Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: ambari-server sync-ldap: Exiting with exit co...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ambari-server sync-ldap: Exiting with exit code 1
- Labels:
-
Apache Ambari
Created 05-08-2018 10:49 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I have created Hortonworks Data cloud cluster on AWS, with one master node and one worker node. on master node I have configured the openLDAP server. Now, I am trying to sync openLDAP users with Ambari.
To sync the openLDAP user with Ambari execute the following command:
ambari-server sync-ldap --users users.txt
user.txt contains the name of the user to sync, seprated by comma.
After executing above command it prompts for ambari login. after I enter credential for ambari server it throws following error:
ERROR: Exiting with exit code 1. REASON: Caught exception running LDAP sync. [LDAP: error code 49 - Invalid Credentials]; nested exception is javax.naming.AuthenticationException: [LDAP: error code 49 - Invalid Credentials]
How can I resolve this error ?
Thank You.
Created 05-09-2018 10:18 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
while configuring ambari by running ambari-server setup-ldap, set the value of Bind anonymously* = true. Now, I can see all the LDAP users in Ambari.
Thank You.
Created 05-08-2018 11:31 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The issue is caused by the invalid credentials Ambari/LDAP Admin [user&passwords]
Note
To perform this operation, your Ambari Server must be running.
- When prompted, you must provide credentials for an Ambari Admin.
- When syncing ldap, Local user accounts with matching username will switch to LDAP type, which means their authentication will be against the external LDAP and not against the Local Ambari user store.
Hope that helps
Created 05-08-2018 11:35 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Geoffrey Shelton Okot I am using the same credential to login the ambari UI and it works perfect. But when I am using them with the ambari-server sync-ldap command it throws an error.
Created 05-08-2018 12:29 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's correct because you are trying to sync LDAP user but giving Ambari admin password hence "Invalid credentials" ,here you need your LDAP admin user and password !!!
You will first need to generate the LDAP config file by running
Step 1
ambari-server setup-ldap
It will prompt you for various parameter's like LDAP admin user and password and LDAP host FQDN and port
Step 2
Then the below command actually sync's
ambari-server sync-ldap [option]
The options can be
- --existing
- --all
- --users users.txt --groups groups.txt
See reference
Configuring Ambari for LDAP or Active Directory Authentication
Hope that helps
Created on 05-08-2018 01:09 PM - edited 08-18-2019 12:59 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
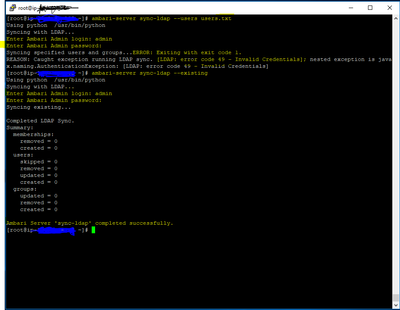
I have already configured LDAP using ambari-server setup-ldap. when I execute the ambari-server sync-ldap --users user.txt it prompts for ambari credentials not LDAP. when I execute ambari-server sync-ldap --existing, I entered the same ambari credentials, and it worked fine. You can check in below attached image.
Created 05-08-2018 01:13 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry maybe misunderstood you,I didn't see the creenshot.
Created 05-08-2018 01:15 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Created 05-08-2018 01:19 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From the above, your LDAP config pulls no data (users/groups) from the server so that means you have a problem with you ldapsearch function
What entries were added to your /etc/ambari-server/conf/ambari.properties can you compare it with the backup if you took one. such as
authentication.ldap.baseDn= authentication.ldap.managerDn= authentication.ldap.primaryUrl= authentication.ldap.bindAnonymously= authentication.ldap.dnAttribute= authentication.ldap.groupMembershipAttr= authentication.ldap.groupNamingAttr= authentication.ldap.groupObjectClass= authentication.ldap.useSSL= authentication.ldap.userObjectClass= authentication.ldap.usernameAttribute=
These are AD-related but should be similar
Created 05-08-2018 01:28 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
following are the entries in ambari.properties:
authentication.ldap.baseDn=dc=hadoop,dc=com
authentication.ldap.bindAnonymously=false
authentication.ldap.dnAttribute=dn
authentication.ldap.groupMembershipAttr=gidNumber
authentication.ldap.groupNamingAttr=cn
authentication.ldap.groupObjectClass=posixGroup
authentication.ldap.managerDn=cn=Manager,dc=hadoop,dc=com
authentication.ldap.managerPassword=/etc/ambari-server/conf/ldap-password.dat
authentication.ldap.primaryUrl=ip-00-0-00-000.ec2.internal:389
authentication.ldap.useSSL=false
authentication.ldap.userObjectClass=inetOrgPerson authentication.ldap.usernameAttribute=uid
Created 05-08-2018 02:36 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your sync process failed!
If you do not know the root entry of the LDAP server you are connecting to, you can query a special "meta" entry outside of the normal LDAP DIT for information about what DIT root entries it knows about
ldapsearch -H ldap://server_domain_or_IP -x -LLL -s base -b "" namingContexts
The admin entry typically uses the simpleSecurityObject objectClass in order to gain the ability to set a password in the entry. You can use this to search for entry with this class:
ldapsearch -H ldap://server_domain_or_IP -x -LLL -b "dc=example,dc=com" "(objectClass=simpleSecurityObject)" dn
This will give you a list of the entries that use this class. Usually there is only one
Performing the Bind
Once you have an entry and password, you can perform a simple bind during your request to authenticate yourself to the LDAP server.
ldapsearch -H ldap://server_domain_or_IP -x -D "cn=admin,dc=example,dc=com" -W
You should get the same result as our anonymous bind, indicating that our credentials were accepted.
Rerun the Ambari ldap setup
Use value obtained from above
ambari-server setup-ldap
You should have users and groups now pulled from the LDAP
Then run ldap sync
ambari-server sync-ldap --existing
Your users should now be visible in Ambari and if you enabled ranger usersync then your user should be available in Ranger too !!!