Community Articles
- Cloudera Community
- Support
- Community Articles
- How to setup OpenLDAP 2.4 on CentOS 7
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on 01-25-2017 07:35 PM - edited 09-16-2022 01:38 AM
OpenLDAP is an open-source implementation of the Lightweight Directory Access Protocol and is used for central management of accounts (users, hosts, and services) and can be used in concert with a KDC to provide authentication within the Hadoop ecosystem. Fundamentally, LDAP functions like a database in many ways and can be used to store any information.
We will assume that you have a fresh CentOS 7 host available that will host OpenLDAP. Make sure you have network connectivity between any clients and this server and that DNS resolution is working. Let's ssh to the host, and install, as root, the packages we need with yum:
yum -y install openldap compat-openldap openldap-clients openldap-servers openldap-servers-sql openldap-devel
We'll also start the LDAP daemon (called slapd) and enable it to auto-start on system boot:
systemctl start slapd.service systemctl enable slapd.service
Next, run the slappasswd command to create an LDAP root password. Please take note of this root password, the entire hashed value that is returned as output and starts {SSHA}, as you'll use it throughout this article.
We'll now configure the OpenLDAP server in a couple of steps. We'll create LDIF text files and then use the ldapmodify command to push the configuration to the server. These will ultimately land in /etc/openldap/slapd.d but the files shouldn't be edited manually.
The first file will update the variables for olcSuffix, the domain name for which your server LDAP server provides account information, and olcRootDN, the root distinguished name (DN) user who has unrestricted administrative access. My domain is field.hortonworks.com, or dc=field,dc=hortonworks,dc=com and my root DN is cn=ldapadm,dc=field,dc=hortonworks,dc=com.
Create the following db.ldif file using vi or your favorite editor.
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=field,dc=hortonworks,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootDN
olcRootDN: cn=ldapadm,dc=field,dc=hortonworks,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootPW
olcRootPW: {SSHA}theHashedPasswordValueFromSlapPasswd
We'll then push this config:
ldapmodify -Y EXTERNAL -H ldapi:/// -f db.ldif
We'll next restrict monitor access to the ldapadm user:
dn: olcDatabase={1}monitor,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external, cn=auth" read by dn.base="cn=ldapadm,dc=field,dc=hortonworks,dc=com" read by * noneAnd push that config change:
ldapmodify -Y EXTERNAL -H ldapi:/// -f monitor.ldif
In order to communicate securely with the OpenLDAP server, we'll need a certificate and associated private key. These would likely be obtained from our PKI Administrator in a production environment, but a self-signed certificate and associated private key can be created in development environments, using a command like below:
openssl req -new -x509 -nodes -out /etc/openldap/certs/myldap.field.hortonworks.com.cert -keyout /etc/openldap/certs/myldap.field.hortonworks.com.key -days 365
Set the owner and group permissions to ldap:ldap for both files.
We'll then create certs.ldif to configure OpenLDAP for secure communication over LDAPS:
dn: cn=config changetype: modify replace: olcTLSCertificateFile olcTLSCertificateFile: /etc/openldap/certs/myldap.field.hortonworks.com.cert dn: cn=config changetype: modify replace: olcTLSCertificateKeyFile olcTLSCertificateKeyFile: /etc/openldap/certs/myldap.field.hortonworks.com.key
We can then push the config file and finally test the configuration:
ldapmodify -Y EXTERNAL -H ldapi:/// -f certs.ldif slaptest -u
We're now ready to set up the initial LDAP database:
First, copy the sample database configuration file to /var/lib/ldap and update the file permissions.
cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG chown ldap:ldap /var/lib/ldap/*
Next, add the cosine and nis LDAP schemas.
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
Finally, generate base.ldif file for your domain.
dn: dc=field,dc=hortonworks,dc=com dc: field objectClass: top objectClass: domain dn: cn=ldapadm,dc=field,dc=hortonworks,dc=com objectClass: organizationalRole cn: ldapadm description: LDAP Manager dn: ou=People,dc=field,dc=hortonworks,dc=com objectClass: organizationalUnit ou: People dn: ou=Group,dc=field,dc=hortonworks,dc=com objectClass: organizationalUnit ou: Group
We'll now push these changes to OpenLDAP using the ldapadm user (sometimes referred to as the bind user):
ldapadd -x -W -D "cn=ldapadm,dc=field,dc=hortonworks,dc=com" -f base.ldif
You'll be prompted for the root password.
From here, I prefer to use a GUI to create additional users. Apache Directory Studio is a nice multi-platform tool and can be downloaded here.
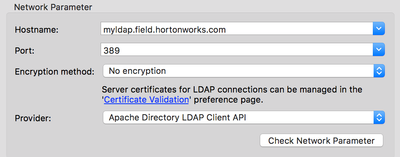
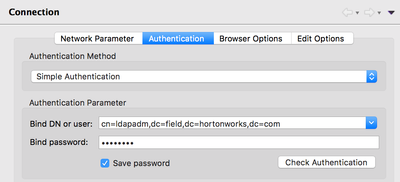
Within Apache Directory Studio, you can create a new connection in the lower left-hand pane and use the following configuration:
With the following authentication information:
Once you connect successfully you can create your organizational structure and users accordingly.
These steps are based on the valuable tutorial provided here.
Created on 04-29-2017 02:32 AM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello, I want to thank you for this very good tutotiel, I encounter a problem at the end, I can not connect with Apache DS. That put me "connection refused", I checked and I think it is a port problem. Port 389 is not open on my hortonworks exit interface. Have you had this problem? If yes, how did you resolve it? thank you in advance
Created on 04-10-2018 05:17 AM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
Its very informative and helpful.
I guess you just missed to add "ldaps:///" in SLAPD_URLS configuration in file "/etc/sysconfig/slapd".
Created on 08-15-2022 06:49 AM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
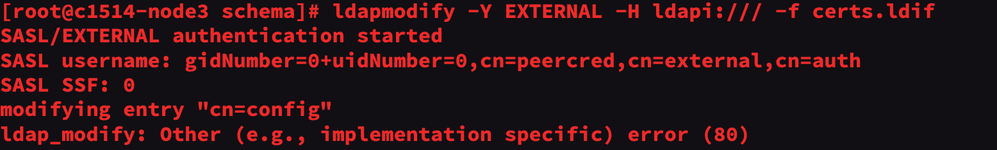
- olcTLSCACertificateFile,
- olcTLSCertificateKeyFile,
- olcTLSCertificateFile.