Support Questions
- Cloudera Community
- Support
- Support Questions
- Nifi InvokeHttp using UsernameToken security
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Nifi InvokeHttp using UsernameToken security
- Labels:
-
Apache NiFi
-
Security
Created 03-07-2022 08:42 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
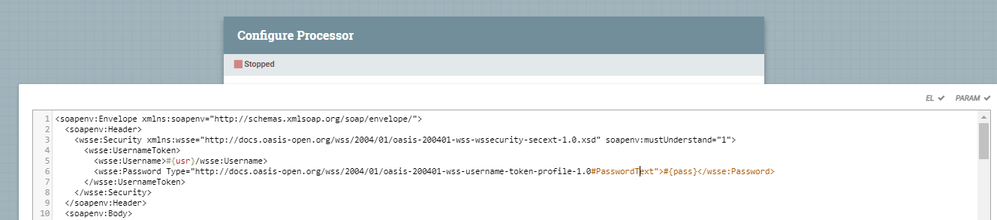
I need to call a soap service that is secured with WS-Security username token authentication and not basic auth. I also need to rely on the Parameter Context value for the id and password. I am using replace text to crate the soap request with the http header. When I try to reference the password it says I cannot due to the fact its sensitive and Sensitive Parameters may only be referenced by Sensitive Properties. I understand basic auth and WS-Security are different types of security. I do not see how to build/populate the security header using my value from the parameter context. Any help would be appreciated. Thank you!
Created 03-08-2022 02:31 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @mr_jahurley ,
NiFi does not allow the use of sensitive parameters in non-sensitive context to avoid leaking of sensitive information into other parts of your flow, including flowfile contents. If this was possible, you could, for example, inject a sensitive value into a flowfile and anyone with access to a flowfile would be able to see the sensitive values, which would be otherwise encrypted in NiFi.
If that's really what you want/need, I can only see two available solutions:
- Create a non-sensitive property to store the password, and you would be able to use it in the ReplaceText processor. This is less secure, but no less secure than having the password in a flowfile content. So, I guess, to do what you want to do, this could be a viable alternative.
- Alternatively, you can create your own processor with a sensitive password property where you would be able to use the sensitive parameter. This processor could then take the sensitive value and modify the flowfile content as needed. Notice, though, that after being processed by this processor, the flowfile would contain the password in plain text, so anyone inspecting the flowfile after that would be able to see that. In that sense, this is still somewhat insecure since that password could be leaked. But again, it may be a necessary evil for what you need to implement.
Hope this helps,
André
--
Was your question answered? Make sure to mark the answer as the accepted solution.
If you find a reply useful, say thanks by clicking on the thumbs up button.
Was your question answered? Please take some time to click on "Accept as Solution" below this post.
If you find a reply useful, say thanks by clicking on the thumbs up button.
Created 03-08-2022 02:31 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @mr_jahurley ,
NiFi does not allow the use of sensitive parameters in non-sensitive context to avoid leaking of sensitive information into other parts of your flow, including flowfile contents. If this was possible, you could, for example, inject a sensitive value into a flowfile and anyone with access to a flowfile would be able to see the sensitive values, which would be otherwise encrypted in NiFi.
If that's really what you want/need, I can only see two available solutions:
- Create a non-sensitive property to store the password, and you would be able to use it in the ReplaceText processor. This is less secure, but no less secure than having the password in a flowfile content. So, I guess, to do what you want to do, this could be a viable alternative.
- Alternatively, you can create your own processor with a sensitive password property where you would be able to use the sensitive parameter. This processor could then take the sensitive value and modify the flowfile content as needed. Notice, though, that after being processed by this processor, the flowfile would contain the password in plain text, so anyone inspecting the flowfile after that would be able to see that. In that sense, this is still somewhat insecure since that password could be leaked. But again, it may be a necessary evil for what you need to implement.
Hope this helps,
André
--
Was your question answered? Make sure to mark the answer as the accepted solution.
If you find a reply useful, say thanks by clicking on the thumbs up button.
Was your question answered? Please take some time to click on "Accept as Solution" below this post.
If you find a reply useful, say thanks by clicking on the thumbs up button.
Created on 03-08-2022 05:25 AM - edited 03-08-2022 05:38 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, Thank you for your response. That is helpful. But it turns out I am not allowed to mark the pwd context Parameter as non-sensitive for the reasons you outlined. It sounds like to use the context parameter to call a soap service secured by WS Security I must create a custom processor. I want to ask if you know of any other possible solutions to call the service without compromising the security. Thank you!
Created 03-08-2022 12:28 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @mr_jahurley ,
Unfortunately, I can't think of any other option apart from creating a processor that that makes the call directly to the SOAP service.
Cheers,
André
--
Was your question answered? Make sure to mark the answer as the accepted solution.
If you find a reply useful, say thanks by clicking on the thumbs up button.
Was your question answered? Please take some time to click on "Accept as Solution" below this post.
If you find a reply useful, say thanks by clicking on the thumbs up button.