Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: How to enable User Authentication with Kerbero...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to enable User Authentication with Kerberos in nifi 1.x
- Labels:
-
Apache NiFi
Created 08-31-2016 08:36 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is a page to enable User Authentication with Kerberos step by step for nifi 0.x
But nifi 1.x change the conf. I follow parts of steps as above, and then login with username/password . But I get following message:
"Unable to perform the desired action due to insufficient permissions. Contact the system administrator."
(it seem that the username/password has been authed by kerberos )
How to resolve? Thanks for you reply.
@Jobin George: please update your article. Thanks very much.
Created on 08-31-2016 12:23 PM - edited 08-19-2019 02:49 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
NiFi 1.x (HDF 2.x) versions have gone through a major framework upgrade/change. A multi-tenancy approach has been added that allows users to control the access of users down to the component level. As part of this change, the way the initial admin user is added has changed. In previous NiFi 0.x (HDF 1.x) versions, this was simply done by adding the DN of your first admin user to the authorized-users.xml file. In NiFi 1.x (HDF 2.x) versions you need to set that user DN in the following property in the authorizers.xml file:
<property name="Initial Admin Identity"></property>
For those who previously worked with NiFi 0.x (HDF 1.x) versions, you can use an old authorized-users.xml file to seed the new NiFi version's user authorization by setting this property in the same file:
<property name="Legacy Authorized Users File"></property>
NiFi 1.x (HDF 2.x) version no longer provide new users the ability to "request access". An Admin will need to manually added each users and assign them component level access through the UI.
adding new users is done through the users UI found in the hamburger menu in the upper right corner of the UI. (Remember this can only be done once initial admin as given access as described above).
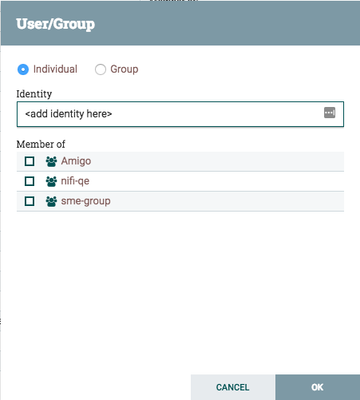
From the Users UI, select the add user icon in the upper right corner 
The above UI will appear to add your new users. Supply your kerberos, LDAP, or certificate DN and click "OK"
Now that you have added a user you need grant them component level access back on the main NiFi UI.
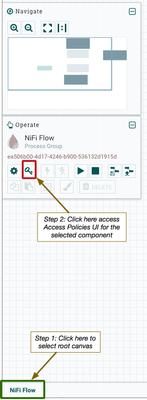
Select the component you which to control access to. In the below example we will select the root canvas:
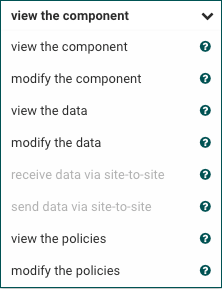
A new "Access Policies" Ui will appear where you need select the access policy you want to add the user to from the pull down menu:
Once you select Policy, click on the add user icon in the upper right to grant access to one of the users added earlier.
Thanks,
Matt
Created 08-31-2016 12:00 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In NiFi 1.0 the configuration was separated into a principal/keytab that NiFi uses to talk to other services vs. a principal/keytab used for authenticating users. For authenticating users you would need to populate these two properties:
| nifi.kerberos.spnego.principal* | The name of the NiFi Kerberos service principal, if used. It is blank by default. Note that this property is used to authenticate NiFi users. Example: HTTP/nifi.example.comor HTTP/nifi.example.com@EXAMPLE.COM |
| nifi.kerberos.spnego.keytab.location* | The file path of the NiFi Kerberos keytab, if used. It is blank by default. Note that this property is used to authenticate NiFi users. Example: /etc/http-nifi.keytab |
In step 5 of that article, there is no more authorized-users.xml... you should put the identity of the initial admin user into conf/authorizers.xml. The identity would be kerberos principal you are going to login as. When NiFi starts and sees the initial admin, it will generate permissions for that user giving access to the UI.
