Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: Error while enabling kerberos on ambari
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Error while enabling kerberos on ambari
- Labels:
-
Apache Ambari
Created on 05-13-2019 08:48 AM - edited 08-17-2019 03:28 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
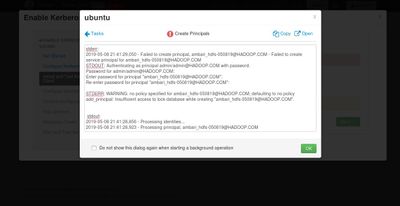
I receive an error while enabling kerberos on ambari as below;
i have installed krb5-kdc krb5-admin-server and config krb5.conf, kdc.conf and kadm5.acl then created new principle (as attached)
Note when i wrote the realm name in the kdc file in uppercase letter i got an error while using kadmin.local master key cannot be fetch, it only works in lowercase letter
Also when i try to restart the krb5 services, it said service can't be found although it is running so i restart the server instead
Last thing when i installed krb5-kdc krb5-admin-server the /var/kerberos folder didn't create automatically and i had to create it manually.
Please help me solve this issue, thank you in advanced.
Created 05-13-2019 07:04 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is something I don't understand can you share how you create the KDC database? How come you have a principal "ambari_hdfs-050819@HADOOP.COM"?
I suggest starting afresh so delete/destroy the current KDC as the root user or sudo on ubuntu whichever is appropriate
# sudo kdb5_util -r HADOOP.COM destroy
Accept with a "Yes"
Now create a new Kerberos database
Complete remove Kerberos
$ sudo apt purge -y krb5-kdc krb5-admin-server krb5-config krb5-locales krb5-user krb5.conf $ sudo rm -rf /var/lib/krb5kdc
Do a refresh installation
First, get the FQDN of your kdc server for this example
# hostanme -f test.hadoop.com
Use the above output for a later set up
# apt install krb5-kdc krb5-admin-server krb5-config
Proceed as follow
At the prompt for the Kerberos Realm = HADOOP.COM Kerberos server hostname = test.hadoop.com Administrative server for Kerberos REALM = test.hadoop.com
Configuring krb5 Admin Server
# krb5_newrealm
Open /etc/krb5kdc/kadm5.acl it should contain a line like this
*/admin@HADOOP.COM *
The kdc.conf should be adjusted to look like this
[kdcdefaults]
kdc_ports = 88
kdc_tcp_ports = 88
[realms]
HADOOP.COM = {
#master_key_type = aes256-cts
acl_file = /var/kerberos/krb5kdc/kadm5.acl
dict_file = /usr/share/dict/words
admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab
supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal camellia256-cts:normal camellia128-cts:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal
}The krb5.conf should look like this if you are on a multi-node cluster this is the fines you will copy to all other hosts, notice the entry under domain_realm?
[libdefaults]
renew_lifetime = 7d
forwardable = true
default_realm = HADOOP.COM
ticket_lifetime = 24h
dns_lookup_realm = false
dns_lookup_kdc = false
default_ccache_name = /tmp/krb5cc_%{uid}
#default_tgs_enctypes = aes des3-cbc-sha1 rc4 des-cbc-md5
#default_tkt_enctypes = aes des3-cbc-sha1 rc4 des-cbc-md5
[domain_realm]
.hadoop.com = HADOOP.COM
hadoop.com = HADOOP.COM
[logging]
default = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
kdc = FILE:/var/log/krb5kdc.log
[realms]
HADOOP.COM = {
admin_server = test.hadoop.com
kdc = test.hadoop.com
}Restart the Kerberos kdc daemons and kerberos admin servers:
# for script in /etc/init.d/krb5*; do $script restart; done
Don't manually create any principle like the "ambari_hdfs-050819@HADOOP.COM"
Go to the ambari kerberos wizard for the domain notice the . (dot)
kdc host = test.hadoop.com Real Name = HADOOP.COM Domains = .hadoop.com ,hadoop.com ----- kadmin host = test.hadoop.com Admin principal = admin/admin@HADOOP.COM Admin password = password set during the creation of kdc database
Now from here just accept the default the keytabs should generate successfully. I have attached files to guide you Procedure to Kerberize HDP 3.1_Part2.pdfProcedure to Kerberize HDP 3.1_Part1.pdf Procedure to Kerberize HDP 3.1_Part3.pdf
Hope that helps please revert if you have any questions
Created on 05-20-2019 03:06 PM - edited 08-17-2019 03:28 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, sorry for keep disturbing you, hope i can solve this issue unfortunately after i followed you steps i got back the same error as before shown bellow 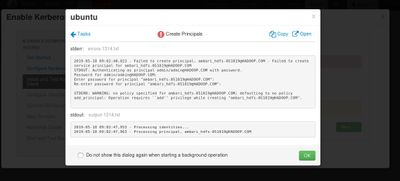
note that i didnt create principle ambari_hdfs-051819@HADOOP.COM i only created admin/admin@HADOOP.COM as you mentioned before and actually ambari_hdfs is my cluster name, any solution for this?
Thank you so much in advanced .
Created 05-20-2019 04:59 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The above question and the replies below were originally posted in the Community Help Track. On Mon May 20 16:56 UTC 2019, a member of the HCC moderation staff moved it to the Security track. The Community Help Track is intended for questions about using the HCC site itself.
Was your question answered? Make sure to mark the answer as the accepted solution.
If you find a reply useful, say thanks by clicking on the thumbs up button.
Created 05-22-2019 07:40 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
Any other solution i can do to solve this issue?
Created 05-22-2019 08:51 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unbelievable ping me on linkedin ,could help with remote
Created 01-13-2020 03:37 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry for the bump. I tried this in the HDP Sandbox and discovered that installing krb5-workstation-1.15.1-37.el7_7.2.x86_64.rpm solved the problem
- « Previous
-
- 1
- 2
- Next »