Community Articles
- Cloudera Community
- Support
- Community Articles
- How to enable user impersonation for SH interprete...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on 02-02-2017 07:37 AM - edited 08-17-2019 05:15 AM
OVERVIEW
This facility is available in Zeppelin 0.7.0 based on the JIRA: https://issues.apache.org/jira/browse/ZEPPELIN-1320. The below steps allow you to get this working in HDP 2.5 environment with Zeppelin 0.6.
ENVIRONMENT and SETUP
I did test the below solution with
- HDP 2.5.0.0-1245
- Ambari 2.4.0.1
Shiro.ini
[users] # List of users with their password allowed to access Zeppelin. # To use a different strategy (LDAP / Database / ...) check the shiro doc at http://shiro.apache.org/configuration.html#Configuration-INISections admin = password user1 = password, role1, role2 user2 = password, role3 #user3 = password4, role2 # Sample LDAP configuration, for user Authentication, currently tested for single Realm [main] #activeDirectoryRealm = org.apache.zeppelin.server.ActiveDirectoryGroupRealm #activeDirectoryRealm.systemUsername = CN=Administrator,CN=Users,DC=HW,DC=EXAMPLE,DC=COM #activeDirectoryRealm.systemPassword = Password1! #activeDirectoryRealm.hadoopSecurityCredentialPath = jceks://user/zeppelin/zeppelin.jceks #activeDirectoryRealm.searchBase = CN=Users,DC=HW,DC=TEST,DC=COM #activeDirectoryRealm.url = ldap://ad-nano.test.example.com:389 #activeDirectoryRealm.groupRolesMap = "" #activeDirectoryRealm.authorizationCachingEnabled = true #ldapRealm = org.apache.shiro.realm.ldap.JndiLdapRealm #ldapRealm.userDnTemplate = uid={0},cn=users,cn=accounts,dc=example,dc=com #ldapRealm.contextFactory.url = ldap://ldaphost:389 #ldapRealm.contextFactory.authenticationMechanism = SIMPLE #sessionManager = org.apache.shiro.web.session.mgt.DefaultWebSessionManager #securityManager.sessionManager = $sessionManager # 86,400,000 milliseconds = 24 hour #securityManager.sessionManager.globalSessionTimeout = 86400000 shiro.loginUrl = /api/login [urls] # anon means the access is anonymous. # authcBasic means Basic Auth Security # To enfore security, comment the line below and uncomment the next one #/api/version = anon #/** = anon #/** = authc /** = authcBasic
PROBLEM
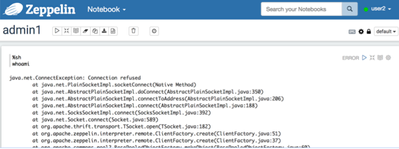
In the current version of Zeppelin, enabling “User Impersonate” in SH interpreter causing the connection refused error
SOLUTION
To get “user2” get working with SH interpreter, follow up the below steps:
1. Log into Zeppelin node as ROOT and create a “user2” user:
[root@dkhdp251 ~]# adduser user2 [root@dkhdp251 ~]# passwd user2 Changing password for user user2. New password: BAD PASSWORD: it is based on a dictionary word Retype new password: passwd: all authentication tokens updated successfully. [root@dkhdp251 ~]#
2. Log in to Zeppelin node as zeppelin user to set the passwordless authentication for “user2”:
[root@dkhdp251 ~]# su - zeppelin [zeppelin@dkhdp251 ~]$ ssh-keygen (this is to be run only once for all the users) Generating public/private rsa key pair. Enter file in which to save the key (/home/zeppelin/.ssh/id_rsa): /home/zeppelin/.ssh/id_rsa already exists. Overwrite (y/n)? n (As I already have keygen generated, I skipped this step for presentation) [zeppelin@dkhdp251 ~]$ ssh user2@dkhdp251.dk mkdir -p .ssh user2@dkhdp251.dk's password: [zeppelin@dkhdp251 ~]$ [zeppelin@dkhdp251 ~]$ [zeppelin@dkhdp251 ~]$ cat ~/.ssh/id_rsa.pub | ssh user2@dkhdp251.dk 'cat >> .ssh/authorized_keys' user2@dkhdp251.dk's password: [zeppelin@dkhdp251 ~]$ [zeppelin@dkhdp251 ~]$ [zeppelin@dkhdp251 ~]$ ssh user2@dkhdp251.dk "chmod 700 .ssh; chmod 640 .ssh/authorized_keys" user2@dkhdp251.dk's password: [zeppelin@dkhdp251 ~]$ [zeppelin@dkhdp251 ~]$ [zeppelin@dkhdp251 ~]$ ssh user2@dkhdp251.dk [user2@dkhdp251 ~]$ [user2@dkhdp251 ~]$ [user2@dkhdp251 ~]$ exit logout Connection to dkhdp251.dk closed. [zeppelin@dkhdp251 ~]$ [zeppelin@dkhdp251 ~]$ [zeppelin@dkhdp251 ~]$ ssh user2@localhost Last login: Thu Feb 2 06:37:26 2017 from 172.26.81.190 [user2@dkhdp251 ~]$
3. Log in to Zeppelin UI
a) first, log in as the user with access to interpreters
- go to Interpreters
- edit SH interpreter
- enable “User Impersonate”
- save the changes
- restart SH interpreter
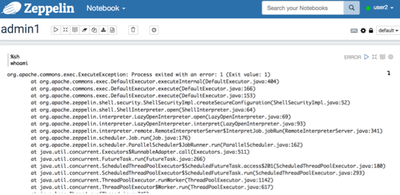
b) log in as “user2” and run script from notebook
Due to this error the “user2” does not have a right permission accessing zeppelin keytab. For now, do the following:
- go to Interpreter
- edit SH interpreter
- remove the following properties:
zeppelin.shell.auth.type zeppelin.shell.keytab.location zeppelin.shell.principal
- save the changes
- restart interpreter
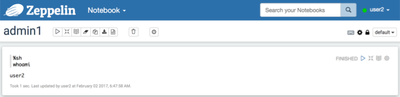
So, the SH interpreter looks like this
Now when running the sh code as “user2”
NOTE:
Restarting Zeppelin will add the above removed properties back to SH interpreter. To get around it:
- log in as ROOT to zeppelin node
$ ls -lrt /etc/security/keytabs/zeppelin.server.kerberos.keytab (this will tell you the <GROUP>) $ usermod -a -G <GROUP> user2 (add the user to zeppelin’s keytab group) $ chmod 440 /etc/security/keytabs/zeppelin.server.kerberos.keytab (make sure the above keytab has a read permission for groups (440))
- Restart SH interpreter