Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: How to fix test Kerberos client?
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to fix test Kerberos client?
- Labels:
-
Apache Ambari
Created 10-27-2017 11:36 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I'm trying to set up Kerberos automatically on my cluster, which is composed of 2 nodes (ambari-server and ambari-agent1).
I've installed KDC and KDC admin server on ambari-server.
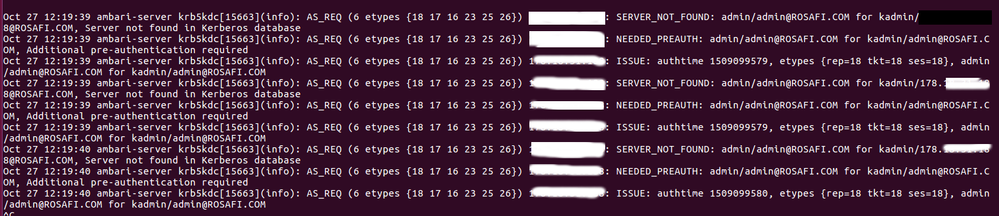
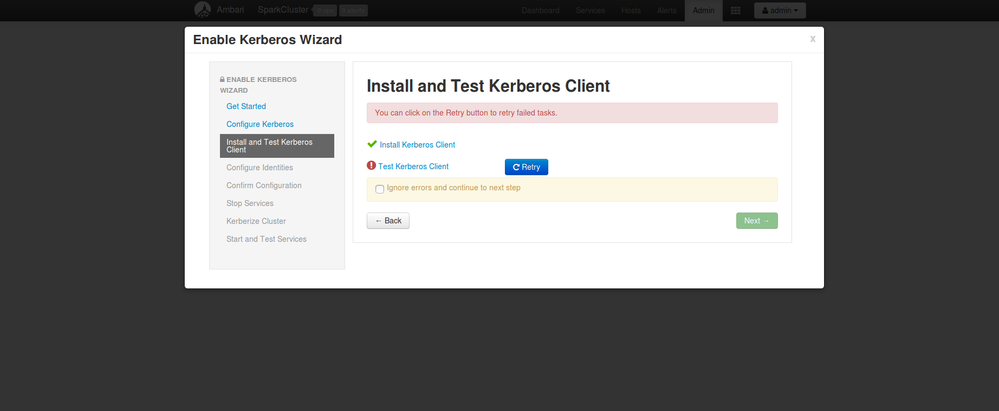
I've followed this link https://docs.hortonworks.com/HDPDocuments/HDP2/HDP-2.6.2/bk_security/content/_launching_the_kerberos..., the 2.Authentication and I'm stuck in Launching the kerberos Wizard (Automated Setup) when i tried to test kerberos client as shown in "error.png".
I attached the logs that can be related to this issue in "1_log.png" from /var/log/krb5kdc.log and in "2_log.png" from
/var/log/krb5.log.
My question are:
1- What does this prerequisite "Ambari server and all cluster hosts have network access to both the KDC and KDC admin hosts" mentioned as the first one in "prerequisites for kerberos.png" mean? What are the necessary steps to be done to ensure this
prerequisite?
2- Where can i find the default log attached to kerberos?
3- Is it possible that the test kerberos client is failed for ambari-server because I've installed on it both KDC and kerberos client?
4- How can i debug the errors mentioned in "1_log.png" and "2_log.png"?
I'm really stuck, I'll be grateful if you try to help me resolve this issue?


Created 10-27-2017 12:18 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It seems like there may be an issue with the configuration of your KDC. Make sure the "admin" account you are using has rights to create accounts in the KDC. In my setup, any user with /admin in their principal name has fully rights to the KDC:
# cat /var/kerberos/krb5kdc/kadm5.acl */admin@EXAMPLE.COM *
Try to manually create an account first to make sure your account has the proper rights. In my case, my admin user is admin/admin@EXAMPLE.COM:
# kadmin -p admin/admin Authenticating as principal admin/admin with password. Password for admin/admin@EXAMPLE.COM: kadmin: add_principal test_user WARNING: no policy specified for test_user@EXAMPLE.COM; defaulting to no policy Enter password for principal "test_user@EXAMPLE.COM": Re-enter password for principal "test_user@EXAMPLE.COM": Principal "test_user@EXAMPLE.COM" created. kadmin:
The test above, done from the Ambari server, ensure that the krb5.conf is set up properly, the admin user credentials are correct, and the admin user has rights to create principals. If you cannot perform the same, something is wrong with the KDC config. If the problem is related to the /etc/krb5.conf file, make sure you enter the correct information into Ambari's Enable Kerberos Wizard fields. For example, the hostname of the KDC should not be localhost, it should be the FQDN (fully qualified domain name) of the host where the KDC is.
For more research on the error, take a look at the Ambari server log (/var/log/ambari-server/ambari-server.log). There may be more information on the error there.
