I have NIFI single Node and for my learning purpose I'm trying to implement SiteToSiteBulletinReporyingTask (with assuming this will work for single node)
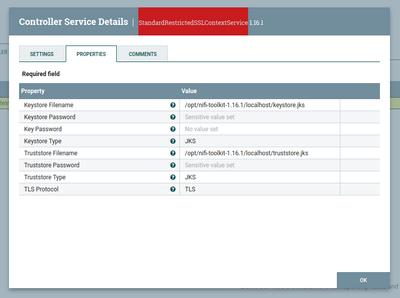
I configured StandardRestrictedSSLContextService as below
Note - same keystore and truststore used inside nifi-properties
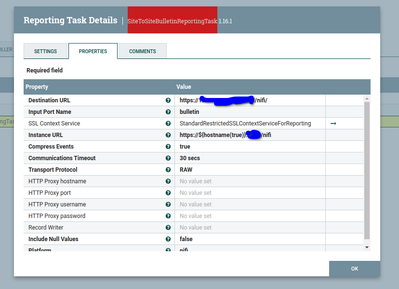
I configured SiteToSiteBulletinReportingTask as below
Note - the destination URL is the same URL that nifi is currently running.
Now I'm facing below issues -
I'm not receiving any data to the bulletin port. I'm getting the
below warning message in nifi-app.log (couldn't find resource to fix this)
The issue is I'm getting the below warning and, to be honest, I don't have a clear idea about this warning, and also
2022-10-23 17:57:09,618 WARN [NiFi Site-to-Site Connection Pool Maintenance] o.apache.nifi.remote.client.PeerSelector Unable to refresh remote group peers due to: Certificate for <xxx.xxx.xx.xxx> doesn't match any of the subject alternative names: [localhost] 2022-10-23 17:57:09,618 WARN [NiFi Site-to-Site Connection Pool Maintenance] o.a.n.r.SiteToSiteBulletinReportingTask SiteToSiteBulletinReportingTask[id=105311a0-1473-1059-2fb8-ea483b8d9fa8] Unable to refresh remote group peers due to: Certificate for <xxx.xxx.xx.xxx> doesn't match any of the subject alternative names: [localhost]

