Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: problem generating keytab with HTTP SPN
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
problem generating keytab with HTTP SPN
- Labels:
-
Apache Hadoop
-
Cloudera Manager
Created 08-22-2022 11:44 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello cloudera community,
we are trying to create a keytab with the main one:
"HTTP/hostname@DOMAIN.LOCAL"
with the command:
ktpass -princ HTTP/hostname@DOMAIN.LOCAL -mapuser livy-http -crypto ALL -ptype KRB5_NT_PRINCIPAL -pass password2022 -target domain.local -out c:\temp\livy-http.keytab
but I try to validate the ticket with this keytab returns the error:
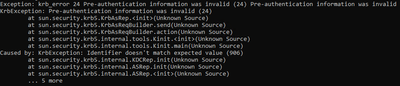
Exception: krb_error 24 Pre-authentication information was invalid (24) Pre-authentication information was invalid
KrbException: Pre-authentication information was invalid (24)
at sun.security.krb5.KrbAsRep.<init>(Unknown Source)
at sun.security.krb5.KrbAsReqBuilder.send(Unknown Source)
at sun.security.krb5.KrbAsReqBuilder.action(Unknown Source)
at sun.security.krb5.internal.tools.Kinit.<init>(Unknown Source)
at sun.security.krb5.internal.tools.Kinit.main(Unknown Source)
Caused by: KrbException: Identifier doesn't match expected value (906)
at sun.security.krb5.internal.KDCRep.init(Unknown Source)
at sun.security.krb5.internal.ASRep.init(Unknown Source)
at sun.security.krb5.internal.ASRep.<init>(Unknown Source)
... 5 more
this user "livy-http" is already created in AD and with the SPN "HTTP/hostname@DOMAIN.LOCAL" attached to it
what are we doing wrong?
Created 08-23-2022 09:21 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @JQUIROS
the command to create the entry was:
add_entry -password -p HTTP/hostname@DOMAIN.LOCAL -k 1 -e rc4-hmac
then export the keytab with the command:
wkt http.keytab
and then to validate the tiker the command:
KRB5_TRACE=/dev/stdout kinit -kt http.keytab HTTP/hostname@DOMAIN.LOCAL
presented the error:
Getting initial credentials for HTTP/hostname@DOMAIN.LOCALLooked up etypes in keytab: rc4-hmac
Sending unauthenticated request
Sending request (237 bytes) to DOMAIN.LOCAL
Sending initial UDP request to dgram 172.22.22.22:88
Received answer (229 bytes) from dgram 172.22.22.22:88
Response was from master KDC
Received error from KDC: -1765328359/Additional pre-authentication required
Preauthenticating using KDC method data
Processing preauth types: PA-PK-AS-REQ (16), PA-PK-AS-REP_OLD (15), PA-ETYPE-INFO2 (19), PA-ENC-TIMESTAMP (2)
Selected etype info: etype rc4-hmac, salt "", params ""
Retrieving HTTP/hostname@DOMAIN.LOCAL from FILE:http.keytab (vno 0, enctype rc4-hmac) with result: 0/Success
AS key obtained for encrypted timestamp: rc4-hmac/20C1
Encrypted timestamp (for 1661441475.76781): plain 301AA011199992303232BED, encrypted 3625254347B405C2739999992C5C50F451C0A477AE3AD421DF
Preauth module encrypted_timestamp (2) (real) returned: 0/Success
Produced preauth for next request: PA-ENC-TIMESTAMP (2)
Sending request (313 bytes) to DOMAIN.LOCAL
Sending initial UDP request to dgram 172.22.22.22:88
Received answer (196 bytes) from dgram 172.22.22.22:88
Response was from master KDC
Received error from KDC: -1765328360/Preauthentication failed
Preauthenticating using KDC method data
Processing preauth types: PA-ETYPE-INFO2 (19)
Selected etype info: etype rc4-hmac, salt "", params ""
kinit: Preauthentication failed while getting initial credentials
Created 08-23-2022 09:55 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We need to reach out the AD support, the response is coming from the AD
Response was from master KDC
Received error from KDC: -1765328360/Preauthentication failed
Preauthenticating using KDC method data
Processing preauth types: PA-ETYPE-INFO2 (19)
Selected etype info: etype rc4-hmac, salt "", params ""
kinit: Preauthentication failed while getting initial credentials
[0] Reference: https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-kile/ae60c948-fda8-45c2-b1d1-a71b484...
Created 08-25-2022 05:00 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What do you need the keytab with the HTTP principal for?
André
Was your question answered? Please take some time to click on "Accept as Solution" below this post.
If you find a reply useful, say thanks by clicking on the thumbs up button.
Created 08-26-2022 05:29 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @araujo
to use in the livy service, as requested in the processes in the links below:
https://danielfrg.com/blog/2018/08/spark-livy/
https://enterprise-docs.anaconda.com/en/latest/admin/advanced/config-livy-server.html
Created 08-26-2022 06:55 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The problem is that to generate a keytab for any principal you need to know the password for that principal. The HTTP/hostname principal probably already exists in your AD and has some unknown password. Without knowing that you would have to reset the principal password to be able to create a keytab for it. And if you reset its password you will invalidate any keytabs that already exist for that principal that other services may be using.
Cheers,
André
Was your question answered? Please take some time to click on "Accept as Solution" below this post.
If you find a reply useful, say thanks by clicking on the thumbs up button.
Created 08-29-2022 06:33 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @araujo
the ad has two users:
livy
livy-http
the user livy has the SPN:
livy/hostname@DOMAIN.LOCAL
and it is working without problem in kinit
the user livy-http has the SPN:
HTTP/hostname@DOMAIN.LOCAL
but it is showing the error described above
Created 08-29-2022 03:54 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you know the passwords for the users livy and livy-http? Can you manually kinit with those 2 users from the command line?
Can you also check in AD what's the value for userPrincipalName property of those two users and share it here?
Cheers,
André
Was your question answered? Please take some time to click on "Accept as Solution" below this post.
If you find a reply useful, say thanks by clicking on the thumbs up button.
Created 08-30-2022 05:41 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @araujo
yes, we know the passwords, because we created these two users from scratch
before creating the keytabs for the two users, we managed to kinit the two users without problem "kinit user", after creating the keytabs for the two users, kinit only works with the keytab, but it only works on the livy user, when we try to run kinit in livy-http user keytab displays the error "kinit: Preauthentication failed while getting initial credentials"
the userprincipalname of each user is:
livy:
livy/hostname_livy_server@DOMAIN.LOCAL
livy-http:
HTTP/hostname_livy_server@DOMAIN.LOCAL
Created 08-30-2022 06:32 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The names you listed are the servicePrincipalName. These are different from the userPrincipalName. Could you please check the latter and let me know what they are?
Cheers,
André
Was your question answered? Please take some time to click on "Accept as Solution" below this post.
If you find a reply useful, say thanks by clicking on the thumbs up button.
Created 08-30-2022 06:36 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could you please run the kinit commands for both accounts and share a screenshot showing the command line and the output?
Was your question answered? Please take some time to click on "Accept as Solution" below this post.
If you find a reply useful, say thanks by clicking on the thumbs up button.