Created 10-27-2017 12:18 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It seems like there may be an issue with the configuration of your KDC. Make sure the "admin" account you are using has rights to create accounts in the KDC. In my setup, any user with /admin in their principal name has fully rights to the KDC:
# cat /var/kerberos/krb5kdc/kadm5.acl */admin@EXAMPLE.COM *
Try to manually create an account first to make sure your account has the proper rights. In my case, my admin user is admin/admin@EXAMPLE.COM:
# kadmin -p admin/admin Authenticating as principal admin/admin with password. Password for admin/admin@EXAMPLE.COM: kadmin: add_principal test_user WARNING: no policy specified for test_user@EXAMPLE.COM; defaulting to no policy Enter password for principal "test_user@EXAMPLE.COM": Re-enter password for principal "test_user@EXAMPLE.COM": Principal "test_user@EXAMPLE.COM" created. kadmin:
The test above, done from the Ambari server, ensure that the krb5.conf is set up properly, the admin user credentials are correct, and the admin user has rights to create principals. If you cannot perform the same, something is wrong with the KDC config. If the problem is related to the /etc/krb5.conf file, make sure you enter the correct information into Ambari's Enable Kerberos Wizard fields. For example, the hostname of the KDC should not be localhost, it should be the FQDN (fully qualified domain name) of the host where the KDC is.
For more research on the error, take a look at the Ambari server log (/var/log/ambari-server/ambari-server.log). There may be more information on the error there.
Created 10-27-2017 01:39 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
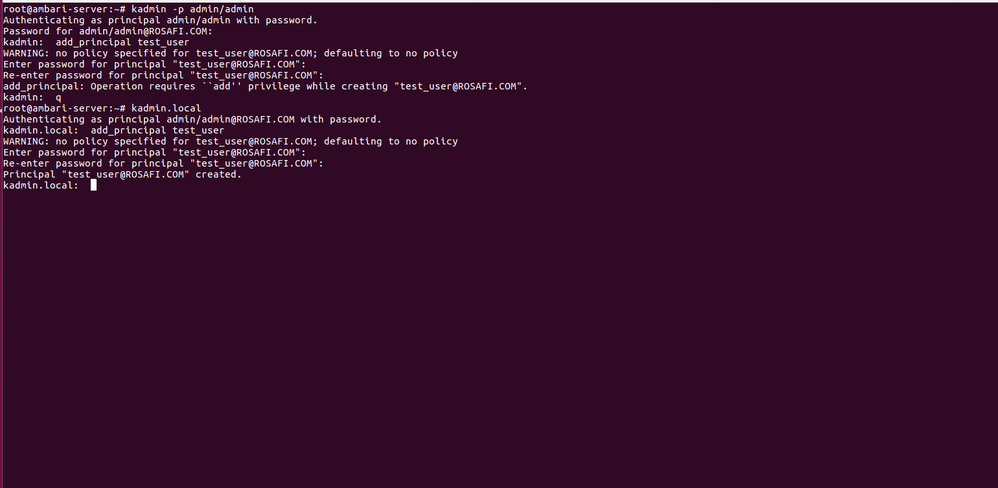
Thank you for your reply. I've tried the test above and the result are attached in "test.png".
I've concluded that my admin account does not have the proper rights to create accounts.
I've edited my /var/kerberos/krb5kdc/kadm5.acl from
*/admin *
to
*/admin@ROSAFI.COM *
and I've restarted my krb5-admin -server and krb5-kdc.
From/var/log/ambari-server/ambari-server.log, i got this error as you have expected:
27 Oct 2017 15:42:45,206 ERROR [Server Action Executor Worker 2313] MITKerberosOperationHandler:207 - Failed to execute kadmin query: add_principal -pw "********" sparkcluster-102717@ROSAFI.COM STDOUT: Authenticating as principal admin/admin@ROSAFI.COM with password. Password for admin/admin@ROSAFI.COM: Enter password for principal "sparkcluster-102717@ROSAFI.COM": Re-enter password for principal "sparkcluster-102717@ROSAFI.COM": STDERR: WARNING: no policy specified for sparkcluster-102717@ROSAFI.COM; defaulting to no policy add_principal: Operation requires ``add'' privilege while creating "sparkcluster-102717@ROSAFI.COM".
So, for now my questions are:
1- How can i set the proper rights to my admin account?
2- What is the difference between "kadmin.local" and "kadmin -p admin/admin"?
Would you please help me to continue with resolving this issue?
Created 10-27-2017 04:17 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
kadmin.local is only available on the KDC server host. It is a utility that basically manages the KDC DB directly, which by passes the user set in the relative Kerberos ticket cache.
kadmin is a tool that comes with the Kerberos client suite, It connects to the kadmin service and uses the user's Kerberos ticket cache to determine who the acting user is and what privs they have. If the user does not have the appropriate privileges then the action will fail - as you see in your test.
For my (test) environment, I have it set so that any principal with "/admin" in the name can perform any administrative task. So using kadmin.local, I create a principal with the name "admin/admin" and set its password. Then I edit the /var/kerberos/krb5kdc/kadm5.acl file and set it as shown above:
*/admin@EXAMPLE.COM *
Then, I restart the kadmind and krb5kdc services. After that, I can manage the KDC using
kadmin -p admin/admin
I uploaded install-kdc-sh.txt. This is the script I use when installing a KDC in my test environment on Centos6
Created 10-27-2017 04:55 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your detailed explanation. With these details, i've resolved my issue. It was a problem in my kadm5.acl.

