Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: CVE-2021-44228 - log4j Arbitrary RCE
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
log4j2 vulnerability (CVE-2021-44228)
- Labels:
-
Apache Hadoop
-
Cloudera Manager
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I wanted to ask if there's a page / instructions / info regarding the recent log4j2 vulnerability (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228) and how it can affect Cloudera CDH setups? If it does affect, what are the recommended mitigations on it?
Thanks,
Mor
Created 12-12-2021 01:41 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is in deed an important question.
Created 12-12-2021 01:33 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Following - Cloudera please provide recommendations as this is really urgent.
Created 12-12-2021 07:26 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please go through below apache docs, its might help
Created 12-24-2021 12:05 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
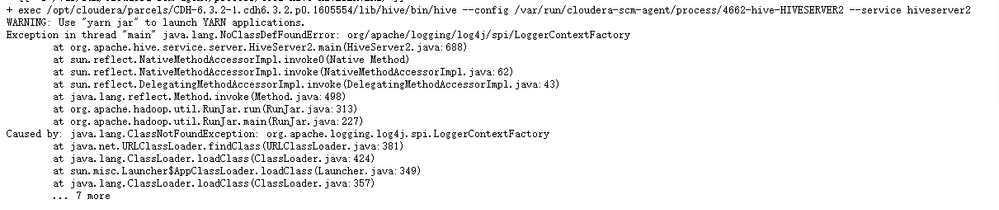
I upgraded log4j to 2.17 0, but the following error occurred when restarting hiveserver2:
Created 12-12-2021 11:30 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
Is there any impact of CVE-2021-44228 - log4j Arbitrary RCE on CDH 5.x and 6.x??
Regards,
Hanu
Created 12-13-2021 05:59 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cloudera platform security teams are actively assessing the impact to our on-premises and cloud products and will provide an impact analysis update to customers as soon as possible.
Cy Jervis, Manager, Community Program
Was your question answered? Make sure to mark the answer as the accepted solution.
If you find a reply useful, say thanks by clicking on the thumbs up button.
Created 12-13-2021 01:41 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Team,
Currenlty in our organization we are using Cloudera 6.3.1 express edition, recently our company security team came up with log4j CVE-2021-44228 vulnerable, Could you please suggest due to this any problem for cloudera ?
Thanks
Srikanth
Created 12-13-2021 02:04 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I second this question. I currently administer a CDH 5.16 cluster that we're in the process of upgrading to CDP 7.x. Is there a statement from cloudera about the extent of the vulnerablility in their products and how we can go about patching it?
Created 12-13-2021 02:19 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could you please refer to below url , this statement came from apache, but not from Cloudera.
https://logging.apache.org/log4j/2.x/security.html
Thanks
Srikanth