Support Questions
- Cloudera Community
- Support
- Support Questions
- Re: NiFi Authentication with LDAP
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NiFi Authentication with LDAP
- Labels:
-
Apache NiFi
-
Security
Created on 07-07-2020 07:14 AM - edited 07-07-2020 08:07 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
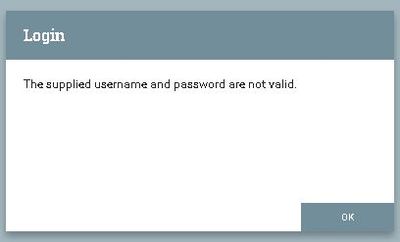
I am trying to secure NiFi using LDAP configuration. I followed blog by mintops and pvillard articles for reference. I am running NiFi on windows (not in cluster configuration). I am able to get to the login screen, but then I am getting an error on logging in ( The supplied username and password are invalid)
I followed most instructions as mentioned in the blog by mintops. Can someone help me in the direction, on what might be the problem?
PS: NiFi version and toolkit versions -1.8.0.
I haven't created certificates, just the configs needed to update in Keystore and truststore passwords by the toolkit.
The LDAP configurations were already being used in another program, so that is also not the issue.
login-identity-provider.xml
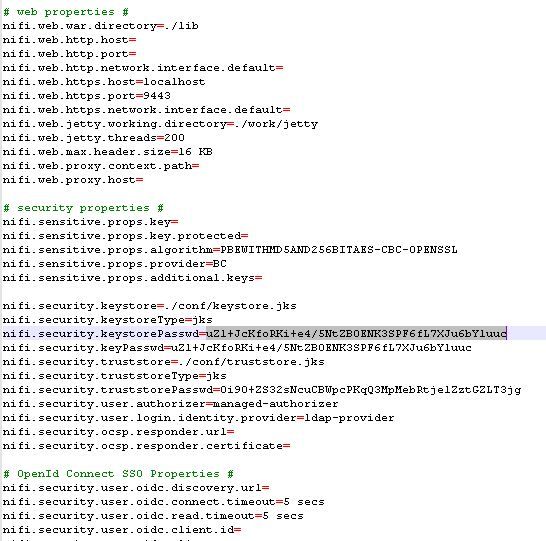
nifi.properties
Created 07-08-2020 06:09 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The error you are seeing has nothing to do with authorization at this point. It is throwing an error during authentication of your user. So your focus at this point is on your ldap-provider configuration since it is handling the authentication of your user.
"The Supplied Username or Password are not valid" indicates that the LDAP search resulted in no returns or the password used was wrong.
Observations:
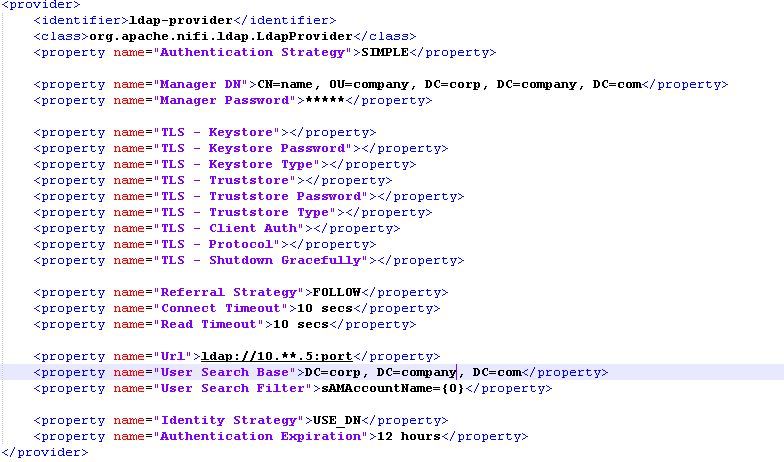
1. Are you using ldap or Active Directory (AD). I see you have set "User Search Filter" to "sAMAccountName={0}". sAMAccountName is more commonly seen in AD and not LDAP. Did you try using the ldapsearch command from a terminal window on your NiFI server to make sure you can return a listing for your user using this search filter?
ldapsearch -x -H ldap://<ldap-hostname/IP>:<ldap-port> -D "<Manager DN>" -w "<Manager password>" -b "<user search base>" "sAMAccountName=<username>"
2. Not that this has anything to do with successful authentication, but I see you have set "Identity Strategy" to "USE_DN" which then uses the users full DN from ldap to identify that user during authorization actions following successful authorization. If you set this to "USE_USERNAME", the user string type at login will be used.
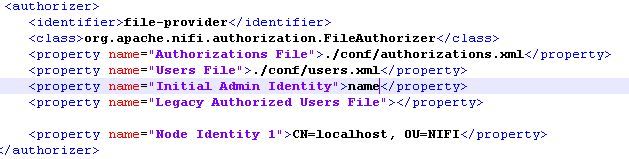
3. Also has nothing to do with authentication, but I see you are using "CN=localhost, OU=NiFi" as your "node identity 1" value. Using localhost in your node certificates is not advisable. This should be set to unique value. Also keep in mind that the keystore used by NiFi must meet the following minimum requirements:
- Contain only 1 "PrivateKeyEntry"
- The "PrivateKeyEntry" must support both clientAuth and serverAuth ExtendedKeyUsage (EKU).
- The "PrivateKeyEntry" must contain at least 1 SubjectAlternativeName (SAN) that matches the hostname of the server on which the certificate is being used.
Hope this information helps you progress with your authentication and then authorization setup in NiFi.
Matt
Created 07-08-2020 06:09 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The error you are seeing has nothing to do with authorization at this point. It is throwing an error during authentication of your user. So your focus at this point is on your ldap-provider configuration since it is handling the authentication of your user.
"The Supplied Username or Password are not valid" indicates that the LDAP search resulted in no returns or the password used was wrong.
Observations:
1. Are you using ldap or Active Directory (AD). I see you have set "User Search Filter" to "sAMAccountName={0}". sAMAccountName is more commonly seen in AD and not LDAP. Did you try using the ldapsearch command from a terminal window on your NiFI server to make sure you can return a listing for your user using this search filter?
ldapsearch -x -H ldap://<ldap-hostname/IP>:<ldap-port> -D "<Manager DN>" -w "<Manager password>" -b "<user search base>" "sAMAccountName=<username>"
2. Not that this has anything to do with successful authentication, but I see you have set "Identity Strategy" to "USE_DN" which then uses the users full DN from ldap to identify that user during authorization actions following successful authorization. If you set this to "USE_USERNAME", the user string type at login will be used.
3. Also has nothing to do with authentication, but I see you are using "CN=localhost, OU=NiFi" as your "node identity 1" value. Using localhost in your node certificates is not advisable. This should be set to unique value. Also keep in mind that the keystore used by NiFi must meet the following minimum requirements:
- Contain only 1 "PrivateKeyEntry"
- The "PrivateKeyEntry" must support both clientAuth and serverAuth ExtendedKeyUsage (EKU).
- The "PrivateKeyEntry" must contain at least 1 SubjectAlternativeName (SAN) that matches the hostname of the server on which the certificate is being used.
Hope this information helps you progress with your authentication and then authorization setup in NiFi.
Matt
Created 07-10-2020 12:03 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, you were spot-on about the issue, turned out the creds provided to me were incorrect. And thanks for the suggestions as well.
Created 09-20-2022 08:32 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
where location crods previded ?