Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: Ranger Policy change not affecting behavior
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Ranger Policy change not affecting behavior
- Labels:
-
Apache Hive
-
Apache Ranger
Created on 07-14-2016 07:34 PM - edited 08-19-2019 02:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am working through tutorial 410, and I'm running into an issue in the Hive Grant/Revoke Permission Scenarios section. After disabling the global access policies and invoking beeline as the it1 user, I can confirm the initial behavior of receiving an AccessControlException when attempting to run
GRANT select, update on table xademo.customer_details to user network1;
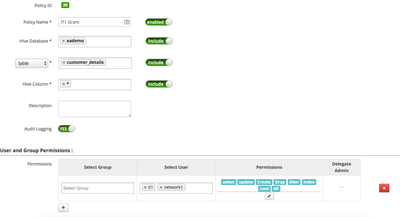
However, after implementing the new policy for the user it1, I am encountering the same exact behavior in beeline (AccessControlException). The configuration of the policy looks identical to the screenshot in the walkthrough.
What am I missing and how can I troubleshoot further?
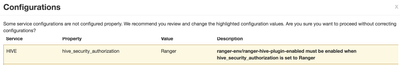
One additional note (see second screenshot), I am seeing the below configuration warning in Hive (I'm unsure whether this is related).
Created on 07-14-2016 07:53 PM - edited 08-19-2019 02:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Created on 07-14-2016 07:53 PM - edited 08-19-2019 02:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
you need to enable the delegate admin in you policy
Created 07-14-2016 07:53 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Deepak. So the screenshot is incorrect and needs to be updated? https://raw.githubusercontent.com/hortonworks/tutorials/hdp/assets/securing-hdfs-hive-hbase-with-kno...
Also, why would I want to delegate admin rights to the network1 user? I think the idea is for it1 to be able to grant permissions to network1 (but not for network1 to be able to grant permissions to any one else).
Created 07-14-2016 08:02 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
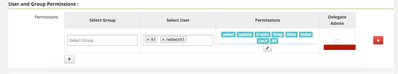
here what i mean is you remove network1 from your policy and enabel the delegate admin (chekbox next to permissions) privilege for it1,
now if you login to beeline as it1 and try to run the command:
GRANT select, update on table xademo.customer_details to user network1;
then network1 will get grant privilege and will get added as user in the the policy that belong to the resource xademo.customer_details , and delegate admin prvilege will not be enabled for it , it should create new policy item for it
Created 07-14-2016 08:16 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
for ex: i had policy for user1 with delegate admin yes on table t4 so i had run this command using user1
grant select,update on table t4 to user2
now my policy got new entry in it for user2 with select , update but delegate admin no as follows
Created 07-14-2016 09:40 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @deepak sharma, I will submit a Github issue as I believe this screenshot needs to be changed: https://raw.githubusercontent.com/hortonworks/tutorials/hdp/assets/securing-hdfs-hive-hbase-with-kno...
Created 09-27-2016 10:15 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have encountered the same issue. After specifying the first user "it1" as "Delegating admin", managing grant/revokes worked. I guess, a better policy would be to create a admin user "hive_admin" and delegate all admin activities to this user.