Created 09-01-2016 08:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much. It work.
Created 12-08-2016 06:38 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi,Bryan
I changed the two properties in conf/nifi.properties, and put the identity of the initial admin user into conf/authorizers.xml. but I still got the same issue like @David DN ,‘Demo’ user is NiFi Administrator got nothing.
Created on 08-31-2016 12:23 PM - edited 08-19-2019 02:49 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
NiFi 1.x (HDF 2.x) versions have gone through a major framework upgrade/change. A multi-tenancy approach has been added that allows users to control the access of users down to the component level. As part of this change, the way the initial admin user is added has changed. In previous NiFi 0.x (HDF 1.x) versions, this was simply done by adding the DN of your first admin user to the authorized-users.xml file. In NiFi 1.x (HDF 2.x) versions you need to set that user DN in the following property in the authorizers.xml file:
<property name="Initial Admin Identity"></property>
For those who previously worked with NiFi 0.x (HDF 1.x) versions, you can use an old authorized-users.xml file to seed the new NiFi version's user authorization by setting this property in the same file:
<property name="Legacy Authorized Users File"></property>
NiFi 1.x (HDF 2.x) version no longer provide new users the ability to "request access". An Admin will need to manually added each users and assign them component level access through the UI.
adding new users is done through the users UI found in the hamburger menu in the upper right corner of the UI. (Remember this can only be done once initial admin as given access as described above).
From the Users UI, select the add user icon in the upper right corner 
The above UI will appear to add your new users. Supply your kerberos, LDAP, or certificate DN and click "OK"
Now that you have added a user you need grant them component level access back on the main NiFi UI.
Select the component you which to control access to. In the below example we will select the root canvas:
A new "Access Policies" Ui will appear where you need select the access policy you want to add the user to from the pull down menu:
Once you select Policy, click on the add user icon in the upper right to grant access to one of the users added earlier.
Thanks,
Matt
Created 09-01-2016 08:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much. It work.
Created 12-08-2016 02:22 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I hava added new user as what @Matt said , but I don't know how get login with the new user?
Created 12-08-2016 01:16 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I need more detail on what you are seeing. There are two parts to accessing a secured NiFi installation, Authentication and authorization.
Authentication by default expects users to authenticate using SSL. A user would need to present a valid certificate via their browser to NiFi for authentication. NiFi can also be configured via the login-identity.providers.xml file to support either LDAP or Kerberos for users authentication.
After a user successfully authenticates, the authorization piece occurs. The above answer deals with the authorization piece only.
Check you nifi-user.log to see if authentication is successful. make sure the DN shown in the nifi-users.log matches exactly (case sensitive and whitespace issues?) what is configured in the "Initial Admin Identity" property in your authorizers.xml file.
When nifi is started for the first time after enabling https the users.xml and authorizations.xml files are generated based on the user supplied configurations in the authorizers.xml file. Should the configurations in the authorizers.xml get edited at a later time, those changes will not be made to the existing users.xml or authorizations.xml files. They are only ever created once, subsequent edits to these files are expected to be done via the NiFi application.
If you made a mistake in these files when setting up https access for the first time, you can remove these two files and they we be re-created next time you start NiFi.
Thanks,
Matt
Created 12-09-2016 01:19 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks,Matt!
this page to enable User Authentication with Kerberos step by step for nifi 0.x
But nifi 1.x change the conf. I follow parts of steps as above, and then login with username/password . But I get following message:
"Unable to perform the desired action due to insufficient permissions. Contact the system administrator."
then I add username (same as created in kerberos) in nifi as you said. give the right to the users added earlier. after that, I still get the same problem. "Unable to perform the desired action due to insufficient permissions. Contact the system administrator."
Created 12-09-2016 02:10 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@pholien feng
before a user can access the UI, that user must have the "view the interface" policy granted for them. This policy is added through the global policies UI found under the hamburger menu located in the upper right corner. I see that step is missing in the above answer. Sorry about that.
Matt