Support Questions
- Cloudera Community
- Support
- Support Questions
- NiFi Authentication with LDAP
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NiFi Authentication with LDAP
- Labels:
-
Apache NiFi
Created 02-02-2023 10:31 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
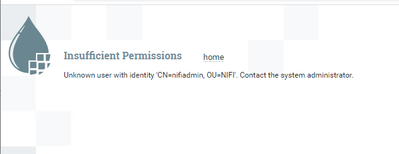
I have installed Apache nifi 1.19.1 and configured the ssl using below command
./tls-toolkit.sh standalone -n 'nifi1,nifi2,nifi3' -B MyPassword -C 'CN=nifiadmin,OU=NIFI' -O -o /opt/nificert
and it was wotking fine after importing the certificate in my browser.
Then configured LDAP like below:-
loginIdentityProviders
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<loginIdentityProviders>
<provider>
<identifier>ldap-provider</identifier>
<class>org.apache.nifi.ldap.LdapProvider</class>
<property name="Authentication Strategy">SIMPLE</property>
<property name="Manager DN">cn=Myuser,ou=Myuser,dc=Mydomain,dc=com</property>
<property name="Manager Password">Mypassword</property>
<property name="Referral Strategy">FOLLOW</property>
<property name="Connect Timeout">10 secs</property>
<property name="Read Timeout">10 secs</property>
<property name="Url">ldap://x.x.x.x:389</property>
<property name="User Search Base">dc=Mydomain,dc=com</property>
<property name="User Search Filter">(sAMAccountName={0})</property>
<property name="Identity Strategy">USE_USERNAME</property>
<property name="Authentication Expiration">12 hours</property>
</provider>
</loginIdentityProviders>
authorizers
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<authorizers>
<userGroupProvider>
<identifier>file-user-group-provider</identifier>
<class>org.apache.nifi.authorization.FileUserGroupProvider</class>
<property name="Users File">./conf/users.xml</property>
<property name="Legacy Authorized Users File"></property>
<property name="Initial User Identity 2">CN=nifi1, OU=NIFI</property>
<property name="Initial User Identity 3">CN=nifi2, OU=NIFI</property>
<property name="Initial User Identity 4">CN=nifi3, OU=NIFI</property>
<property name="Initial User Identity 1">cn=Myuser,ou=Myuser,dc=Mydomain,dc=com</property>
</userGroupProvider>
<userGroupProvider>
<identifier>ldap-user-group-provider</identifier>
<class>org.apache.nifi.ldap.tenants.LdapUserGroupProvider</class>
<property name="Authentication Strategy">SIMPLE</property>
<property name="Manager DN">cn=Myuser,ou=Myuser,dc=Mydomain,dc=com</property>
<property name="Manager Password">Mypassword</property>
<property name="Referral Strategy">FOLLOW</property>
<property name="Connect Timeout">10 secs</property>
<property name="Read Timeout">10 secs</property>
<property name="Url">ldap://Mydomain:389</property>
<property name="Page Size"></property>
<property name="Sync Interval">30 mins</property>
<property name="Group Membership - Enforce Case Sensitivity">false</property>
<property name="User Search Base">dc=Mydomain,dc=com</property>
<property name="User Object Class">person</property>
<property name="User Search Scope">ONE_LEVEL</property>
<property name="User Search Filter">(uid=*)</property>
<property name="User Identity Attribute">cn</property>
<property name="User Group Name Attribute"></property>
<property name="User Group Name Attribute - Referenced Group Attribute"></property>
<property name="Group Search Base"></property>
<property name="Group Object Class">group</property>
<property name="Group Search Scope">ONE_LEVEL</property>
<property name="Group Search Filter"></property>
<property name="Group Name Attribute"></property>
<property name="Group Member Attribute"></property>
<property name="Group Member Attribute - Referenced User Attribute"></property>
</userGroupProvider>
<userGroupProvider>
<identifier>composite-configurable-user-group-provider</identifier>
<class>org.apache.nifi.authorization.CompositeConfigurableUserGroupProvider</class>
<property name="Configurable User Group Provider">file-user-group-provider</property>
<property name="User Group Provider 1">ldap-user-group-provider</property>
</userGroupProvider>
<accessPolicyProvider>
<identifier>file-access-policy-provider</identifier>
<class>org.apache.nifi.authorization.FileAccessPolicyProvider</class>
<property name="User Group Provider">composite-configurable-user-group-provider</property>
<property name="Authorizations File">./conf/authorizations.xml</property>
<property name="Initial Admin Identity">cn=Myuser,ou=Myou,dc=Mydomain,dc=com</property>
<property name="Legacy Authorized Users File"></property>
