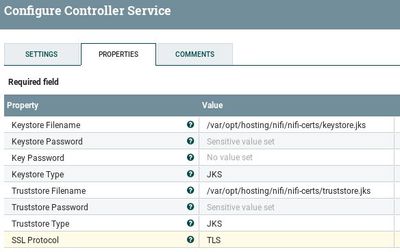
I've changed my configuration Controller Service but I'm running an issue
I've checked all truststore/keystore on all the cluster, their use same passwd
Created 10-28-2016 11:14 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It does not look like you provided you key password.
Created 10-31-2016 08:34 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now that ContextServiceSSL was enabled. I need to generate keystore for my client/user ?
Created 10-31-2016 01:03 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ListenHTTP requires 2-way SSL when enabled. So the client will also need a keystore and truststore. The Truststore on both your client and server will need to contain the trusted cert entry for each others client cert. If you used the same CA for both then you should be good. If not you will need to add the CA or trusted key entry (Public key from each private key entry.) to each others Truststores.
Created 02-05-2020 08:00 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Want to add some clarity to this last comment:
ListenHTTP requires 2-way TLS when enabled if a SSLContextService has been configured with a truststore. The truststore is used to trust the client certificate presented by the client, for the purpose of authentication, connecting to this secured ListenHTTP processor.
If only a keystore and no truststore is configured in the SSLContext service, the ListenHTTP will not require that clients present a client certificate.
The server certificate from the keystore will be presented to the client so the client can verify that it trusts the server (NiFI listenHTTP jetty server) that it is connecting with.
- « Previous
-
- 1
- 2
- Next »