Support Questions
- Cloudera Community
- Support
- Support Questions
- Setting StandardSSLContext service for listenTCP
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Setting StandardSSLContext service for listenTCP
- Labels:
-
Apache NiFi
Created on 11-07-2017 09:52 PM - edited 08-18-2019 12:28 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
Thanks a lot to this aweosme community.
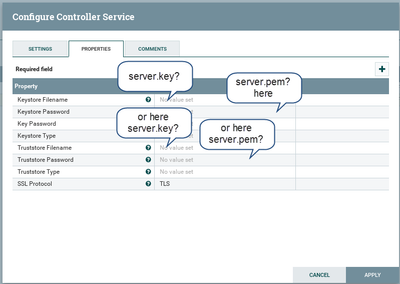
I am trying to set server.key and server.pem store in some directory on my nifi node using StandardSSLcontext service, the type is pkcs12.
Which property will be set here
Keystore properties or
the Truststore ones
I am confused between terminalogies any help
I do not have much idea about keys and certs
Thanks Dheeru
Created 11-08-2017 12:50 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need the private key and public key to be stored in a Java Keystore (*.jks) file. You can import the PEM-encoded certificate and key into this form by using the following commands:
openssl pkcs12 -export -in server.pem -inkey server.key -out server.p12 -name [some-alias] -chain keytool -importkeystore -deststorepass [yourpassword] -destkeypass [yourpassword] -destkeystore server.jks -srckeystore server.p12 -srcstoretype PKCS12 -srcstorepass [passwordfromabove] -alias [some-alias]
When creating the temporary PKCS12 keystore, make sure to provide a password at the prompt, or the Java keytool utility will not accept it. Once you have the server.jks file, populate the properties as follows:
- Keystore file: path/to/server.jks
- Keystore password: [yourpassword]
- Key password: [yourpassword]
- Keystore type: JKS
This will allow your NiFi instance/component to present a server certificate identifying itself and encrypt the channel. However, to connect to external HTTPS services, you will also need to provide a truststore. A truststore is a keystore file that contains only public certificates of other services to allow your system (in this case, NiFi) to trust them. If you have custom organizational certificates, you'll need to build your own truststore here. If you are just connecting to generic internet services, the JRE default should be fine:
- Truststore file: /Library/Java/JavaVirtualMachines/jdk1.8.0_101.jdk/Contents/Home/jre/lib/security/cacerts (your JRE path may be different)
- Truststore password: changeit
- Truststore type: JKS
Created 11-07-2017 10:45 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I read this blog (https://bryanbende.com/development/2017/10/13/apache-nifi-tls-with-apache-solr) by @Bryan Bende and looks
like I need download the
- nifi-toolkit-1.4.0-bin.tar.gz ( asc, md5, sha1, sha256 ) from
https://nifi.apache.org/download.html and make a keystore or truststore or both?
Am I going in the right direction?
Thanks
Dheeru
Created 11-08-2017 12:50 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need the private key and public key to be stored in a Java Keystore (*.jks) file. You can import the PEM-encoded certificate and key into this form by using the following commands:
openssl pkcs12 -export -in server.pem -inkey server.key -out server.p12 -name [some-alias] -chain keytool -importkeystore -deststorepass [yourpassword] -destkeypass [yourpassword] -destkeystore server.jks -srckeystore server.p12 -srcstoretype PKCS12 -srcstorepass [passwordfromabove] -alias [some-alias]
When creating the temporary PKCS12 keystore, make sure to provide a password at the prompt, or the Java keytool utility will not accept it. Once you have the server.jks file, populate the properties as follows:
- Keystore file: path/to/server.jks
- Keystore password: [yourpassword]
- Key password: [yourpassword]
- Keystore type: JKS
This will allow your NiFi instance/component to present a server certificate identifying itself and encrypt the channel. However, to connect to external HTTPS services, you will also need to provide a truststore. A truststore is a keystore file that contains only public certificates of other services to allow your system (in this case, NiFi) to trust them. If you have custom organizational certificates, you'll need to build your own truststore here. If you are just connecting to generic internet services, the JRE default should be fine:
- Truststore file: /Library/Java/JavaVirtualMachines/jdk1.8.0_101.jdk/Contents/Home/jre/lib/security/cacerts (your JRE path may be different)
- Truststore password: changeit
- Truststore type: JKS
Created 11-08-2017 01:31 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks a lot, appreciate it