<property name="Node Identity 1">CN=nifi1, OU=NIFI</property>
<property name="Node Identity 2">CN=nifi2, OU=NIFI</property>
<property name="Node Identity 3">CN=nifi3, OU=NIFI</property>
<property name="Node Group"></property>
</accessPolicyProvider>
<authorizer>
<identifier>managed-authorizer</identifier>
<class>org.apache.nifi.authorization.StandardManagedAuthorizer</class>
<property name="Access Policy Provider">file-access-policy-provider</property>
</authorizer>
</authorizers>
I also changed nifi.properities
but still getting below error
Any help will be high appreciated
Created 02-02-2023 12:32 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Based on above output your initial admin set in the file-access-policy provider needs to be "initialdmin" as that is what you typed in the login UI and that is likely the string being returned by your ldap for the cn attribute for this user.
Matt
Created 02-02-2023 10:57 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A secured NiFi will always "WANT" a clientAuth certificate for client/user authentication even if you have configured additional method of user authentication. So when you access the NiFi UI your browser returns the clientAuth certificate you loaded in the TLS exchange. When No other method of user/client authentication is configured, NiFi will "REQUIRE" a userAuth certificate. When alternate method of authentication are configured, NiFi will "WANT" a clientAuth certificate. This cannot be disabled. NiFi nodes need to communicate with one another in a cluster and the Nodes clientAuth certificates are used to facilitate that authentication and authorization. Other features of NiFi like Site-To-Site also will uses a mutualTLS auth.
Removing the client certificate from your browser or using a different browser where you have not loaded that certificate would result in NiFi moving on to next configured authentication method (provided those alternate methods are properly configured).
Also important that you understand that modifications to the file-user-group-provider and/or file-access-policy provider will not result in those changes being applied to existing users.xml and/or authorizations.xml files those providers generate. Based on your exception for your certificate based nifiadmin user, I am guessing you did remove these files so they got regenerated on startup using the newly defined initial admin Identity.
When you say you changed your nifi.properties file, i assume that to mean you changed the configuration for the login provider:
nifi.security.user.login.identity.provider=ldap-provider
Try using a different browser where you have not installed the nifiadmin certificate.
If you found that the provided solution(s) assisted you with your query, please take a moment to login and click Accept as Solution below each response that helped.
Thank you,
Matt
Created 02-02-2023 11:14 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@JobBranwl
Within your authorizers.xml file you can NOT have multiple user-group providers return the same user identity string.
I see you creating the following user identity string in the file-user-group-provider
cn=Myuser,ou=Myuser,dc=Mydomain,dc=com
and also see in your ldap-user-group-provider that you may be trying to sync the sme user from your LDAP. But in that sync configuration you are telling the provider to use the value returned by the "cn" attribute as the user identity. This I suspect would return just "Myuser". So NiFi would treat these two identities as different users.
Now looking at your ldap-provider (user for user authentication) and see this concern:
<property name="User Search Filter">(sAMAccountName={0})</property> This ldap-provider performs a ldap search where the username entered at the NiFi login window is substituted in place of the "{0}". Are you using AD (commonly where I'd expect to see a "sAMAccountName" attribute to be used)? If this attribute does not exist on your ldap/AD users, your login is not going to be successful. Perhaps you meant to use "cn={0}" here?
I also see that your have configured the following in the ldap-provider:
<property name="Identity Strategy">USE_USERNAME</property>
This property tells the ldap-provider what to use as the user's identity post successful authentication.
With "USE_USERNAME", the username (case sensitive) enter in the login window is used. "USE_DN" will use the full DN returned by ldap/AD as the user identity.
So with your current setup i expect your authorization will fail as your "username" will be passed to your configured authorizer where in your file-access-policy provider you have configured your initial admin to use a full DN.
Additionally, NIFi provides configuration properties that can be used to manipulate the user identity and or group identity strings returned via authentication should you choose to go that route.
https://nifi.apache.org/docs/nifi-docs/html/administration-guide.html#identity-mapping-properties
So once you get past your login window issue, you'll need to resolve above.
If you found that the provided solution(s) assisted you with your query, please take a moment to login and click Accept as Solution below each response that helped.
Thank you,
Matt
Created on 02-02-2023 11:37 AM - edited 02-02-2023 12:08 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK @MattWho , I will make the below change, are they ok?
<property name="User Search Filter">cn={0}</property>
<property name="Identity Strategy">USE_DN</property>
nifi.security.identity.mapping.pattern.dn=^cn=(.*?),ou=(.*?),dc=(.*?),dc=(.*?),dc=(.*?)$
nifi.security.identity.mapping.value.dn=$1
nifi.security.identity.mapping.transform.dn=NONE
And regarding 2 file-user-group-provider If I commented or deleted "Initial User Identity" valuse in the first property I got error
Unable to locate initial admin cn=initial-admin,ou=initail-admin-ou,dc=domain,dc=com to seed policies at org.apache.nifi.authorization.FileAccessPolicyProvider.populateInitialAdmin(FileAccessPolicyProvider.java:678)
I'm little confused in that
Created 02-02-2023 12:30 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So your ldap-user-group-provider is returning the value from the "cn" attribute which is likely just:
initial-admin However, you set your initial admin identity in the file-access-policy provider to a full DN. So when that provider attempts to build the authorization.xml, it can't because neither provider returned that identity string.
I recommend you leave Identity strategy as "USE_USERNAME" (most commonly used).
I also recommend setting your initial admin identity in the file-access-policy provider to your admin username and not the full DN.
You can also add a logger to the NiFi logback.xml that will result in all the user and group identities strings being output in the nifi-app.log for inspection by you to aid in yoru troubleshooting here:
<logger name="org.apache.nifi.ldap.tenants.LdapUserGroupProvider" level="DEBUG"/> Just scroll down in your logback until you start seeing logger lines and add this one.
User and groups produced by the user-group providers are assigned a uuid. That uuid is then used when assigning policies in the authorization.xml. That is why a user-group provider must return an identity in order to set permissions or seed initial policies against a user. That is why you got that exception.
If you found that the provided solution(s) assisted you with your query, please take a moment to login and click Accept as Solution below each response that helped.
Thank you,
Matt
Created on 02-02-2023 11:16 AM - edited 02-02-2023 11:20 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@MattWho Thanks for your Reply
Yes, I removed users.xml and authorizations.xml as I did some changes & want the nodes to inherite the new policies
Yes, I made the below change in nifi.properities file
nifi.security.user.login.identity.provider=ldap-provider
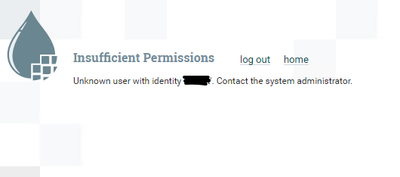
And indeed after using another laptop to access nifi it moved to the next step which I was about to login using the initial admin but it fails like below
And this from the nifi-user.log
2023-02-02 21:18:29,980 INFO [NiFi Web Server-404] o.a.n.w.a.c.AccessDeniedExceptionMapper identity[initialAdmin], groups[] does not have permission to access the requested resource. Unknown user with identity 'initialAdmin'. Returning Forbidden response.
Appreciate your valuable input 😅
Created 02-02-2023 12:32 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Based on above output your initial admin set in the file-access-policy provider needs to be "initialdmin" as that is what you typed in the login UI and that is likely the string being returned by your ldap for the cn attribute for this user.
Matt
Created on 02-02-2023 01:11 PM - edited 02-02-2023 09:41 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@MattWho, THANKS NOW I'M ABLE TO LOGIN USING THE INITIAL ADMIN 🕺🏻